Introduction
- The JS7 - Identity Services offer integration with LDAP Directory Services for authentication and authorization.
- The LDAP Identity Service is a built-in service available from JOC Cockpit
Identity Service Type
The following integration levels are available from Identity Service Types that can be used with LDAP:
| Identity Service | Identity Service Configuration Items | JOC Cockpit Configuration | ||||
|---|---|---|---|---|---|---|
| Service Type | Built-in | User Accounts/Passwords stored with | User Accounts/Passwords managed by | Roles/Permissions stored with | Roles->User Accounts Mapping managed with | Roles Mapping |
| LDAP | yes | LDAP Server | LDAP Server | JS7 Database | LDAP Server | Mapping of LDAP Security Groups to JOC Cockpit Roles performed with the LDAP Server |
| LDAP-JOC | yes | LDAP Server | LDAP Server | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit |
Explanation:
- Service Type:
LDAP- Management of user accounts and passwords is performed with the LDAP Server.
- In addition, an automated mapping of membership in LDAP Security Groups to JOC Cockpit roles takes place.
- JOC Cockpit does not know any user accounts, passwords an role assignments as this information is managed with LDAP only.
- Service Type:
LDAP-JOC- Management of user accounts and passwords is performed with the LDAP Server.
- The assignment of roles to user accounts is performed with JOC Cockpit and is stored with the JS7 database.
- JOC Cockpit knows user accounts and role assignments. JOC Cockpit does not know passwords as this information is managed with LDAP only
Identity Service Configuration
JOC Cockpit offers the Manage Identity Services view from the user menu of an administrative account for configuration of Identity Services:
Add Identity Service
To add an Identity Service use the button Add Identity Service from the above list of Identity Services:
Explanation:
- The
Identity Service Nameis a unique identifier that can be freely chosen. - The
Identity Service Typecan be selected as available from the above matrix. - The
Orderingspecifies the sequence in which a login is performed with available Identity Services. - The
Requiredattribute specifies if login with the respective Identity Service is required to be successful, for example if a number of Identity Services are triggered on login of a user account. - The
Identity Service Authentication Schemeallows to selectsingle-factorauthentication: user account and password are specified for login with the LDAP Identity Service.two-factorauthentication: in addition to user account and password a Client Authentication Certificate is required, see JS7 - Certificate based Authentication
Identity Service Settings
Having added an LDAP Identity Service it is required to add settings for the LDAP integration from the Identity Service's action menu item Manage Settings:
For use of the LDAP Identity Service
- the LDAP Server product has to be installed and has to be accessible for JOC Cockpit,
- settings are required for configuration in a Simple Mode and Expert Mode.
Simple Mode Configuration
This configuration mode is intended for
Explanation:
LDAP Server Host: Expects the hostname or IP address of the LDAP Server host. If TLS/SSL protocols are used then the Fully Qualified Domain Name (FQDN) of the host has to be used for which the LDAP Server SSL certificate is issued.LDAP Protocol: The LDAP Protocol can be Plain Text, TLS or SSL. Plain Text is not recommended as the user account and password will be sent through the network without encryption. TLS and SSL protocols are considered being secure as they encrypt the connection to the LDAP Server.LDAP Server Port: The port that the LDAP Server is listening to. For Plain Text and TLS connections frequently port389is used, for SSL connections port636is a frequent option.LDAP Server is Active Directory: This setting simplifies the configuration if the LDAP Server is implemented by Active Directory. A number of attributes for user search and group search are automatically assumed if Active Directory is used.LDAP Server offers sAMAccountName attribute: ThesAMAccountNameattribute is the unique identifier of a user account. This attribute frequently is available with LDAP Servers of type Active Directory.LDAP Server offers memberOf attribute: ThememberOfattribute simplifies the search for Security Groups for which the user account has membership. This attribute frequently is available with LDAP Servers of type Active Directory, however, other LDAP products similarly can implement this attribute.LDAP Search Base: TheSearch Basefor looking up user accounts in the hierarchy of LDAP Server entries, for exampleOU=Operations,O=IT,O=Users,DC=example,DC=com.LDAP User Search Filter: TheUser Search Filterspecifies an LDAP query that is used to identify the user account in the hierarchy of LDAP entries.
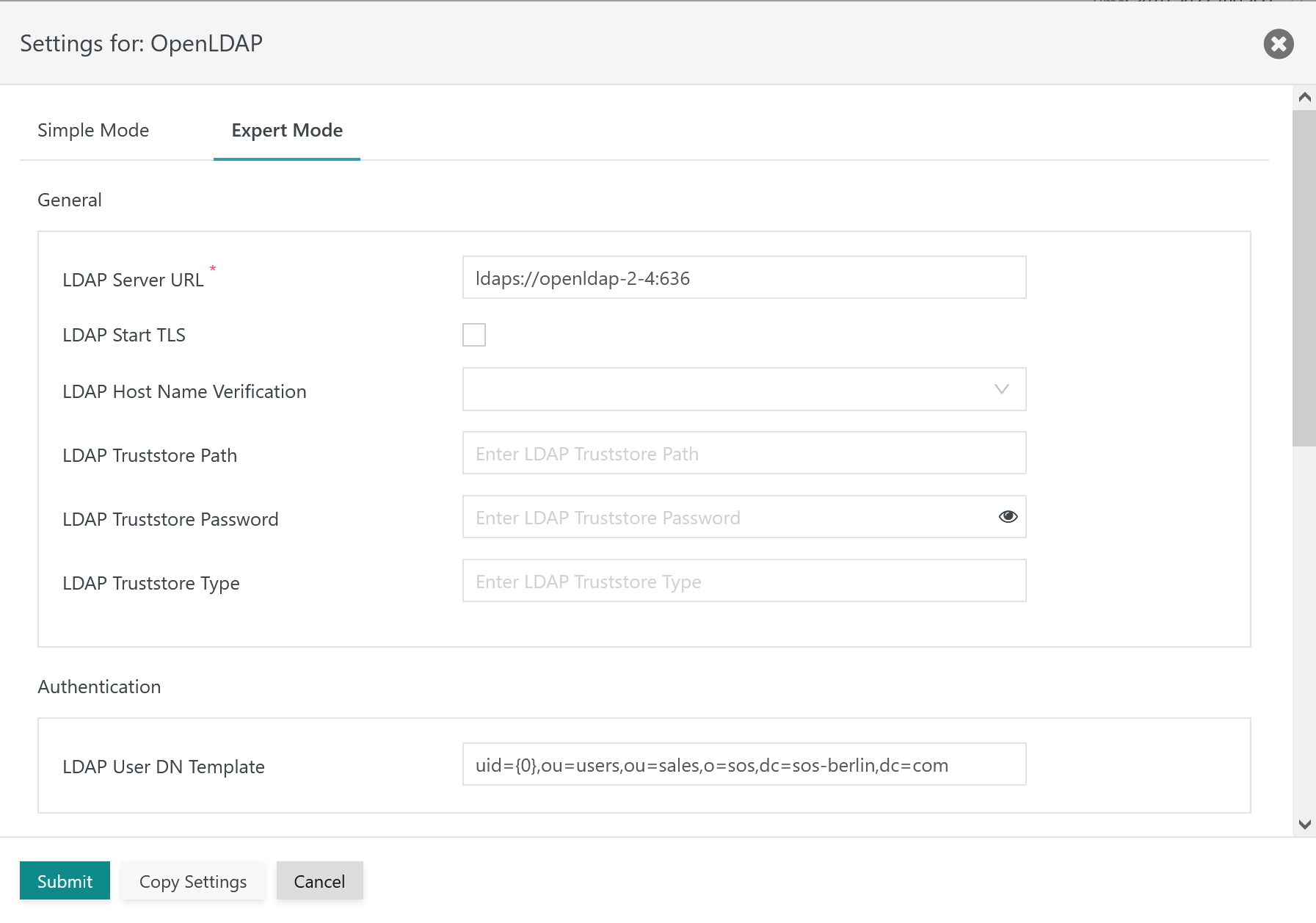
Expert Mode Configuration
This configuration mode is intended for users who intend to use LDAP for authentication and authorization:
The remaining settings in this mode look like this:
x