Introduction
The JS7 - Security Architecture includes the use of JS7 - Identity Services for JS7 - Authentication and JS7 - Authorization.
- Identity Services implement authentication methods and access to Identity Providers. For example, credentials such as user account/password can be used as an authentication method to access an LDAP Directory Service as the Identity Provider.
- The JS7 supports a number of Identity Services:
- Build-in Identity Services
-
FEATURE AVAILABILITY STARTING FROM RELEASE 2.2.0
- JS7 - JOC Identity Service, see JOC-1148 - Getting issue details... STATUS
- JS7 - LDAP Identity Service, see JOC-1147 - Getting issue details... STATUS
FEATURE AVAILABILITY STARTING FROM RELEASE 2.5.0
FEATURE AVAILABILITY STARTING FROM RELEASE 2.6.0
- JS7 - Certificate Identity Service, see JOC-1547 - Getting issue details... STATUS
- JS7 - FIDO Identity Service, see JOC-1546 - Getting issue details... STATUS
-
FEATURE AVAILABILITY STARTING FROM RELEASE 2.2.0
- External Identity Services
-
FEATURE AVAILABILITY STARTING FROM RELEASE 2.2.0
- JS7 - HashiCorp® Vault Identity Service, see JOC-1146 - Getting issue details... STATUS
-
FEATURE AVAILABILITY STARTING FROM RELEASE 2.3.0
- Keycloak®, see JOC-1193 - Getting issue details... STATUS
-
FEATURE AVAILABILITY STARTING FROM RELEASE 2.2.0
- Build-in Identity Services
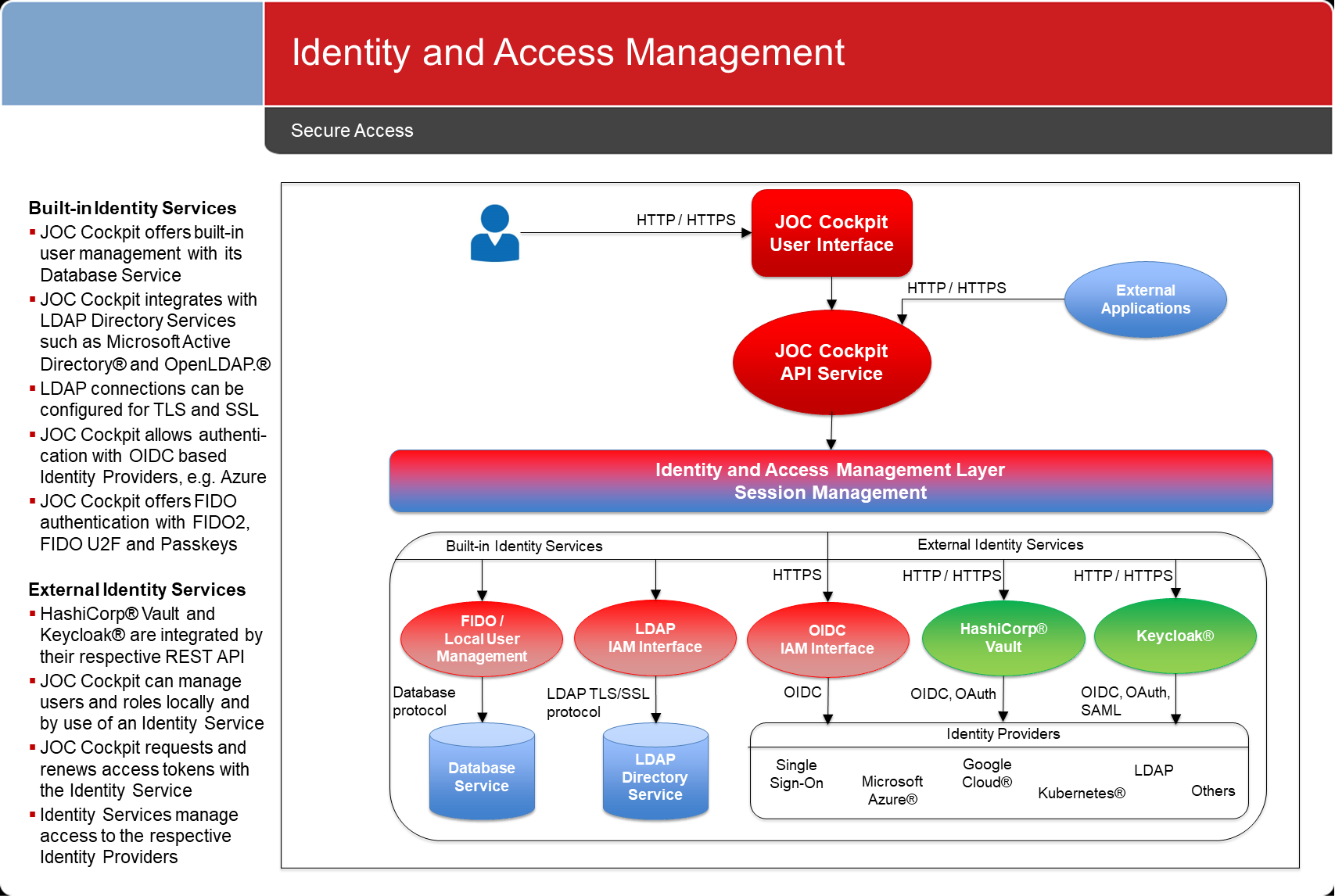
Identity and Access Management
The JOC Cockpit implements an access layer to integrate a number of Identity Services for Identity and Access Management (IAM).
Built-in Identity Services
- Built-in Identity Services ship with the JOC Cockpit and can be used out-of-the-box.
- The JS7 - JOC Identity Service for local user management does not include elaborated features such as password recovery, password complexity constraints, password rotation, etc. and is not intended for such purposes. Instead, this Identity Service is intended as a starting point for users who operate JS7 for testing purposes.
- The JS7 - LDAP Identity Service typically offers such features from an Identity Provider such as Active Directory.
- The JS7 - OIDC Identity Service offers a token based authentication scheme for direct interaction between the user and the Identity Provider.
- The JS7 - Certificate Identity Service works based on Client Authentication certificates that replace passwords.
- The JS7 - FIDO Identity Service offers authentication from use of a secure device.
External Identity Services
- Use of external Identity Services requires that users install and operate the relevant Identity Service product.
- Depending on the nature of the Identity Service, security tokens are used that limit the scope (roles) and lifetime of access to JOC Cockpit.
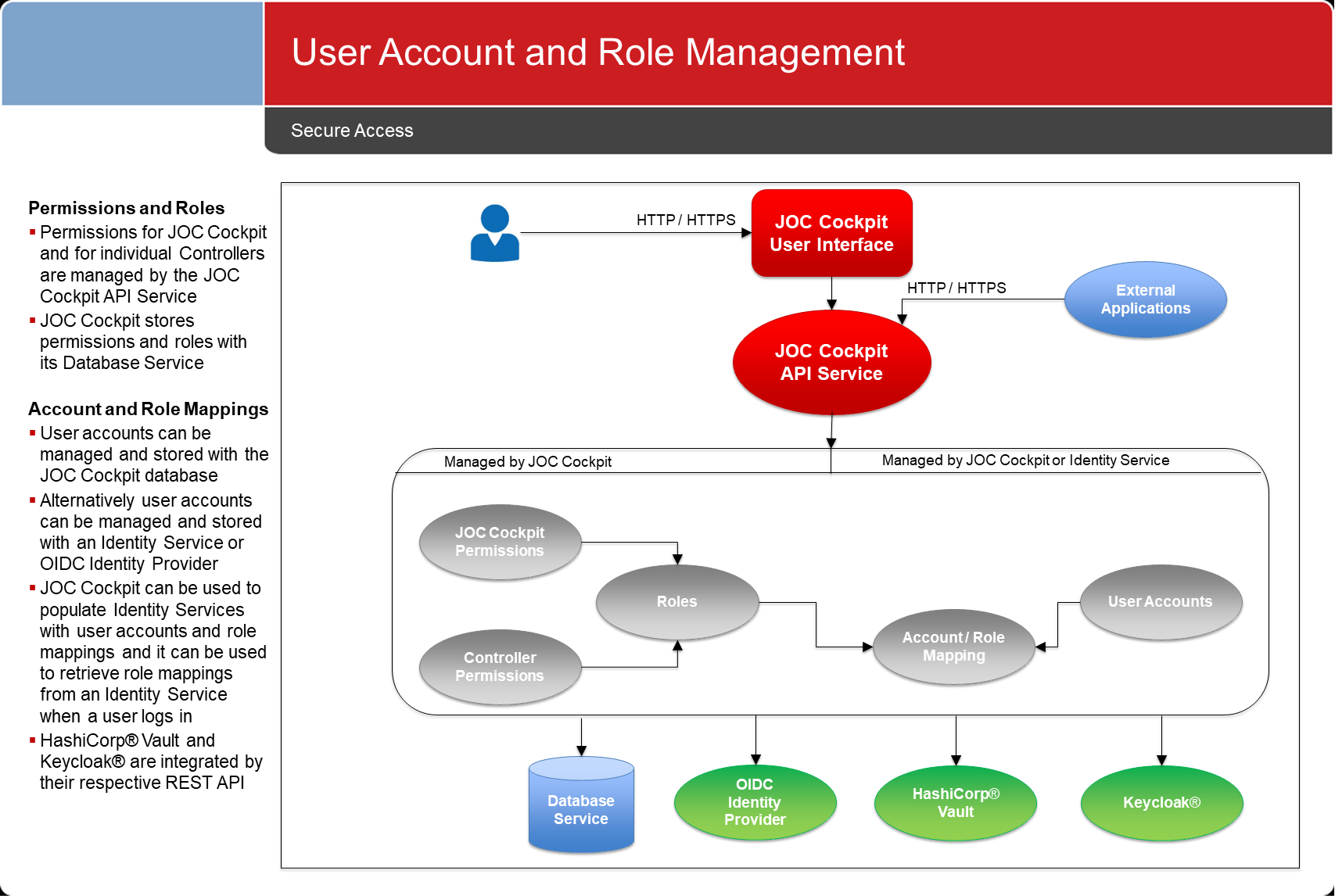
User Account and Role Management
Finely-grained permissions are available for access to JOC Cockpit functions, see the JS7 - Default Roles and Permissions article for detailed information.
Permissions and roles are managed using the JOC Cockpit. User accounts and role assignments can be managed using either the JOC Cockpit Identity Service or external Identity Services. See the JS7 - Management of User Accounts, Roles and Permissions article for more information.
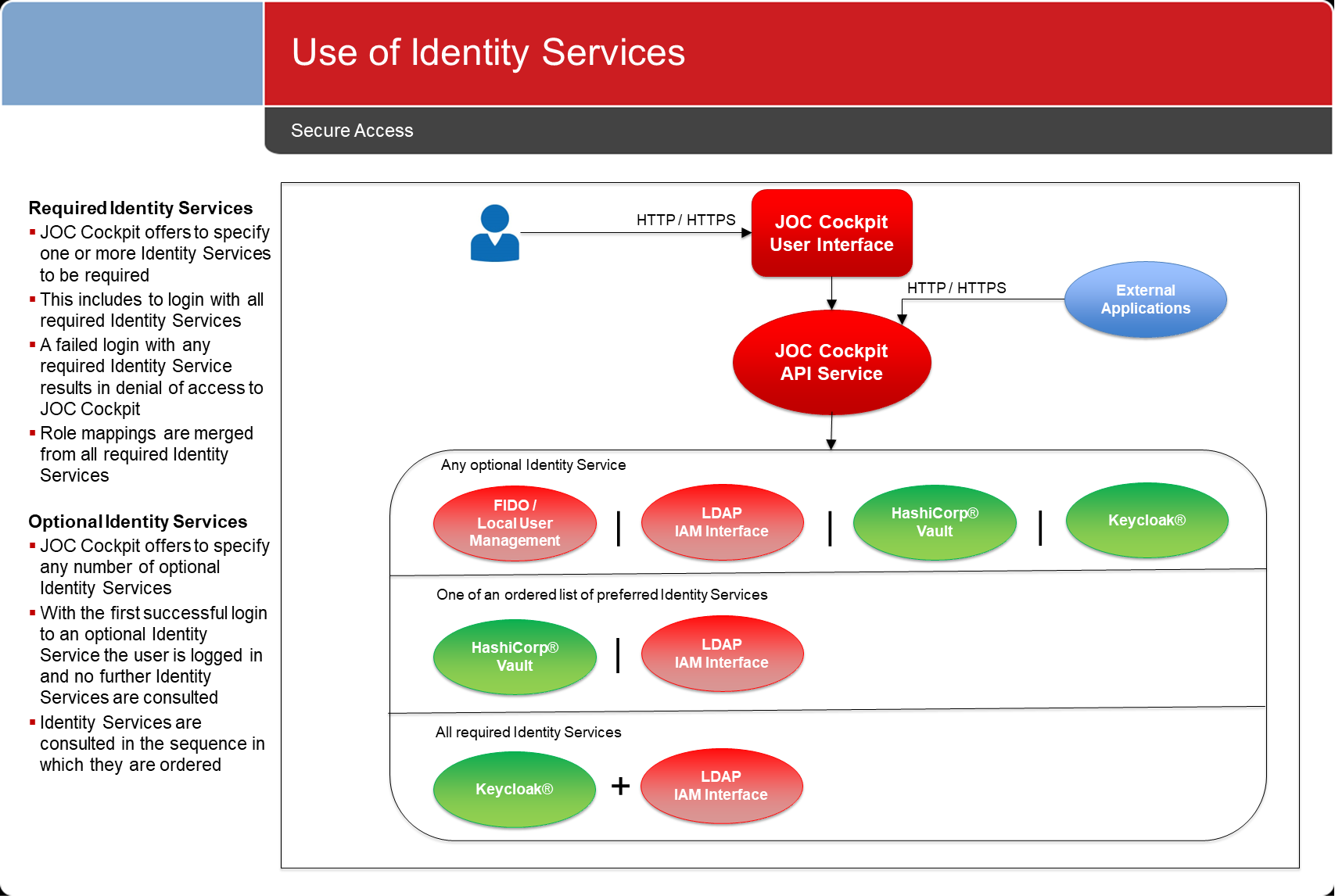
Use of Identity Services
A number of Identity Services can be used at the same time:
- Required Identity Services: user login is performed with all required Identity Services. Optional Identity Services are not considered.
- Optional Identity Services: with the first successful login to an Identity Service the user is considered to have logged in and further Identity Services are not consulted.
Identity Services can be ordered to specify a sequence of preferred or required services for authentication.
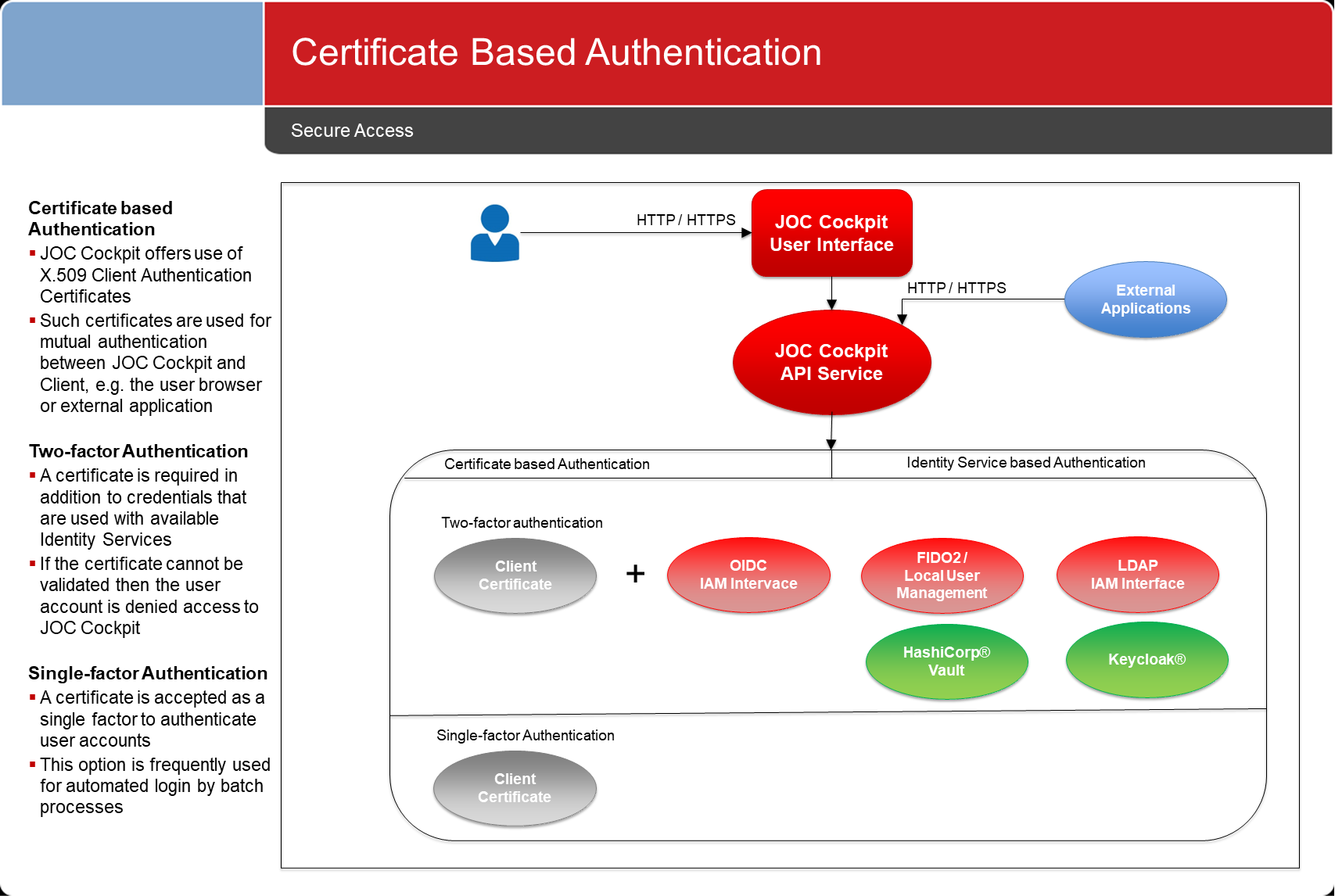
Certificate Based Authentication
Certificates can be used for mutual authentication, see JS7 - Certificate Identity Service.
- The client (Browser Client, REST API Client) challenges the JOC Cockpit server to present its Server Authentication Certificate which is then verified by the client.
- The JOC Cockpit server challenges the client to present its Client Authentication Certificate which is then verified by the JOC Cockpit.
When the JOC Cockpit is set up for mutual authentication, certificates can be used to:
- enforce two-factor authentication with clients having to provide a certificate and a password,
- allow single-factor authentication using a certificate instead of user account/password.
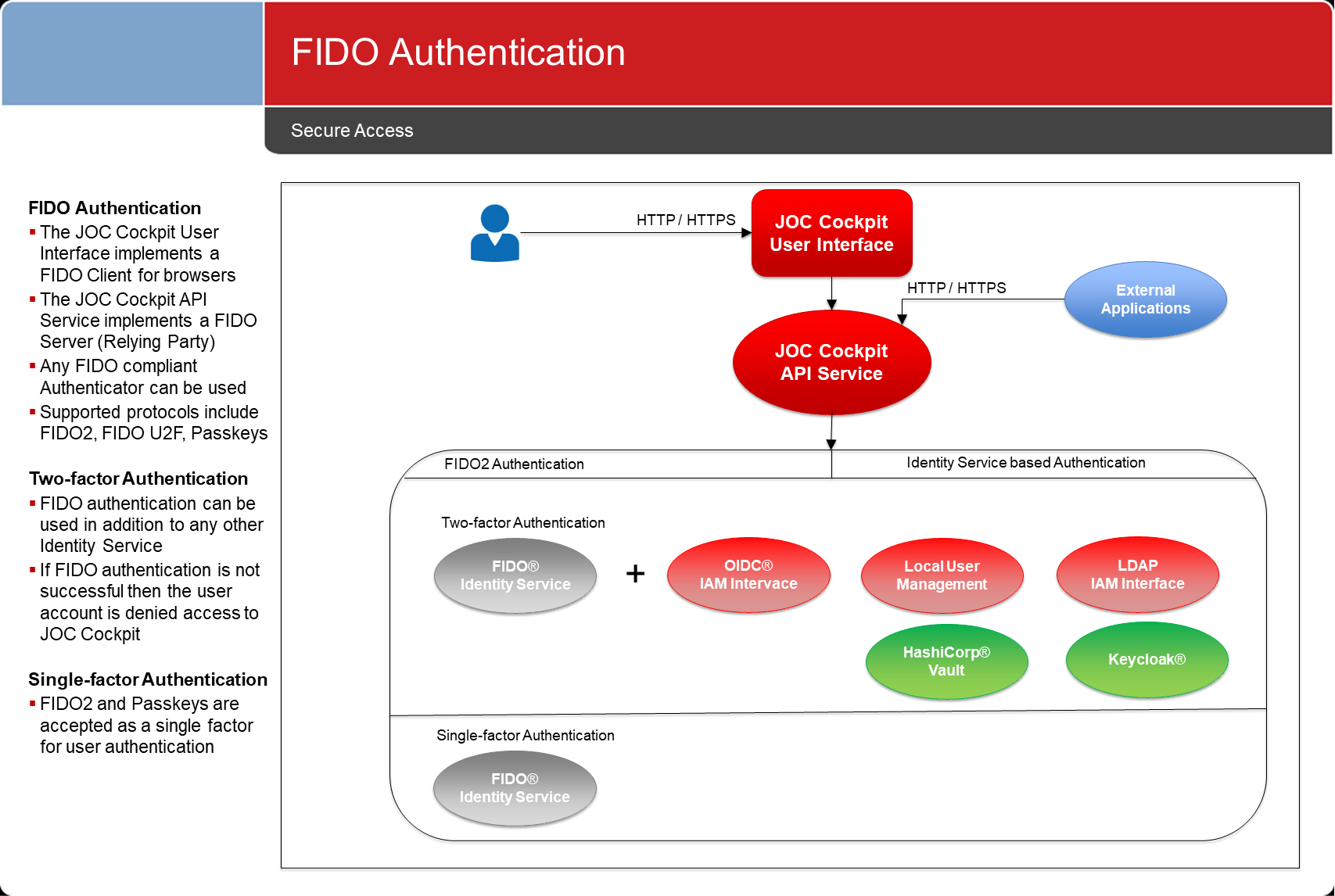
FIDO Authentication
The FIDO protocol family can be used for authentication, see JS7 - FIDO Identity Service.
- FIDO2 and Passkeys can be used as a first or second factor for authentication in MFA.
- FIDO U2F can be used as a second factor for authentication in MFA.
Further Resources
How To ... Instructions