Introduction
- JS7 - Identity Services implement Authentication Methods and access to Identity Providers, for example credentials such as user account/password are used as an Authentication Method to access an LDAP Directory Service acting as the Identity Provider, see JS7 - Identity and Access Management.
- Depending on the Identity Service Type in use the user accounts are managed and stored with the Identity Service or with JOC Cockpit, see JS7 - Identity Services.
- JOC Cockpit manages permissions and roles for any Identity Services and stores such information independently from the Identity Service.
Manage User Accounts, Roles and Permissions
After installing the JOC Cockpit a user can log in with the default root user account and root password that are available from the JS7 - JOC Identity Service.
- This Identity Service is active and is the only Identity Service available by default.
- This Identity Service includes the default
rootuser account. Users are encouraged to change the password of therootuser account after initial installation of JOC Cockpit.
To manage user accounts, roles and permissions from any JOC Cockpit page use the user menu in the right upper corner and select Manage Identity Services:
The Manage Identity Service page holds the list of the available Identity Services. By default the list is populated from the JS7 - JOC Identity Service. Users can add new Identity Services. From this page users can select an Identity Service to manage the user accounts associated with the Identity Service. Assume that the JOC Identity Service is selected by clicking the name JOC.
The JOC Identity Service page offers three sub-tabs: Accounts, Roles, Profiles
Explanation:
- Accounts: Management of user accounts that are stored with the JS7 database.
- Roles: Permissions can freely be grouped to roles. This includes to specify permissions for scheduling objects in JOC Cockpit and in Controllers.
- Permissions: a sub-view offered to manage access to folders and permissions.
- Profiles: Information about the date of last login by user accounts.
The Accounts sub-view
The Accounts sub-view is displayed when a user selects the Identity Service from the Identity Management Service page. The sub-view lists the user accounts that have been configured along with their roles.
The above screenshot shows the test user account that assigned the test-role role.
The Add Account button can be used to open a popup window to add a new user account.
- The additional options (ellipsis) symbol allows an Account to be edited (change the Account Name and/or Password, select/deselect Roles) and to be copied or deleted.
- Clicking the Account Name navigates the user to the Roles sub-view that offers to assign the role permissions for JOC Cockpit and Controllers.
The Roles sub-view
The Roles sub-view allows to assign permissions for access to scheduling objects with JOC Cockpit and Controllers.
When the sub-view is opened after initial installation of JOC Cockpit then it is populated from default roles and permissions, see JS7 - Permissions. Users are free to modify, to add and to delete any roles. Please keep in mind that at least one role that includes administrative permissions to access all objects in JOC Cockpit and Controllers is required and has to be assigned an administrative user account. Should no administrative role be left then this corresponds to closing the door behind you and throwing away the keys.
Roles indicate default for the Controller which translates to the fact that permissions from default are applied to any Controllers.
If the Roles sub-view is opened by clicking the Account Name in the Accounts sub-view then the Roles sub-view will display roles only that have been assigned the selected user account. The user account selected is displayed with the Account button that can be used to switch to a different user account.
Positioning the mouse over a role name blends in two links as shown in the screenshot above:
- the pencil link allows the role to be edited and
- the X link allows the role to be deleted.
A set of permissions is configured for each role. Each permission set can be inspected by clicking default from the list of roles. This will open the Permissions sub-view for the given role. The matrix of default roles and permissions along with descriptions per permission is provided with the JS7 - Permissions article.
The Permissions sub-view
The Permissions sub-view allows to manage permissions for roles, optionally limited to specific folders.
- Scope
- JOC Cockpit Permissions are assigned for operations in JOC Cockpit, for example to manage calendars and the daily plan etc.
- Controller Permissions are assigned for operations on scheduling objects per Controller, for example to deploy workflows, to add orders etc.
- If more than one Controller is connected to JOC Cockpit then a user account can be assigned a role that for example allows deployment to one Controller but not to other Controllers.
- Controller permissions can be specified as a default for any Controllers and they can be specified on a per Controller basis.
- States
- Permissions can take one of three states, being unassigned, granted or denied.
- An unassigned permission does not take any assumption if the permission is granted or denied.
- A granted permission is active within limits as is can be overruled by denied permissions.
- A denied permission is active without limits and cannot be overruled by granted permissions.
- Merge
- Permissions are assigned to roles. A user account can accumulate a number of roles, therefore the permissions are merged by the following rules.
- JOC Cockpit Permissions
- Unassigned permissions are ignored.
- Granted permissions work across any roles unless merged with a denied permission from a role.
- Denied permissions work across any roles and cannot be overruled by granted permissions from any role.
- Controller Permissions
- Default Controller
- Unassigned permissions are ignored.
- Granted permissions overrule unassigned permissions from any roles and Controllers.
- Granted permission can be overruled from any roles, they can be
- denied by a permission of the Default Controller specified by some other role,
- denied by a permission for a Specific Controller.
- Denied permissions
- Specific Controller
- Unassigned permissions are ignored, instead the permission of the Default Controller is applied.
- Granted permissions work across any roles unless denied by a permission from any role for the given Controller.
- Denied permissions work without limits across any roles for the given Controller.
- Default Controller
- JOC Cockpit Permissions
- Permissions are assigned to roles. A user account can accumulate a number of roles, therefore the permissions are merged by the following rules.
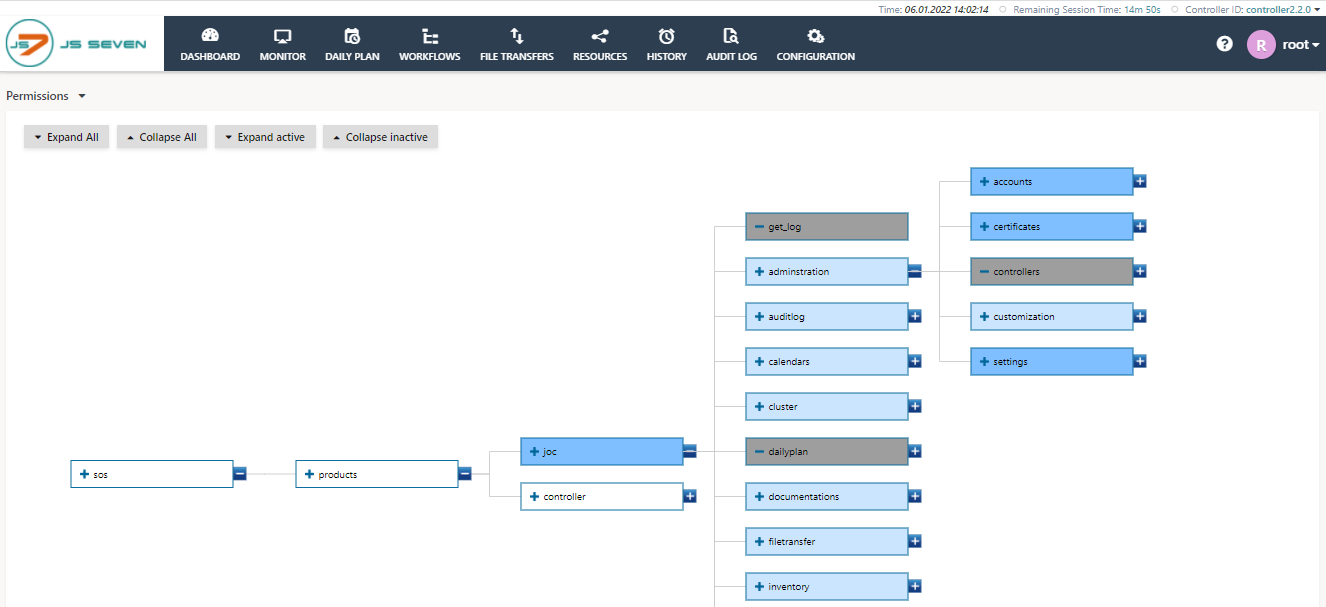
- Permission Tree
- Permissions are organized from a tree that offers a hierarchy of branches.
- Granting or denying permissions at a higher level inherits the permission recursively to deeper levels of the tree.
Permission Management
A graphical and a textual view are available for management of permissions added to a role.
The Graphical View
This view allows graphical navigation and selection of permissions and is the default view.
- Explanation:
- Navigation
- The Expand All and Collapse All buttons open and close any child branches.
- The Expand Active and Collapse Active buttons open and close child branches with granted or denied permissions.
- The
+and-icons at the right edge of each permission icon open and close child branches.
- States and Colors
- Permissions show the following background colors to indicate their state:
- White: Permission is not assigned, i.e. is not granted and is not denied.
- Dark Blue: Permission is granted and the grant is inherited to child permissions recursively.
- Light Blue: Permission is inherited from a granted parent permission.
- Dark Grey: Permission is denied and the denial is inherited to child permissions recursively..
- Light Grey: Permission is inherited from a denied parent permission.
- Granting Permissions
- Clicking the middle of an unassigned (white) permission grants the permission (dark blue).
- Clicking the middle of a granted permission revokes the grant and puts the permission to the unassigned state (white).
- Denying Permissions
- The
+icon inside a permission icon denies the permission (dark grey) recursively for child permissions that are located deeper in the permissions tree (light grey). - A denied permission shows the
-icon, clicking this icon revokes the denial and puts the permission to the unassigned state.
- The
- Permissions show the following background colors to indicate their state:
- Undo/Redo
- Changes to the permissions tree are stored to the JS7 database.
- The Undo button allows the last 10 changes to be undone stepwise.
- Any changes held in the Undo button will be deleted when the user leaves the Permissions sub-view.
- The Redo button changes the permissions tree back to its initial state when the Permissions sub-view is displayed.
- The state held with the Redo button is deleted when a user leaves the Permissions sub-view.
- Navigation
The Textual View
The editor displays permissions from a lists of textual entries. The right upper corner of the Permissions sub-view offers to toggle between graphical view and textual view.
- Explanation:
- Individual permissions can be modified and removed from the role using the pencil and X icons that are faded in when the user's mouse is moved over a permission.
- The Edit function allows the permission to be made subtractive, i.e. for permission granted at a higher level to be removed.
- The folder part of the view is used to restrict the role to access particular folders only - this includes that any scheduling objects such as workflows are visible from the assigned folder only.
Folder Selection
Folders are added using the Add Folder button visible in the background of the below screenshot in the upper right corner:
Folders are selected from a tree view that is opened by clicking the folder icon, see screenshot.
Configuration
Manage User Accounts and Roles
Administrators create and configure user accounts and roles, for example, to limit access to resources such as workflows and logs.
It is straightforward to first add roles, then assign permissions - optionally limited to folders - and finally to add user accounts and to assign roles.
Add a Role
- Roles are created from the Roles sub-view using the Add Role button:
- Once the role is created it is added automatically to the list of roles displayed in the background of the above page.
Configure Permissions for a Role
- Now expand the Role using the arrow button click on the default (blue link) to add Permissions and/or Folders in the Permissions sub-view. The procedures available for managing permissions and folders are explained with the Editing User Permissions and Folders sections below.
- Note that roles that neither have permissions nor folders assigned are deleted automatically when a user leaves the Manage Identity Service page.
Add a User Account
- With permissions / folders being configured select the Accounts sub-view to add a user account and assign one or more roles.
- The Edit Account function is accessed by clicking the relevant Action symbol (ellipsis) in the Actions column of the User Accounts list (visible in the background of the above screenshot). This can be used to change the password or account name and to add or to remove roles.
- Note that deselecting a role in this popup window 'uncouples' the role from the user account - it does not delete the role.
Manage User Permissions
Permissions Structure
Permissions are organized in a hierarchical way:
- A Role with the Permission
sos:products:controller:view'only' allows a User to view Controllers, while a user with the 'higher'sos:products:controllerpermission is able not only to view Controllers but is able to carry out additional operations - in this case, view, restart, terminate, and switch_over. - The JS7 - Permissions article contains a link to a full list of all Permissions that can be granted.
Editing Permissions
Consider any user have a role(demo-role) with the following permission:
sos:products:controller:view
This permission does not allow the demo-role to perform the operation on the Controllers. These Permissions could be granted individually with the following:
sos:products:controller:restartsos:products:controller:terminate
The following Permissions can be set to allow the demo-role Role to view, restart and terminate the Controller, but not Switch_over:
sos:products:controller:viewsos:products:controller:restart
Alternatively, it may make sense in some situations to grant the Role a higher level of Permission and then remove one or more specific Permissions. This approach is shown in the following combination:
sos:products:controller
-sos:products:controller:switch_over
where the ...sos:products:controller Permission is an overall 'Controller' Permission covering view, restart and terminate, and the - Permission is removed from the demo-role Role.sos:products:controller:switch_over
Caution
Users should have Role with the following Permission - or higher - before they are able to log into the JOC Cockpit:
sos:products:joc:administration:controller:view
Editing Procedures
Three editing procedures are available for editing Permissions:
Adding Permissions:
- The Add Permission button in the Permissions View allows a Permission to be selected from a list of all available Permissions as shown in the screenshot below.
- Note that the Permissions listed are all individual Permissions. They can be edited to make them higher level / less specific.
- For example, the screenshot below shows that the
...administration:controller:viewpermission in the process is selected. - Selected permission can also be made subtractive - i.e. to remove a specific part of a higher level Permission.
- This is done by ticking the Excluded checkbox, which is obscured in the above screenshot.
- For example, the screenshot below shows that the
- Note that the Permissions listed are all individual Permissions. They can be edited to make them higher level / less specific.
- The Add Permission button in the Permissions View allows a Permission to be selected from a list of all available Permissions as shown in the screenshot below.
Modifying Existing Permissions:
- The pencil symbol is shown alongside existing Permissions in the Permissions view (shown in the screenshot above) can be used to change the function of a Permission in a Role - to make an additive Permission subtractive and vice-versa. It cannot be used to edit a Permission.
- The X symbol displayed alongside existing permissions in the Permissions sub-view is used to remove a permission from a role.
- Note that a role must be configured to be assigned either a permission or a folder as otherwise the role is considered empty and will be deleted.
- Note that if a user account is not assigned the following permission (or a permission from a higher level) then this user account will not be able to login to JOC Cockpit:
sos:products:joc:administration:controller:view
Graphical Permission Editing:
- The graphical view is activated by selecting the 'tree' symbol at the top right corner of the Permissions sub-view:
- The editor opens with a partially collapsed permissions tree as shown in the next screenshot:
- The Expand All button (shown in the above screenshot) can be used to open all the tree elements.
- Navigation is carried out by dragging & dropping the tree view.
- The functions available for the tree elements are (with reference to the screenshot below):
- Select / Unselect a Permission - click on the body of an unselected / selected element
- Selected Permission elements are shown in blue (see the view element in the screenshot)
- Children of selected Permission elements are shown in light blue (as shown in the screenshot)
- Select / Unselect a Permission - click on the body of an unselected / selected element
- The graphical view is activated by selecting the 'tree' symbol at the top right corner of the Permissions sub-view:
- Deny a Permission - click on the plus sign at the left hand end of the element
- Revoke a Permission Denial - click on a - sign at the left hand end of the element
- Show / hide child elements - click on the + / - symbols at the right edge of an element
- In the following screenshot the administration element has been selected, automatically selecting the administration:accounts, administration:certificates, administration:controllers, administration:customization, administration:settings
- In addition, the controllers:manage child permission has been denied, resulting in the fact that the controllers:view is active only.
Manage Permissions specific for a Controller
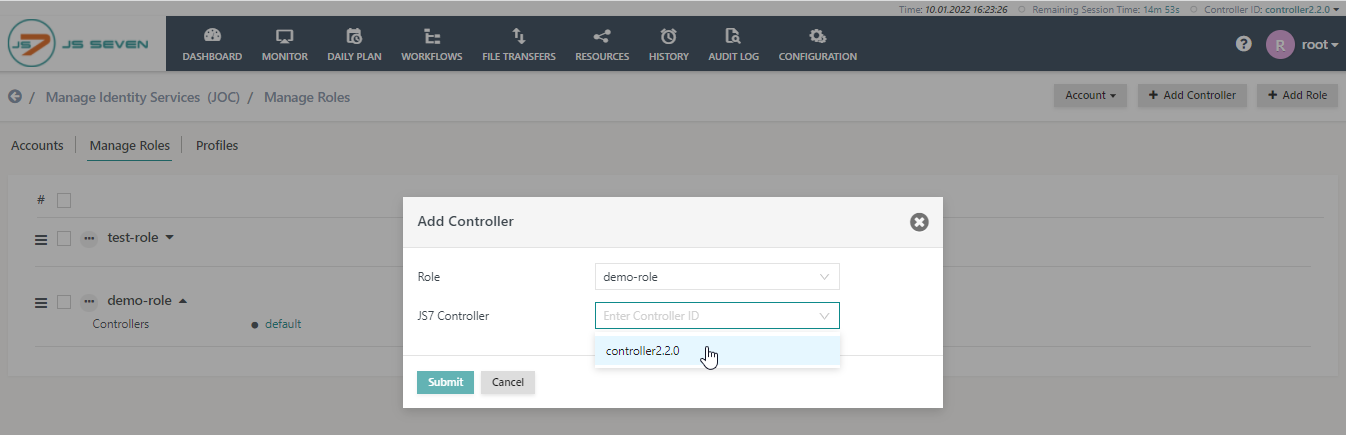
By default User Accounts are granted permissions for all Controllers in a scheduling environment. Permissions that are applicable to a particular Controller only can be added to a role. This can be achieved in the Manage Roles sub-view of the Identity Management Service.
In the screenshot, the demo_role role has been assigned for the Controller with ID controller2.2.0. and will appear in the list of roles as follows.
In this configuration, the demo_role role does not yet have any permissions specific to the Controller ID controller2.2.0. At least one permission needs to be added before the controller2.2.0 - demo_role configuration will be stored persistently.
The interaction of default Controller permissions and Controller specific permissions within the same role is illustrated as follows.
- default permissions:
sos:products:controller:view
- Controller-specific permissions:
sos:products:controller:agents:view
The Dashboard view for all Controllers will display the status of the current Controller but the status of Agent Clusters will only be displayed for the specified Controller - in this case for Controller ID controller2.2.0.
Manage Folder Permissions
Folders are used to restrict access to objects such as workflows and schedules. For example, user accounts can be limited to access objects for particular mandators / clients only.
By default permissions are granted for all folders. However, roles can limit access to specific folders.
This is achieved by adding a folder permission, i.e. a set of permissions to view the content of a specific folder only. With a folder permission being in place the permission to access other folders is automatically revoked. If folder permissions should be used for a number of folders then each folder permission has to be specified individually.
Granting Folder Permissions
Folder permissions are granted from the Permissions sub-view. Note that before folder permissions can be assigned a role, the role has to be specified for a user account. In the below example, a test user account and demo_role role have been configured and the demo folder has been created in the inventory.
To open the Permissions sub-view for a specific role, first open the Manage Identity Services page for the respective Identity Service, switch to the Roles sub-view and select the role that should be assigned folder permissions. For assignment click the name of the role in the list of roles.
Click the Add Folders button and in the popup window select a root level folder or a sub-folder such as /demo/*. or demo/.
Check the Recursive checkbox in the Add Folder popup window if recursive access to sub-folders is required and click the Submit button.
Any user account that is assigned the demo_role will be able to access scheduling objects in the demo folder only.
Note that the test user account will be able to log in to the JOC Cockpit without being assigned a role, however, no menu items and no functionality is offered from the GUI. A minimum permission is required e.g. by a role that grants the following permission:
sos:products:controller:view