Introduction
LDAP authentication for the JOC Cockpit is provided by the JS7 - LDAP Identity Service and relies on a connection between the JS7 - REST Web Service API and the LDAP Server.
- This connection should be secured, otherwise it is vulnerable for example to man-in-the-middle attacks.
- The LDAP Server connection can be secured using two commonly available protocols "LDAP over TLS" (STARTTLS) and "LDAP over SSL" (LDAPS).
- General information how to configure LDAP connections is available from the JS7 - LDAP Identity Service Configuration article.
This article describes the configuration of STARTTLS for use with the JS7 REST Web Service API and and a certificate truststore, as well as providing an example for use with LDAPS.
Secure Connection Schemes
Connection Content Encryption with STARTTLS
STARTTLS is an extension to the LDAP protocol that uses the TLS protocol to encrypt communication. It works by establishing a normal - i.e. unsecured - connection with the LDAP server before a handshake negotiation between the server and the web service is carried out. Here, the server sends its certificate to prove its identity before the secure connection is established. If negotiation for a secure connection is unsuccessful then a standard LDAP connection may be opened as a fallback. Whether or not this occurs depends on the LDAP Server and its configuration.
Connection Encryption with LDAPS
LDAPS is the non-standardized "LDAP over SSL" protocol that in contrast with STARTTLS only allows communication over a secure port such as 636. It establishes the secure connection before there is any communication with the LDAP Server. However, as LDAPS is not part of the LDAP standard, there is no guarantee that LDAPS client libraries actually verify the host name against the Common Name provided with the LDAP Server certificate. See https://shibboleth.net/community/advisories/secadv_20120227.txt for details.
Configuration
Configuration for LDAP over TLS
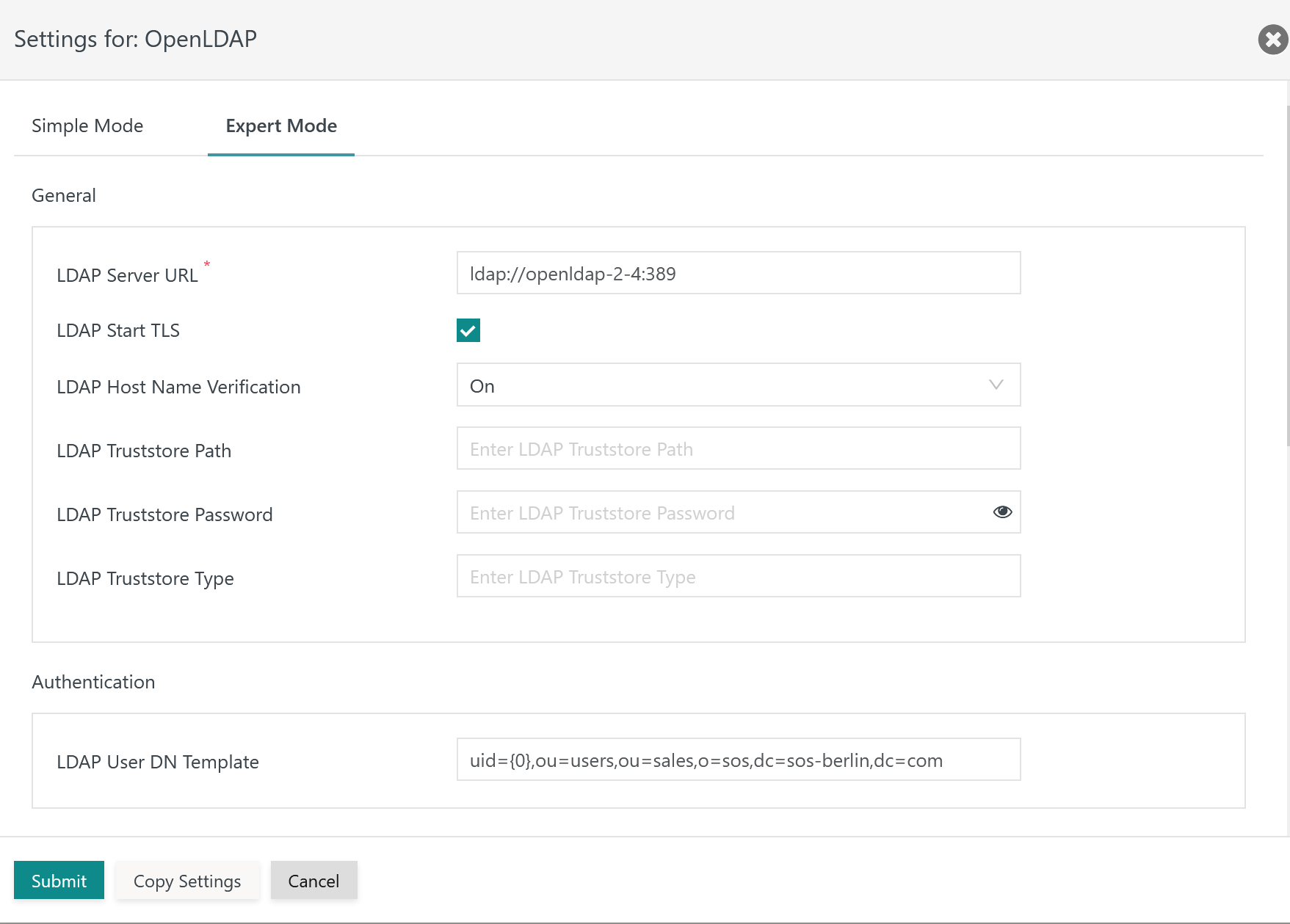
The following settings are available when managing the LDAP Identity Service:
Explanation:
LDAP Server URL: The LDAP Server URL specifies the protocolldap://for the TLS connection. The hostname (FQDN) and port are added to the LDAP Server protocol. An IP address cannot be used as it would not match the LDAP Server certificate.LDAP Start TLS: This switch makes TLS the protocol for the connection to the LDAP Server.LDAP Host Name Verification: This switch has to be active to check if hostnames in theLDAP Server URLand in the LDAP Server certificate match.LDAP Truststore Path: The TLS protocol requires a truststore to be used which holds an X.509 certificate specified for the Extended Key Usage of Server Authentication.- The truststore can include a Self-issued Certificate or a CA-signed Certificate. Typically the Root CA Certificate is used as otherwise the complete certificate chain involved in signing the Server Authentication Certificate has to be available with the truststore.
- If this setting is not specified then JOC Cockpit will use the truststore that is configured with the
JETTY_BASE/resources/joc/joc.propertiesconfiguration file. This includes use of settings for the truststore password and truststore type. - The path to the truststore is specified relative to the
JETTY_BASE/resources/jocdirectory. If the truststore is located in this directory then only the file name is specified, typically with a .p12 extension. Other relative locations can be specified using e.g.../../joc-truststore.p12if the truststore is located in theJETTY_BASEdirectory. Absolute paths cannot be specified and a path cannot be specified that lies before theJETTY_BASEdirectory in the file system hierarchy.
LDAP Truststore Password: If the LDAP truststore is protected by a password, then the password has to be specified.LDAP Truststore Type: The type of the indicated truststore has to be specified being eitherPKCS12orJKS(deprecated).
Configuration for LDAP over SSL
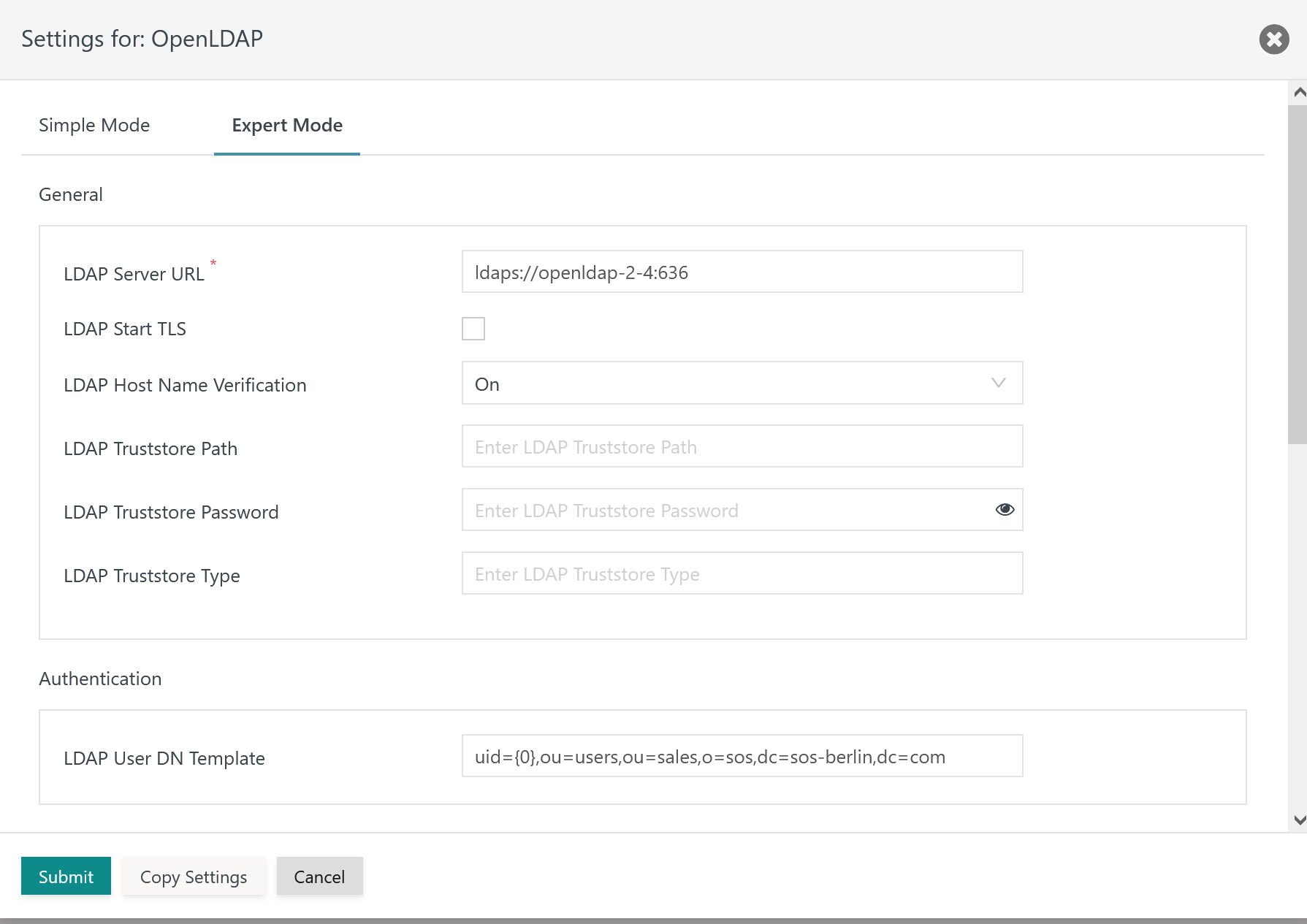
When managing the LDAP Identity Service the following settings are available:
Explanation:
LDAP Server URL: The LDAP Server URL specifies the protocolldaps://for the SSL connection. The protocol is added the hostname (FQDN) and port of the LDAP Server. An IP address cannot be used as it would not match the LDAP Server certificate.LDAP Start TLS: This switch is not used as it would make TLS the protocol for the connection to the LDAP Server.- For the remaining settings see the Configuration for LDAP over TLS section above.
Certificate Management
The certificates for use with both TLS and SSL protocols are distributed in a similar way.
Users can use certficates issued by a Private CA or by a Public CA.
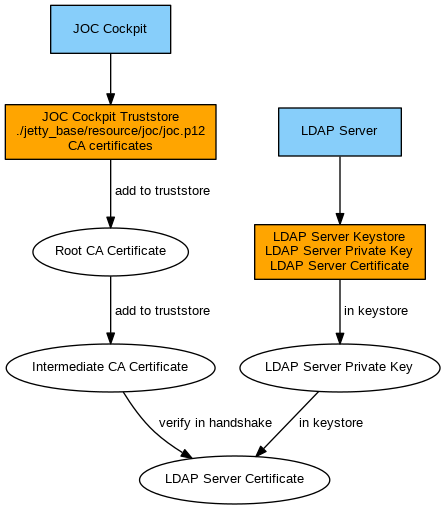
Use with CA-signed Certificates
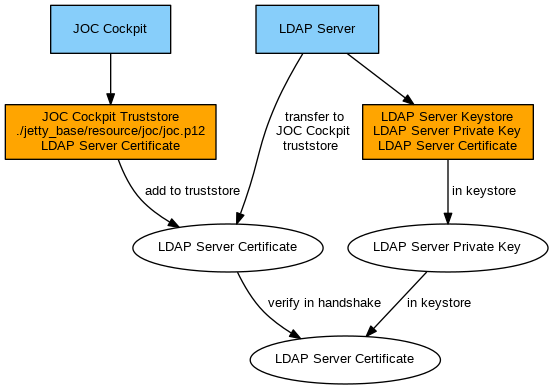
Use with Self-issued Certificates
Set up JOC Cockpit Truststore and import Certificates
The following steps are performed on the server that hosts the JOC Cockpit.
In the following the JETTY_BASE placeholder is used:
JETTY_BASEis Jetty's base directory that is specified during JOC Cockpit installation:- C:\ProgramData\sos-berlin.com\joc (default on Windows)
- /home/<setup-user>/sos-berlin.com/joc (default on Linux)
See the JS7 - JOC Cockpit HTTPS Connections articles about truststores for more information.
Example how to import Certificates
The following examples imply use of the Java keytool utility, however, other tools might be applicable such as the OpenSSL CLI, Keystore Explorer etc.
Example for importing a certificate to a JOC Cockpit truststore in PKCS12 format:
Example for import of LDAP Server Certificate to PKCS12 Keystore# import LDAP Server certificate to a truststore (joc.p12) by specifying the certificate file (ldap-certificate.crt) and alias name (ldap) keytool -importcert -noprompt -file "ldap-certificate.crt" -alias "ldap" -keystore "JETTY_BASE/resources/joc/joc.p12" -storetype pkcs12 -storepass secret_store -trustcacerts
Example for importing a certificate to a JOC Cockpit truststore in JKS format:
Exmple for import of LDAP Server certificate to JKS Keystore# import LDAP Server certificate to a truststore (joc.jks) by specifying the certificate file (ldap-certificate.crt) and alias name (ldap) keytool -importcert -noprompt -file "ldap-certificate.crt" -alias "ldap" -keystore "JETTY_BASE/resources/joc/joc.jks" -storetype jks -storepass secret_store -trustcacerts
- Explanation
- The
-keystoreoption specifies the location of the truststore file. - The
-storepassoption specifies the password for access to the truststore. - The certificate file
ldap-ertificate.crtshould be available from the LDAP Server. Transfer this file to the JOC Cockpit server. Alternatively the server certificate can be requested on-the-fly.Example for request of server certificate:
Example for request of server certificate from LDAP Server# connect to the LDAP Server (ldap_server) with the available port (636), in the server response you should find the certificate that you can copy & paste to a certificate file openssl s_client -showcerts -connect ldap_server:636
If the certificate is signed by a CA then the certificate can include the certificate chain of Root CA Certificate and Intermediate CA Certificate. Otherwise it might be required to concatenate the certificates into one file, for example:
Example for use of a certificate chain# concatenate Root CA certificate and Intermediate CA certificate as provided from the LDAP Server to a single CA Bundle certificate file (ca-bundle.crt) cat RootCACertificate.crt > ca-bundle.crt cat IntermediateCACertificate.crt >> ca-bundle.crt # import LDAP Server certificate and certificate chain to a truststore (joc.p12) by specifying the certificate file (ldap-certificate.crt) and alias name (ldap) keytool -importcert -noprompt -file "ca-bundle.crt" -alias "ldap" -keystore "JETTY_BASE/resources/joc/joc.p12" storetype pkcs12 -storepass secret_store -trustcacerts
- The
Example how to configure the JOC Cockpit Truststore
Find examples for entries in the
JETTY_BASE/resources/joc/joc.propertiesconfiguration file to specify a truststore:Example
Example for joc.properties setting for a truststore in PKCS12 formattruststore_path = joc.p12 truststore_type = PKCS12 truststore_password = secret_store
Example
Example for joc.properties setting for a truststore in JKS format with relative locationtruststore_path = joc.jks truststore_type = JKS truststore_password = secret_store
Explanation
- Specifies the location of the truststore with the
truststore_pathsetting. A location relative to theJETTY_BASE/resources/jocdirectory can be specified. If only a file name is specified such asjoc.p12then this directory is assumed. Use of a relative path such as../../joc.p12locates the truststore file in theJETTY_BASEdirectory.
- Specifies the location of the truststore with the