Introduction
The JS7 - Profiles hold settings that are specific for a user account and that are controlled by the user.
- Profiles include a number of categories such as Preferences, Permissions etc.
- JS7 offers the JS7 - Git Repository Interface and JS7 - Inventory Git Integration
- Git credentials are managed from a user account's profile.
Manage Credentials for Git Access
Depending on the Security Level that JOC Cockpit is operated for the following applies:
- Low: Git credentials are added to the default account, typically the
rootaccount. - Medium: Git credentials are added per user account.
- High: Git credentials are not added to JOC Cockpit.
For low and medium Security Levels the Profile view offers the Git Management tab like this:
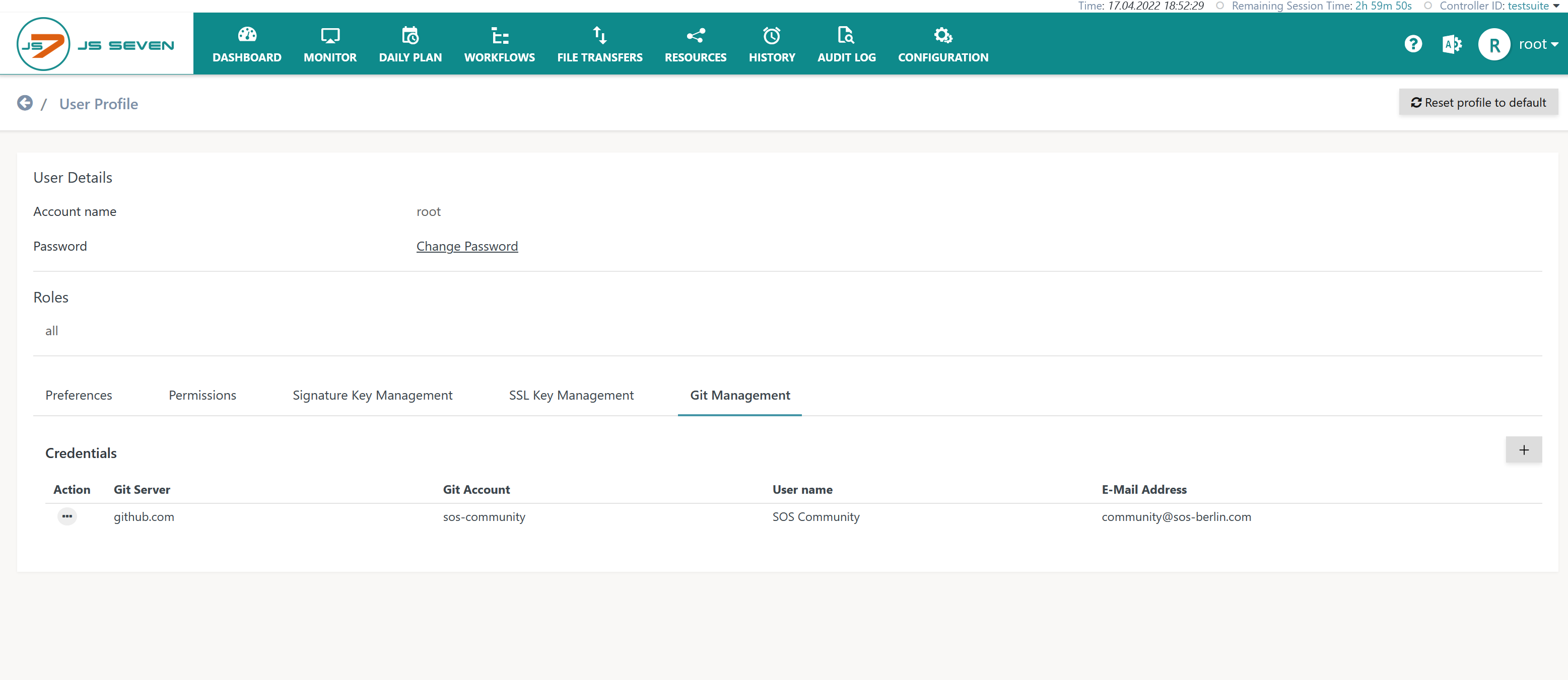
When clicking the Git Management tab then the list of available Git credentials is displayed like this:
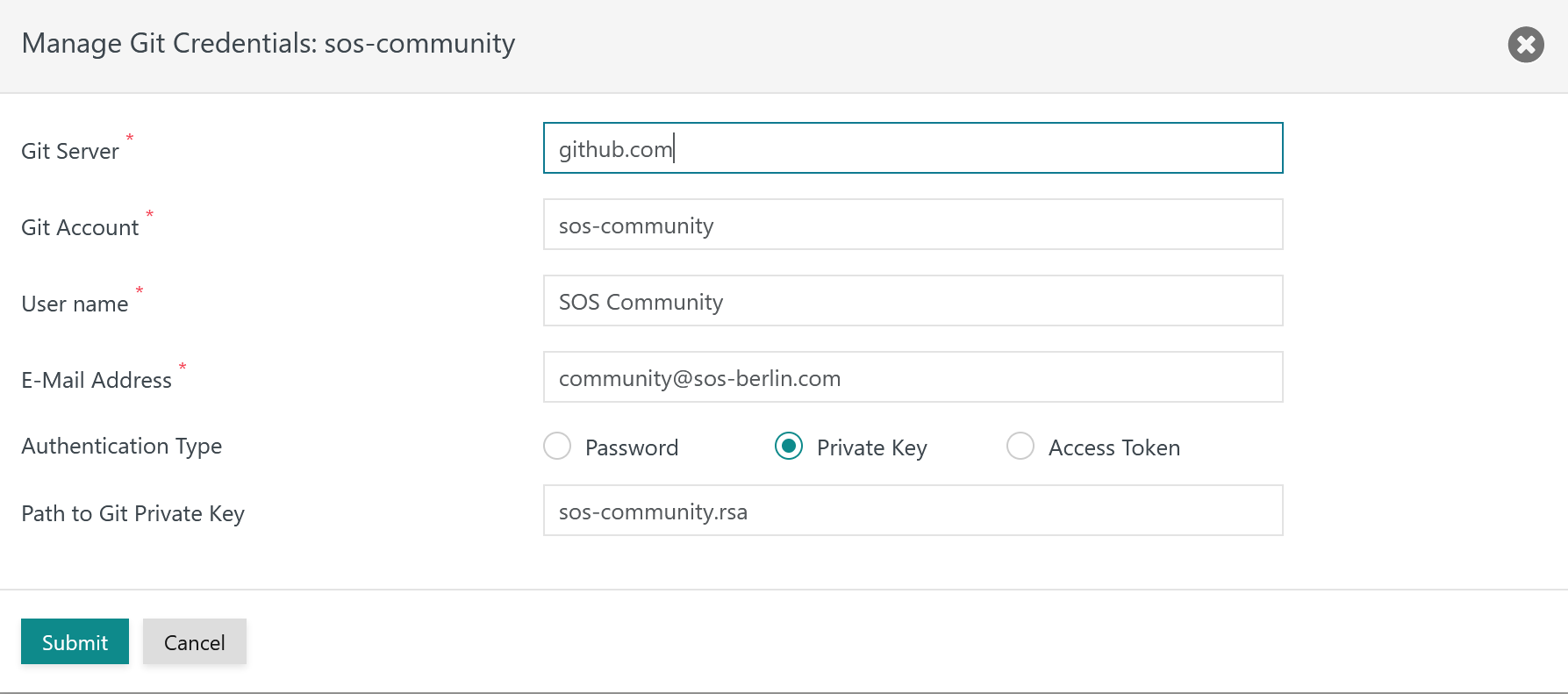
When clicking an entry and when clicking the button a popup window is displayed for management of credentials like this:
Explanation:
- Git Server: Credentials are managed per Git Server.
- The Git Server entry has to be unique. Users can manage different credential sets for different Git Servers. Should different Git Accounts be used for the same Git Server then different JOC Cockpit accounts have to be used.
- The Git Server is specified from the hostname and optionally the port of the Git Server.
- Git Account, User Name, E-Mail Address: The Git Account has to be available with the Git Server, the User Name and E-Mail Address can be freely chosen.
- Authentication Type: This offers to use one of the following options:
- Password: The authentication method is denied by a larger number of Git Servers.
- Private Key: The authentication method makes use of Secure Shell (SSH) that is included with the Git Client.
- The location of the Private Key file can be specified like this:
- file name: JOC Cockpit creates the directory
JETTY_BASE/resources/joc/repositories/privateto which the private key file has to be stored by the user. JOC Cockpit will use this directory to identify the Private Key file and to authenticate with the Git Server. - empty file name: JOC Cockpit will use the Private Key file
~/ssh/id_rsafrom the JOC Cockpit account's home directory. - path to a file: JOC Cockpit makes use of the indicated path to a Private Key file. The path has to be accessible to the run-time account of the JOC Cockpit daemon or Windows Service.
- file name: JOC Cockpit creates the directory
- Users have to manually store the Private Key file to the indicated location.
- Permissions for Private Key files have to be considered: read/write permissions for the owner account, no permissions for groups and others.
- The location of the Private Key file can be specified like this:
- Access Token: The authentication method is considered similarly insecure as use of Passwords and is not offered by all Git Servers.
- The Access Token is created and is stored with the Git Server.
Overview
Content Tools