Introduction
- The JS7 - Identity Services offer integration with HashiCorp® Vault authentication server.
- The Vault Identity Service integration is available from JOC Cockpit:
- This requires HashiCorp® Vault to be downloaded, installed and operated by the user. Vault is not a built-in identity service and does not ship with JS7.
- JS7 implements a REST client for use with HashiCorp® Vault 1.7.0 and newer.
Identity Service Types
The following integration levels are available from identity service types that can be used with Vault:
| Identity Service | Identity Service Configuration Items | JOC Cockpit Configuration | ||||
|---|---|---|---|---|---|---|
| Service Type | Built-in | User Accounts/Passwords stored with | User Accounts/Passwords managed by | Roles/Permissions stored with | Assignment Roles->User Accounts managed with | Roles Mapping |
| VAULT | no | Vault Server | Vault Server | JS7 Database | Vault Server | Mapping of Vault Policies to JOC Cockpit Roles |
| VAULT-JOC | no | Vault Server | Vault Server | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit |
| VAULT-JOC-ACTIVE | no | Vault Server | Vault Server / JOC Cockpit | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit |
Explanation:
- Service Type: VAULT
- Management of user accounts and passwords is performed with the Vault Server.
- In addition, an automated mapping of policies - assigned a user account in Vault - to JOC Cockpit roles takes place.
- JOC Cockpit does not know any user accounts, passwords an role assignments as this information is managed with Vault only.
- Service Type: VAULT-JOC
- Management of user accounts and passwords is performed with the Vault Server.
- The assignment of roles to user accounts is performed with JOC Cockpit and is stored with the JS7 database.
- JOC Cockpit knows user accounts and role assignments. JOC Cockpit does not know passwords as this information is managed with Vault only
- Service Type: VAULT-JOC-ACTIVE
- Management of user accounts and passwords is performed with JOC Cockpit. JOC Cockpit forwards user accounts and passwords to the Vault Server. JOC Cockpit stores users accounts (not: passwords) in the JS7 database.
- The assignment of roles to user accounts is performed with JOC Cockpit and is stored with the JS7 database.
- JOC Cockpit knows user accounts and role assignments. JOC Cockpit temporarily knows passwords until this information is forwarded to Vault.
Vault Authentication Methods
JS7 supports the following authentication methods with Vault:
- Username & Password
- LDAP
It is not required to use Vault to connect to an LDAP Directory Service as there is a built-in JS7 - LDAP Identity Service for this purpose.
JS7 does not support cloud based authentication methods with Vault as such methods are typically used for engineering and administration of cloud services that are not related to an application such as JS7.
Vault Server Configuration
Application Role
If the VAULT-JOC-ACTIVE identity service type is used then an Application Role has to be created and a token has to be generated that is added to the JOC Cockpit configuration of the Vault identity service.
Authentication Methods
Username & Password
- The authentication method has to be added to Vault.
- The path of the authentication method has to be added to the JOC Cockpit identity service configuration.
- If the VAULT identity service type is used then
- user accounts are managed exclusively with Vault,
- policies have to be set up in Vault with names that exactly match the names of roles in JOC Cockpit.
- a user account will be assigned the roles matching policy names when performing a login to JOC Cockpit.
- it is not required to add specific permissions to policies with Vault.
- If the VAULT-JOC identity service type is used then
- user accounts are managed with Vault.
- user accounts are added to JOC Cockpit to allow assignment of roles:
- user accounts in Vault an JOC Cockpit have to match as otherwise the user account is not assigned a role.
- no passwords are managed by JOC Cockpit.
- If the VAULT-JOC-ACTIVE identity service type is used then
- user accounts are managed with JOC Cockpit and are stored with Vault.
- user accounts are assigned roles with JOC Cockpit.
LDAP
- It is not required to use Vault to connect to an LDAP Directory Service as there is a built-in JS7 - LDAP Identity Service for this purpose.
- The authentication method has to be added to Vault.
- The path of the authentication method has to be added to the JOC Cockpit identity service configuration.
- User accounts are managed with Vault.
- User accounts are added to JOC Cockpit to allow assignment of roles:
- user accounts in Vault an JOC Cockpit have to match as otherwise the user account is not assigned a role.
- no passwords are managed by JOC Cockpit.
Identity Service Configuration
JOC Cockpit offers the Manage Identity Services view for configuration:
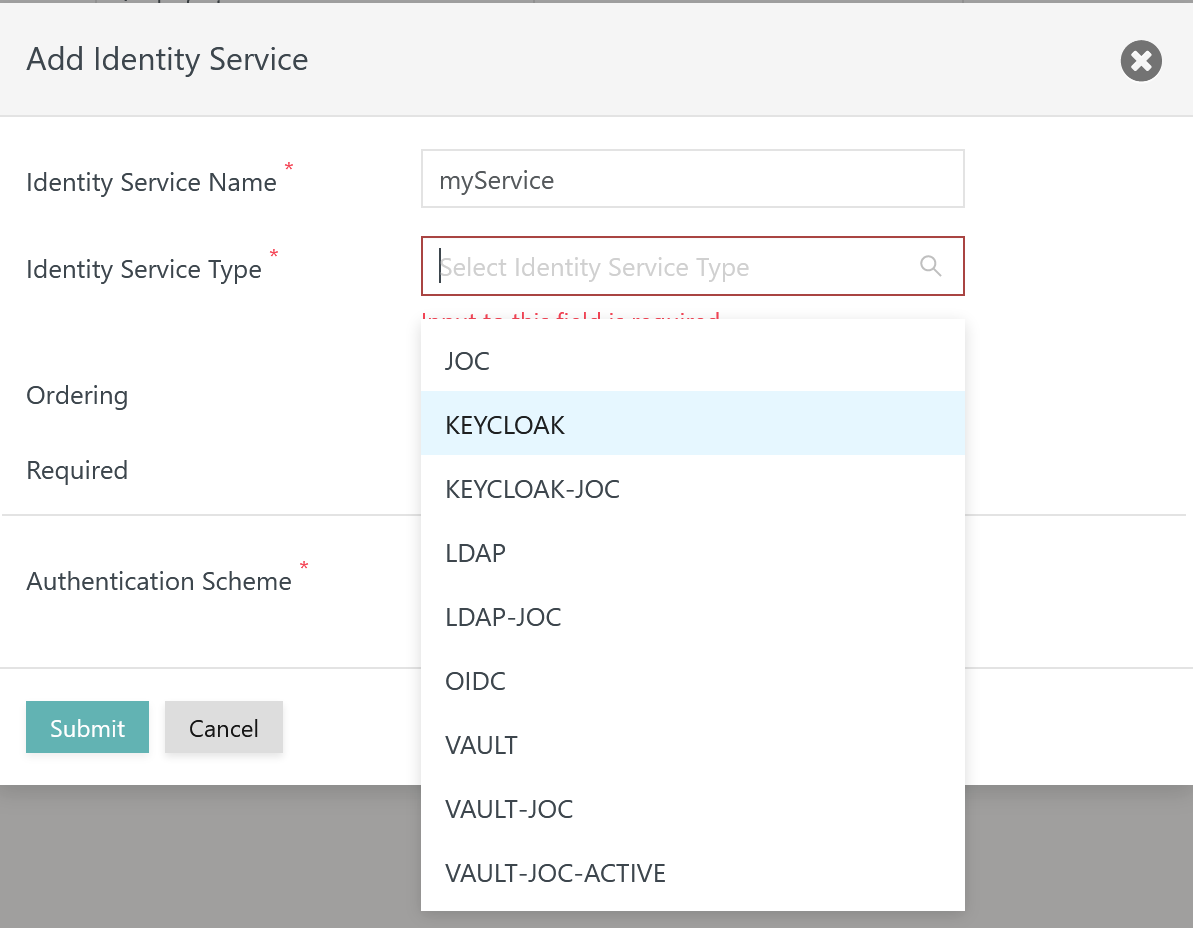
Add Identity Service
To add an Identity Service use the button Add Identity Service from the above list of Identity Services:
Explanation:
- The
Nameof the Identity Service can be freely chosen. - The Identity Service
Typecan be selected as available from the above matrix. - The
Orderingspecifies the sequence in which a login is performed with available Identity Services. - The
Requiredthe attribute specifies if login with the respective Identity Service is required to be successful
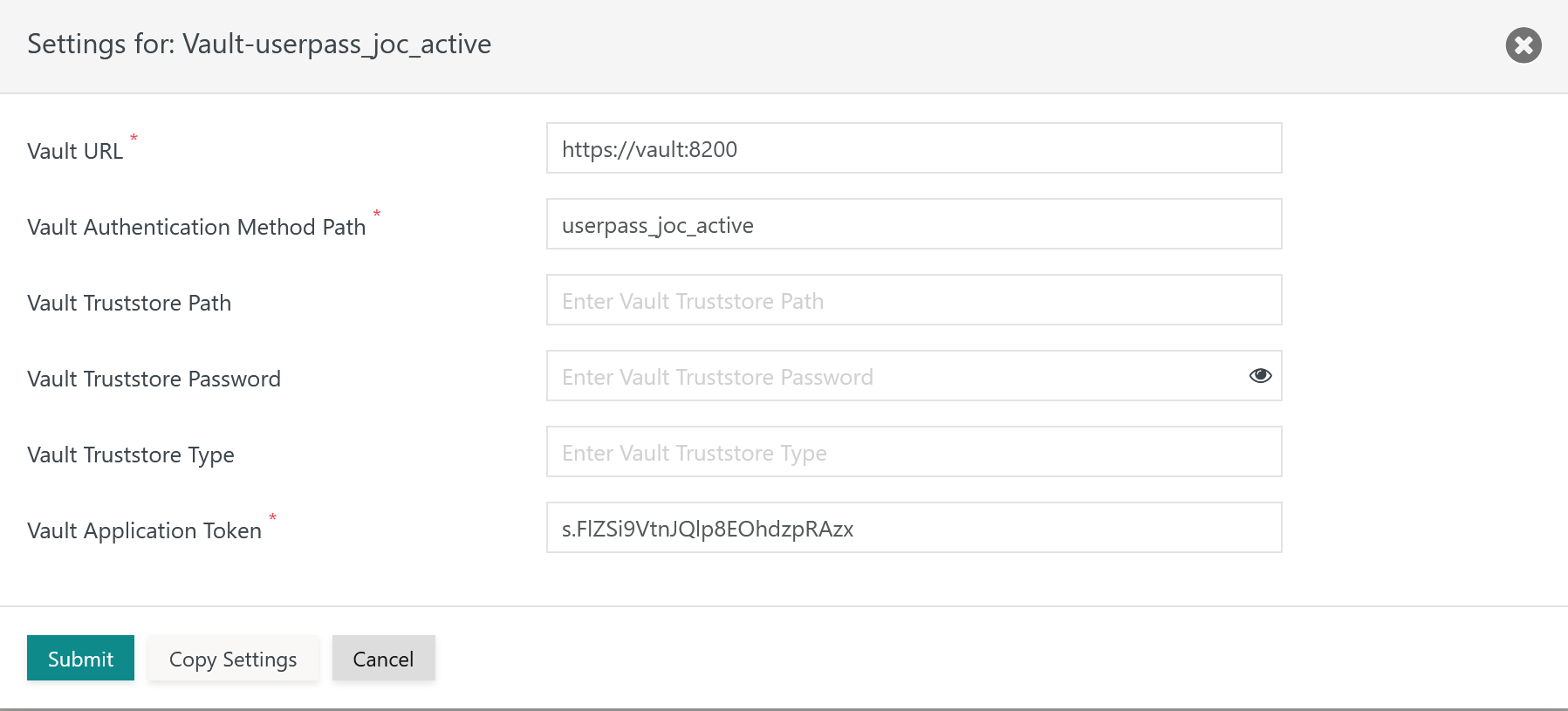
Vault Identity Service Settings
For use of the HashiCorp® Vault Identity Service
- the Vault product has to be installed and accessible for JOC Cockpit,
- the following settings have to be specified:
Explanation:
Vault URL: the base URL for which the Vault REST API is availableVault Keystore Path: Should the Vault REST API be configured for HTTPS Mutual Authentication then the indicated keystore has to include the private key specified for the extended key usage ofClient Authentication.Vault Keystore Password: Should the Vault REST API be configured for HTTPS Mutual Authentication and the indicated keystore be protected by a password then the password has to be specified.Vault Key Password: Should the Vault REST API be configured for HTTPS Mutual Authentication and the indicated private key be protected by a password then the password has to be specified.Vault Keystore Type: Should the Vault REST API be configured for HTTPS Mutual Authentication then the type of the indicated keystore has to be specified being eitherPKCS12orJKS.Vault Truststore Path: Should the Vault REST API be configured for HTTPS then the indicated truststore has to include an X.509 certificate specified for the extended key usage ofServer Authentication. This can be a self-signed server certificate or a CA-signed certificate (typically the Root CA certificate is used as otherwise the complete certificate chain involved in signing the server certificate has to be available with the truststore).Vault Truststore Password: Should the Vault REST API be configured for HTTPS and the indicated truststore be protected by a password then the password has to be specified.Vault Truststore Type: Should the Vault REST API be configured for HTTPS then the type of the indicated truststore has to be specified being eitherPKCS12orJKS.Vault Application Token: The application token has to be created by Vault for JOC Cockpit. It allows to access the Vault REST API and e.g. to renew tokens for user sessions.