Introduction
- The JS7 - Identity Services offer local management of user accounts for authentication and authorization.
- The JOC Identity Service is a built-in service available from JOC Cockpit
Identity Service Type
The following integration level is available from Identity Service Types that can be used with JOC:
| Identity Service | Identity Service Configuration Items | JOC Cockpit Configuration | ||||
|---|---|---|---|---|---|---|
| Service Type | Built-in | User Accounts/Passwords stored with | User Accounts/Passwords managed by | Roles/Permissions stored with | Roles->User Accounts Mapping managed with | Roles Mapping |
| JOC | yes | JS7 Database | JOC Cockpit | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit |
Explanation:
- Service Type:
JOC- Management of user accounts and passwords is performed with JOC Cockpit.
- The assignment of roles to user accounts is performed with JOC Cockpit.
- JOC Cockpit stores user accounts, hashed passwords and role assignments.
Identity Service Configuration
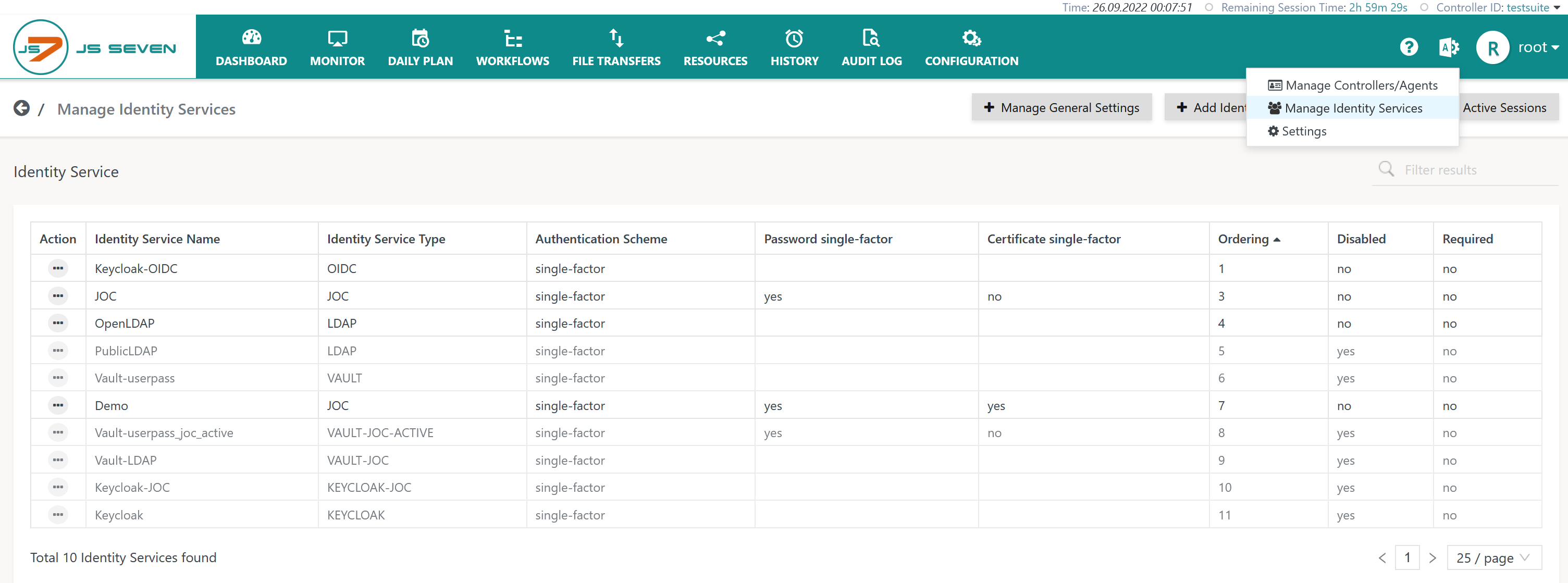
JOC Cockpit offers the Manage Identity Services view from the user menu of an administrative account for configuration of Identity Services:
Add Identity Service
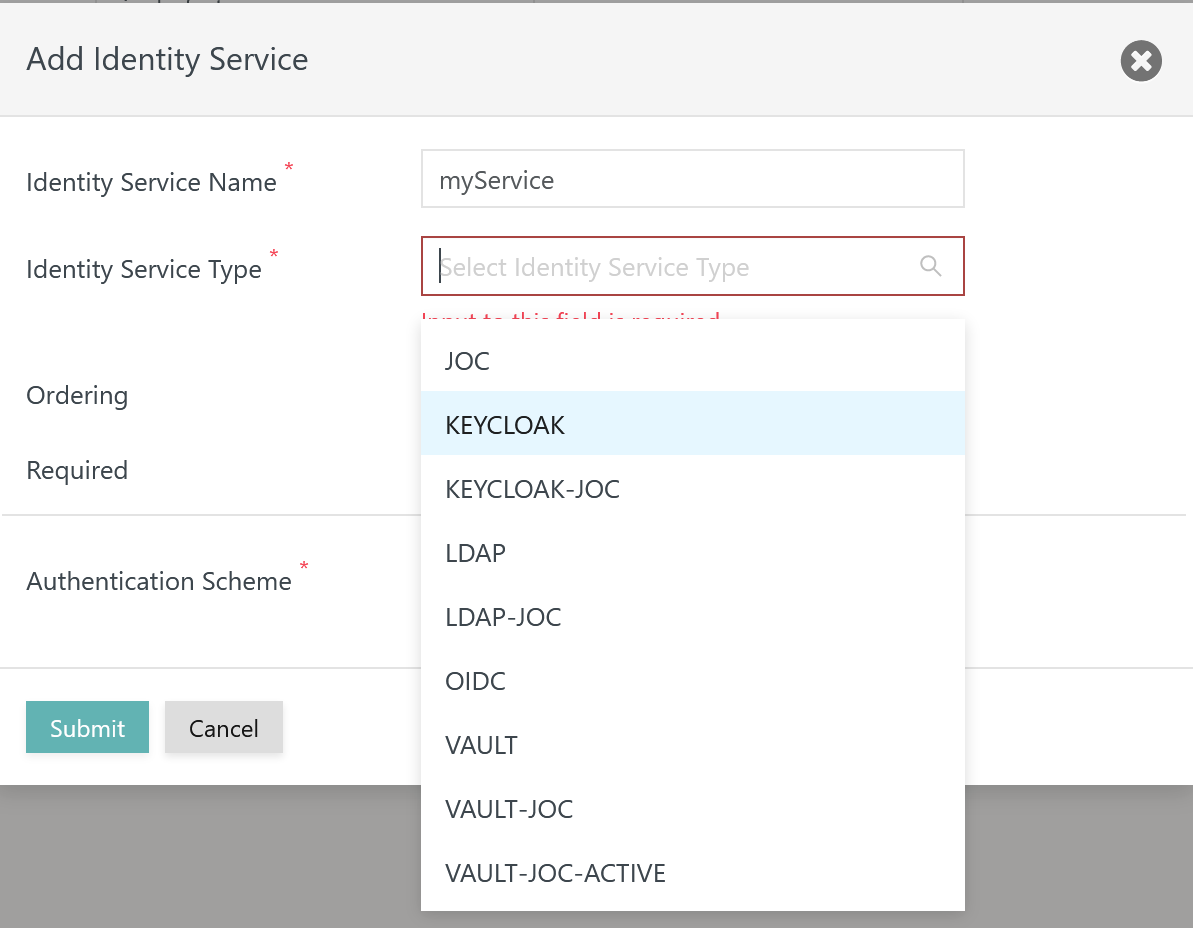
To add an Identity Service use the button Add Identity Service from the above list of Identity Services:
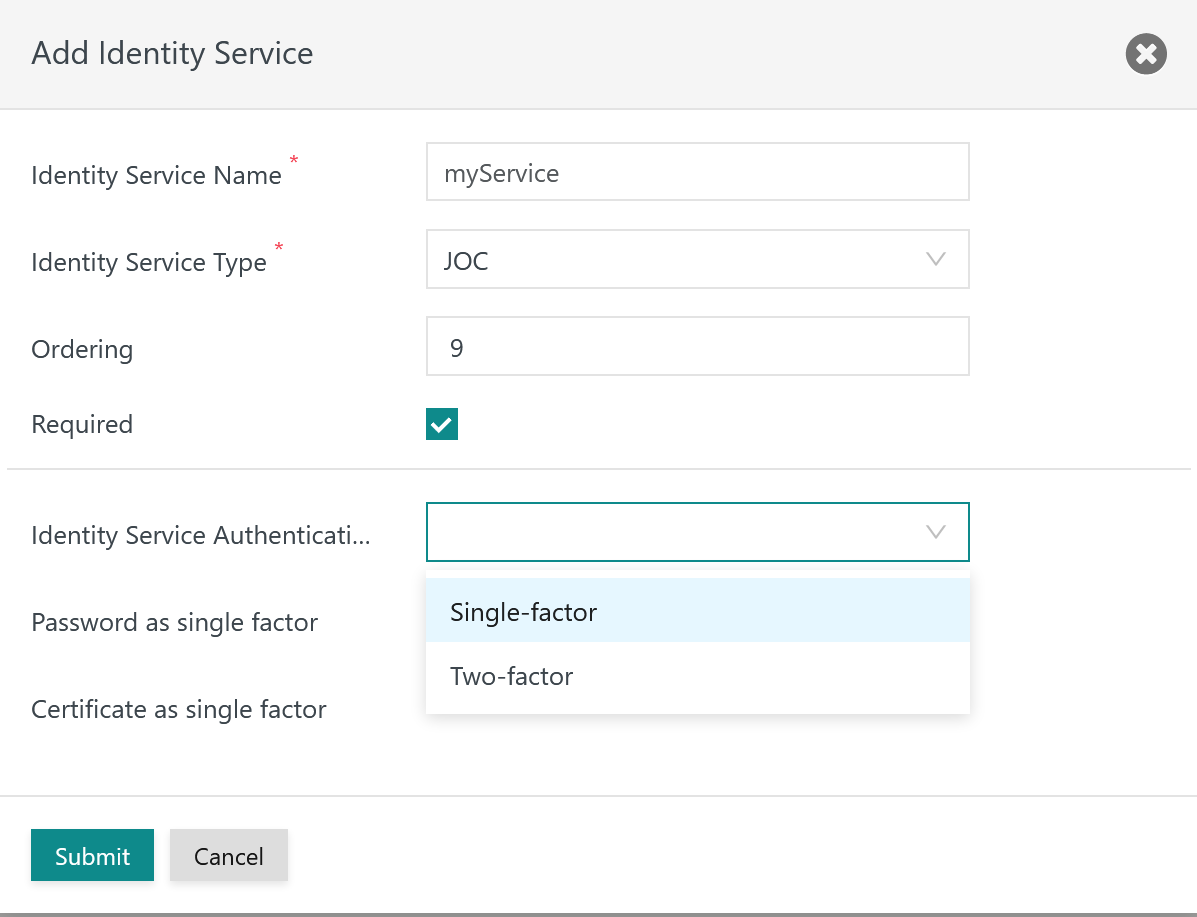
The remaining input fields for the popup window look like this:
Explanation:
- The
Identity Service Nameis a unique identifier that can be freely chosen. - The
Identity Service Typecan be selected as available from the above matrix. - The
Orderingspecifies the sequence in which a login is performed with available Identity Services. - The
Requiredattribute specifies if login with the respective Identity Service is required to be successful, for example if a number of Identity Services are triggered on login of a user account. - The
Identity Service Authentication Schemeallows to selectsingle-factorauthentication: user account and password are specified for login with the Identity Service.two-factorauthentication: in addition to user account and password a Client Authentication Certificate is required, see JS7 - Certificate based Authentication
Password as single factor: if the single-factorAuthentication Schemeis selected then this switch specifies if specification of the user account and password can be used to login.Certificate as single factor: if the single-factorAuthentication Schemeis selected then this switch specifies if use of a certificate - without specifying user account and password - allows to login.
Authentication Scheme
The Authentication Scheme allows a number of options how to authenticate with JOC Cockpit:
- Two-factor authentication forces a user to provide both the user account/password and a certificate. As certificates are stored in the user's local certificate store they represent a factor that limits access to specific client devices equipped with a certificate store. The user account/password is considered a factor that is in a user's mind.
- Single-factor authentication gives a choice to use one of user/password or certificate authentication.
Certificate Based Authentication
- Certificate based authentication makes use of the Common Name that is available from the certificate's subject and that maps to the user account that is managed with JOC Cockpit. Certificates cannot be used for authentication if the user account indicated by the Common Name has not been added to the Identity Service.
- When used with two-factor authentication then the certificate's Common Name has to exactly match the user account specified during login.
- When used with single-factor authentication then the certificate's Common Name has to exactly match a user account available with JOC Cockpit.
- Certificates act as a replacement for passwords. This can be useful for external scripts and for JS7 jobs that access the JS7 - REST Web Service API and that should not store passwords with their configuration. For example the JS7 - Monitoring interface is offered for external scripts, e.g. for System Monitors, to check availability of JS7 components on a regular basis. Such scripts can use a certificate that maps to a JOC Cockpit user account with limited permissions to request the health status of JS7 components only.
Identity Service Settings
No settings are required for use of the JOC Identity Service.
Logging
- Log Files
- Standard Log Files
- Identity Services log output to the
JETTY_BASE/logs/joc.logfile. This includes to report success or failure of authentication. - Successful and failed authentication attempts including user accounts involved are logged to the
JETTY_BASE/logs/audit.logfile.
- Identity Services log output to the
- Debug Log Files
- For problem analysis during setup of an Identity Service increase the log level as explained with JS7 - Log Levels and Debug Options.
- The
JETTY_BASE/logs/joc-debug.logfile includes general debug output of JOC Cockpit. - The
JETTY_BASE/logs/authentication-debug.logfile includes debug output related to authentication and authorization. - The
JETTY_BASE/logs/jetty.logfile includes debug output of attempts to establish SSL connections.