Introduction
The Audit Log allows compliance and operations reporting requirements to be met by providing a automatic and secure record of all operations that users of the JobScheduler Web Service - including JOC Cockpit users and external applications - perform on job-related objects. The Audit Log lists the relevant JobScheduler objects - Jobs, Job Chains, Orders, etc. - and any operations that modify their status.The Audit Log is written by the JobScheduler Web Service as shown in the JOC Cockpit - Architecture page.
Scope of the Audit Log
The Audit Log is maintained for all job-related objects such as Jobs, Job Chains, Orders, etc., whose statuses are modified by users carrying out operations such as starting, stopping or pausing. It uses a format that is human and machine readable and fulfills the following main functions:
- provide a compliance-conform record in a simple file format that can be archived and handed over to a compliance officer,
- provide an operational record of that is readily accessible to operating staff,
- provide a second source of operational information should the database not be available.
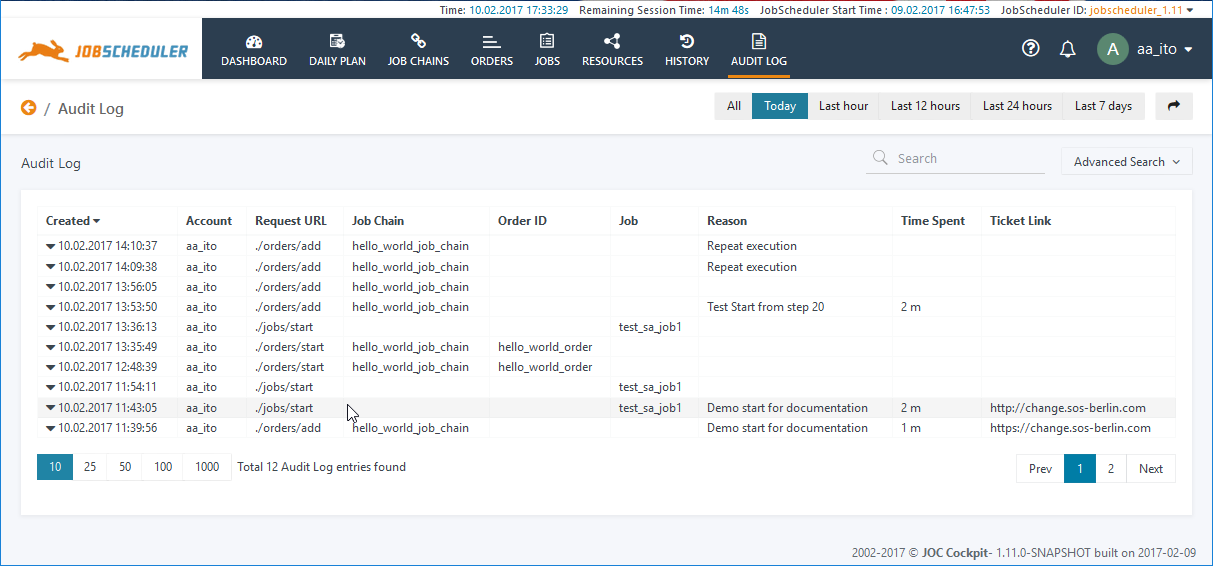
Operators of the JOC Cockpit with the necessary permissions can view the Audit Log in the JOC Cockpit by clicking the Audit Log link in the JOC Cockpit main menu as shown in the screenshot below:
Inclusion of the Audit Log view and in particular the Reasons field is intended to provide users of the JOC Cockpit with more relevant operational information taken than is recorded in the History.
Compliance and Operational Features
- The Audit Log is written automatically by the JobScheduler Web Services:
- Entries to the Audit log are made when an operation that changes the state of a JobScheduler Object is initiated in the JOC Cockpit or other application accessing the JobScheduler Web Services.
- There is no mechanism for switching off the Audit Log.
- The Audit Log is written in two locations simultaneously:
- In the DBMS used by the JobScheduler Web Services:
- This instance is used by the JOC Cockpit to allow operators to view the Audit Log information.
- It is also used by the JOC Cockpit to generate an Excel-compatible export file for reporting purposes.
- In the Audit Log file:
- It is intended that this instance is archived and used as a compliance record. System Administrators can make a copy of this instance available to operating staff if the DBMS should not be available.
- The Audit Log file is named
JOCAuditLog.logand saved in the./logsfolder.
- In the DBMS used by the JobScheduler Web Services:
- All new entries will be added to the Audit Log - neither the log file not the DMBS records are overwritten.
- System administrators have to arrange an archiving and housekeeping system for the Audit Log file according to the relevant compliance laws and corporate governance.
- It is the responsibility of system administrators to check compliance requirements such as the retention period for the information contained in the Audit Log file.
- The Audit Log is visible in the JOC Cockpit to:
- Users with the appropriate permissions. The specification of user permissions is described in the Authentication and Authorization - Configuration article.
- The default authorization permissions for the Audit Log which are configured for the JOC Cockpit are listed in the Permissions Matrix shown in the Authentication and Authorization - Permissions for the JOC Cockpit Web Service article.
- System Administrators with access to the DBMS used by the JOC Cockpit or the file system where the Audit Log file is written.
- The Audit Log is read-only for all JOC Cockpit users - only System Administrators that have access to the file system and to the database can modify the log.
- Users with the appropriate permissions. The specification of user permissions is described in the Authentication and Authorization - Configuration article.
Key to the Audit Log Entries
- Created: the point in time when the action was performed.
- Account: the user account that caused the action.
- Request URL: the Web Service URL that was invoked by the JOC Cockpit. The URLs represent the object type and action, e.g. /orders/start.
- Job Chain, Order ID, Job: identifies the object for which the action was performed.
- Reasons: (can be mandatory or optional - see below) an explanation of why an action was carried out. Reasons are created either by selecting an item from a list of predefined reasons (configurable) or individual - i.e. free text input. A maximum of 2000 characters can be added to a free text reason.
- Time Spent: (optional) the number of minutes required for the action (including time for impact analysis) can be added.
- Ticket Link: (optional) a URL can be added that points to a ticket system, e.g. the SOS Ticket System, to identify the underlying ticket for the intervention.
Operation Reasons
Users carrying out operations are able to add an explanatory reason for each operation. These reasons are then saved in the Audit Log and can be read by all other JOC Cockpit users with the necessary permissions. The 'Enter a Reason' form is shown after each operation is initiated and can be seen in the following screenshot:
Reasons may be mandatory and two forms of reasons are possible:
- Predefined Reasons which are selected from a drop-down list and
- Individual Reasons as shown in the above screenshot.
The Submit and Cancel buttons in the Enter a Reason form refer to the operation being carried out. This means that:
- even when reasons are optional, selection of the Cancel button will cause the operation being carried out to be broken off - not just entry of the reason.
Mandatory Reasons
The force_comments_for_audit_log flag can be set in the joc.properties file as shown in the following code box:
### This flag controls if the comment is required or not. force_comments_for_audit_log = false
The joc.properties file is located in the ./joc_home/jetty_base/resources/joc directory.
Either predefined or individual reasons can be set when force_comments_for_audit_log = true is set.
Predefined Reasons
A predefined set of reasons is delivered with the JOC Cockpit.
Predefined reasons are found in the ./joc_home/jetty_base/resources/joc directory, in the joc.properties file.
The predefined reasons are listed in the following code box:
### Pre-defined comments
comments = System maintenance; \
Repeat execution; \
Business requirement; \
Restart failed execution; \
Re-instantiate stopped object; \
Temporary stop; \
Change of JobScheduler object; \
Rerun with parameter changes; \
Change of external dependency; \
Application deployment and upgrade
Predefined Reasons Syntax
- The ";" near the end of each line marks the end of the comments. The semicolon here functions as a delimiter and allows commas to be used in reasons.
- The "\" at the marks the end of a line.
Modifying Reasons Settings
System administrators are free to modify predefined reasons and the force_comments_for_audit_log flag to suit their own requirements.
The JOC Cockpit needs to be restarted before changes made to the joc.properties file will take effect.
Individual Reasons
Individual Reasons can be entered in the text field as shown in the screenshot above.
The following characters are allowed:
- A-Z, a-z, 0-9, commas
Audit Log Location
The Audit Log is found in the ./joc_home/jetty_base/logs directory, in the JOCAuditLog.log file. If the file does not exist, it will be created with the first operation modifying the status of an object that is carried out by a user.
Audit Log Sample
The following sample shows a number of Web Service requests that have been performed by a user "ap":
Audit Log Explanation
- The Audit Log includes the Web Service URL, which allows the object type and operation to be identified. For example, .
/orders/resumetranslates to the operation to resume an order that is identified by its order ID and Job Chain path, as specified in the parameters part of each log entry.
Audit Log Housekeeping & Archiving
As already noted the JOC Cockpit adds to the Audit Log on an ongoing basis.
System administrators need to implement their own housekeeping / log rotation and archiving system according to their business and compliance requirements.