Introduction
- Identity Services implement Authentication Methods and access to Identity Providers, for example, credentials such as user account/password are used as an Authentication Method to access an LDAP Directory Service acting as the Identity Provider, see JS7 - Identity and Access Management.
- JOC Cockpit implements a pluggable architecture that allows to add Identity Service products with future JS7 releases.
- By default JS7 ships with two built-in Identity Services:
- JOC: includes to manage user accounts with JOC Cockpit and to use the JS7 database for persistence.
- LDAP: includes to authenticate users with an LDAP Directory Service.
- For compatibility reasons early releases of JS7 include the Shiro Identity Service, see
JOC-1145
-
Getting issue details...
STATUS
- FEATURE AVAILABILITY ENDING WITH RELEASE 2.3.0
Matrix of Identity Services
Identity Services can be used in a number of flavors depending on the fact
- which application manages user accounts/passwords:
- the Identity Provider that is specific to an Identity Service,
- JOC Cockpit that propagates user accounts/passwords to the Identity Service but does not store such credentials with the JS7 database.
- where assignments of roles to user accounts are stored
- with the Identity Provider of the Identity Service,
- with the JS7 database.
| Identity Service | Identity Service Configuration Items | JOC Cockpit Configuration | ||||
|---|---|---|---|---|---|---|
| Service Type | Built-in | User Accounts/Passwords stored with | User Accounts/Passwords managed by | Roles/Permissions stored with | Roles->User Accounts Mapping managed with | Roles Mapping |
| JOC | yes | JS7 Database | JOC Cockpit | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit |
| LDAP | yes | LDAP Server | LDAP Server | JS7 Database | LDAP Server | Mapping of LDAP Security Groups to JOC Cockpit Roles performed with the LDAP Server |
| LDAP-JOC | yes | LDAP Server | LDAP Server | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit |
| VAULT | no | Vault Server | Vault Server | JS7 Database | Vault Server | Mapping of Vault Policies to JOC Cockpit Roles |
| VAULT-JOC | no | Vault Server | Vault Server | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit |
| VAULT-JOC-ACTIVE | no | Vault Server | Vault Server / JOC Cockpit | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit |
| KEYCLOAK | no | Keycloak Server | Keycloak Server | JS7 Database | Keycloak Server | Mapping of Keycloak Policies to JOC Cockpit Roles |
| KEYCLOAK-JOC | no | Keycloak Server | Keycloak Server | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit |
| KEYCLOAK-JOC-ACTIVE | no | Keycloak Server | Keycloak Server / JOC Cockpit | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit |
| Shiro (deprecated) | yes | shiro.ini | shiro.ini | shiro.ini | shiro.ini | n/a |
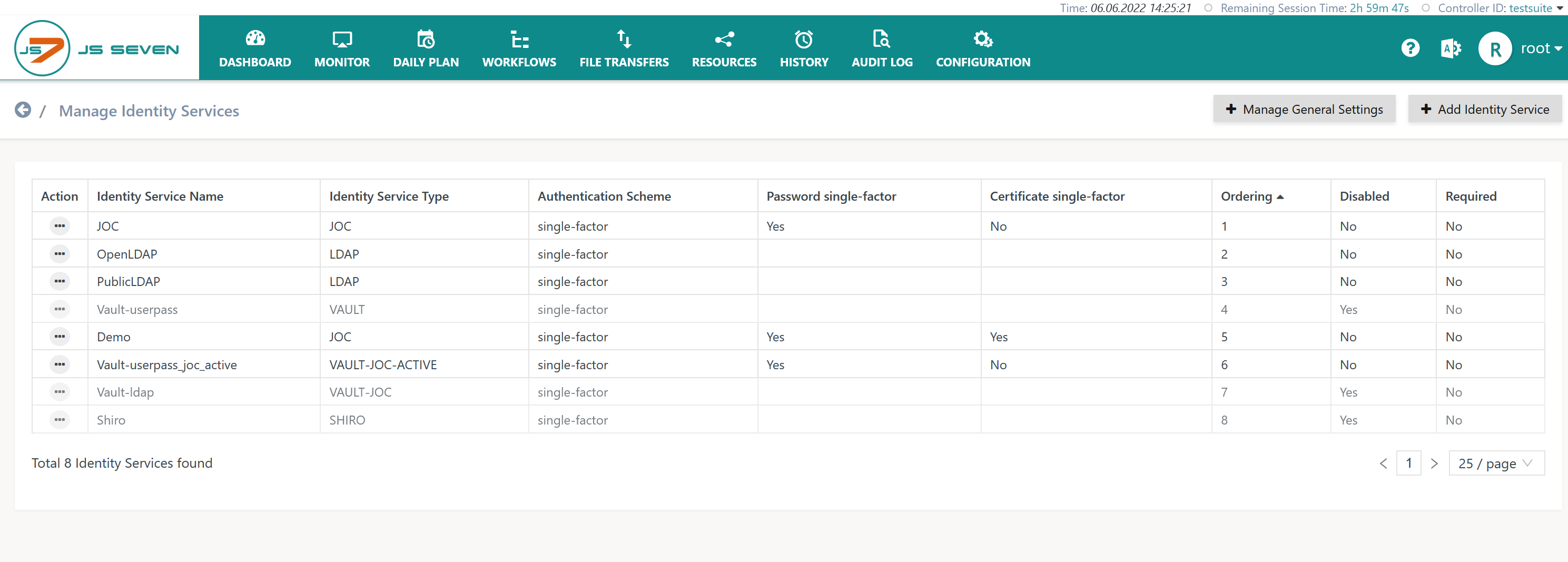
Manage Identity Services
The operation to manage Identity Services is available from the user menu of an administrative user account in the right upper corner of any JOC Cockpit page:
This operation brings forward the list of available Identity Services.
- By default the built-in JOC Identity Service is available.
- The Shiro Identity Service is available for migration purposes up to release 2.3.0.
Add Identity Service
To add an Identity Service use the button Add Identity Service from the above list of Identity Services:
Explanation:
- The
Identity Service Namecan be freely chosen. - The
Identity Service Typecan be selected as available from the above matrix. - The
Orderingspecifies the sequence in which a login is performed with available Identity Services. - The
Requiredthe attribute specifies if login with the respective Identity Service is required to be successful, for example if a number of Identity Services are triggered on login of a user account. - The
Identity Service Authentication Schemeallows to selectsingle-factorauthentication: user account and password are specified for login with the Identity Service.two-factorauthentication: in addition or as an alternative to user account and password a Client Authentication Certificate is required, see JS7 - Certificate based Authentication
Manage User Accounts and Roles
Manage Settings
Settings are available at a global level and per Identity Service.
Global Settings
Global settings are applied for all Identity Services.
Explanation:
Session Idle Timeout- Should the lifetime of a token provided by an external Identity Service be different from the max. idle-timeout then JOC Cockpit will try to renew the token with the Identity Service. Renewal of a token does not require the user to repeatedly specify credentials for login.
- Identity Services can restrict the lifetime of tokens and they can deny renewal of tokens. If a token cannot be renewed then the user session is terminated and the user is required to perform a login.
Initial Password- If an administrator adds user accounts with JOC Cockpit and does not specify a password then the
Initial Passwordwill be used. As a general rule JOC Cockpit does not allow to use empty passwords but populates them from theInitial Passwordif no password is specified by the user that adds or modifies an account. - In addition, the operation to reset a user account's password is available that will replace an existing password with the
Initial Password.
- If an administrator adds user accounts with JOC Cockpit and does not specify a password then the
Minimum Password Length- For any passwords specified - including the
Initial Password- a minimum length is specified. - Consider that the number and arbitrariness of characters are key factors for secure passwords. Password complexity requiring e.g. digits and special characters to be used do not add to password security except in case of short passwords.
- For any passwords specified - including the
Settings specific for Identity Services
Such settings are explained with the individual Identity Service:
- JS7 - JOC Identity Service
- JS7 - LDAP Identity Service
- JS7 - HashiCorp® Vault Identity Service.
- The Shiro Identity Service does not require any settings.
Interaction of Identity Services
A number of Identity Services can be used at the same time:
- Required Identity Services: user login is performed with all required Identity Services.
- No Optional Identity Services are considered.
- If more than one Required Identity Service is configured then a user cannot log in if the login fails with any of the Identity Services.
- Permissions from all Required Identity Services are merged.
- Optional Identity Services: with the first successful login to an Identity Service the user is considered being logged in.
- No further optional Identity Services are consulted if a user login is successful with one of the Optional Identity Services.
- For example, if two Optional Identity Services
JOCandLDAPare configured in this sequence then the login to theJOCIdentity Service can fail and still the user might successfully login with theLDAPIdentity Service. - Permissions from the successful login to an Optional Identity Service are used.
- Disabled Identity Services are not considered for user login.
Identity Services are ordered to specify the sequence of preferred use for authentication.
Further Resources
Pages
Navigation