Introduction
The JOC Cockpit comes with an editor for Managing Authentication and Authorization - the Manage Accounts view. FEATURE AVAILABILITY STARTING FROM RELEASE 1.11.2
Permissions Hierarchy
Permissions are configured hierarchically:
- User Account
- Role(s)
- Permission(s)
- Role(s)
In addition permissions can be specified for specific:
- JobScheduler Master IDs and
- Folders within a JobScheduler's live folder.
Using the Manage Accounts view
Getting Started
After installing the JOC Cockpit, log in with the default root:root user name and password.
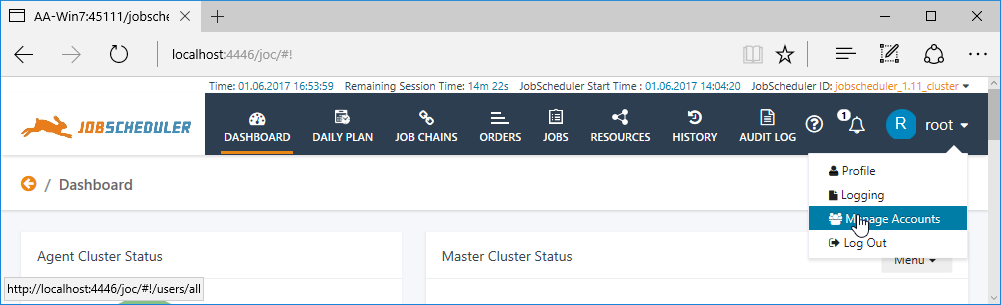
The Manage Accounts section of the JOC Cockpit is then accessed via the Profile Menu as shown in the screenshot below.
The Account Manager has three main Views:
- Accounts: for the configuration of User Accounts. Accounts configured here use shiro name / password Authentication.
- Note that while Shiro authentication is not as secure as, for example, LDAP, it provides a convenient basis for configuring authorization in a test environment.
- See the JOC Cockpit - Authentication and Authorization article for more information about Shiro and other methods of authentication that can be used with the JOC Cockpit.
- Masters: for configuring the JobScheduler Masters that can be accessed by a Role
- Permissions: for configuring access to Folders and the Permissions for a Role
These views will be described in the following sections.
The Accounts View
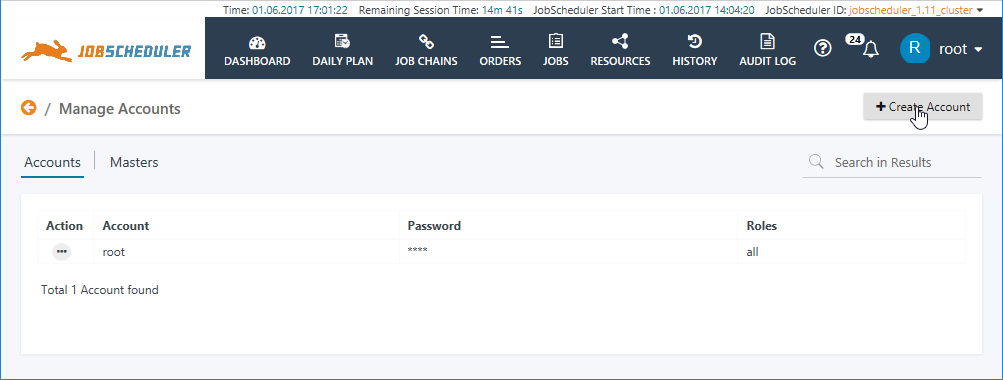
The Accounts view is the view that is opened first when a user selects the Manage Accounts view and lists all the User Accounts that have been configured along with the Roles they have been assigned.
The above screenshot shows the default root User Account which is the only Account that is configured after installation of the JOC Cockpit.
The Create Account button is used to open a window to add a new User Account - clicking on the additional option (ellipsis) symbol or the Account name brings the user to the Masters view (described below) where the Account Name, Password and Role(s) allocated can be edited.
The Masters View
The main purpose of the Masters view is to allow JobScheduler Master Roles to be configured.
When the view is first opened after installation of the JOC Cockpit it will appear as shown in the next screenshot:
The above screen shows seven default roles that are provided with the JOC Cockpit. These Roles are intended to help system administrators get a realistic authorization configuration working as quickly as possible and can be modified as required. These roles are valid for all JobScheduler Master instances in the environment.
Positioning the mouse over a role name blends in two links as shown in the screenshot above:
- the pencil link allows the role to be edited and
- the X link allows the role to be deleted.
A set of Permissions is configured for each Role. Each Permissions set can be inspected by clicking on the Role name in the Masters view list. An example Permissions set is described in the next section.
The Permissions View
The main purpose of the Permissions view is to allow Permissions and Folders to be configured for each Role.
The screenshot below shows the default permissions for the administrator Role.
Individual Permissions can be modified and removed from the Role using the pencil and X symbols that are blended in when the user's mouse is moved over a Permission:
- The Edit function allows the the Permission to be made subtractive - i.e. for a permission granted at a higher level to be removed.
The Folder part of the view is for restricting the Role to accessing particular Folders - and thereby particular Jobs, Job Chains, etc - within a JobScheduler Master's live folder and will be described later.
Editing Permissions is described below .
Initial Configuration
Adding User Accounts and Roles
The following example describes how to add User Accounts to the JOC Cockpit in addition to the default root user account. Each User Account will be assigned one of the default Roles described in the Masters View section above and for simplicity will use the same name as the Role they will be given.
To add a Business User Account:
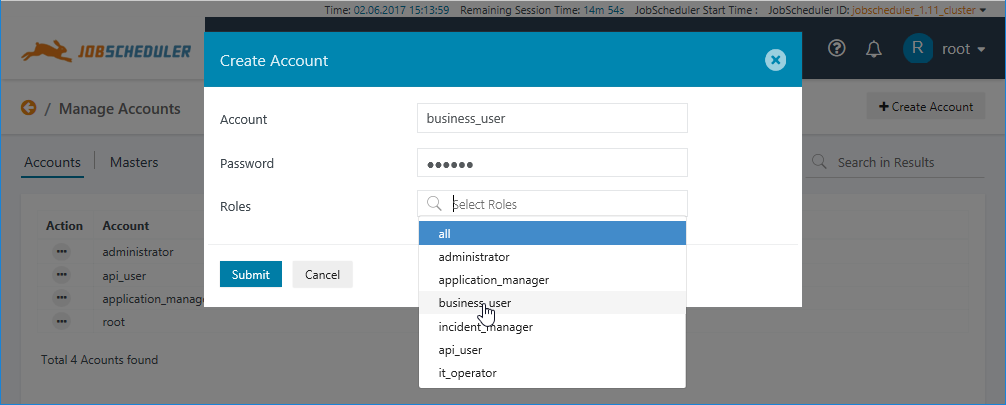
- Go to the Accounts view and click on the Create Account button at the top right.
- This will open the following window:
- Account Names may not contain spaces.
- Selecting the business_user Role from the list will avoid possible errors from a mistyped role name.
- It will be clear form the functioning of the Roles selection that any number of Roles can be specified for a User Account if required.
- Click the Submit Button to save the Account configuration.
- Note that if one of the Accounts should contain a configuration error (such as a blank space in an Account Name), none of the Accounts will be saved to the configuration file.
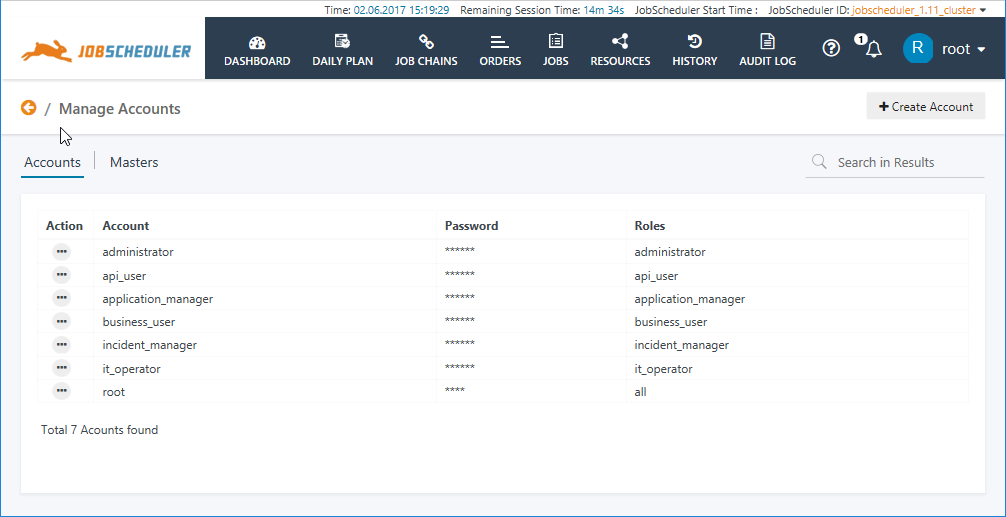
Once a User Account has been created for each of the default Rolesole, the Accounts view would look like:
Account Use
The root User can now be logged out via the Profile Menu and the other User Accounts used.
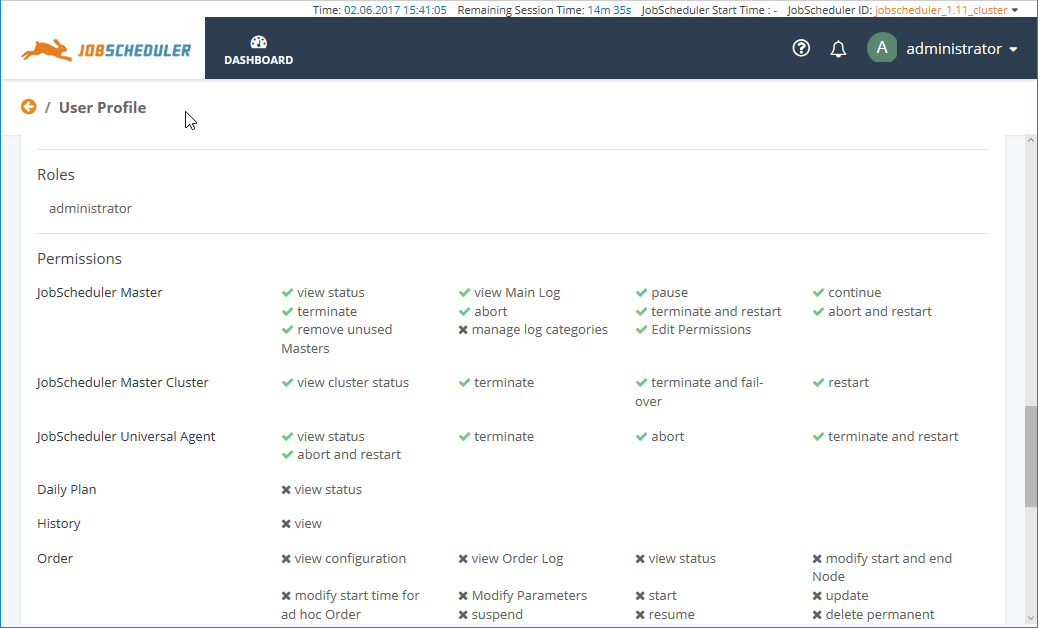
Individual Users can check - but not change - the Permissions they have been granted in the Profile View for their Account as can be seen in the following screenshot which shows part of the Permissions section for Administrator Account with the default administrator Role.
Note that as the default administrator Role is granted a limited Permissions set, the Main Menu Bar in the JOC Cockpit only contains a link to the Dashboard view as can be seen in the screenshot below. In contrast, the root User Account has links for a further seven views (see the screenshots above).
By default the administrator Role is granted Permissions for the Manage Accounts view and therefore the configuration of the User Accounts will continue using this Account rather than root.
A matrix describing and listing the Permissions that are granted by default for the default Roles is available in the Authentication and Authorization - Permissions for the JOC Cockpit Web Service article.
In addition, the same article contains a link to a full list of all Permissions that can be granted.
Editing User Permissions
Permissions Structure
Permissions are hierarchical:
- A Role with the Permission
sos:products:joc_cockpit:jobscheduler_master:view'only' allows a User to view JobScheduler Masters while a User with the 'higher'sos:products:joc_cockpit:jobscheduler_masterPermission is able not only to view JobScheduler Masters but able to carry out all other operations - view, execute and administrate.
Editing Permissions
Consider the default business_user Role, which has the following permission:
sos:products:joc_cockpit:jobscheduler_master:view:status
This permission does not allow the business_user Role to access JobScheduler Master log files or parameters which would be granted individually with the following Permissions:
sos:products:joc_cockpit:jobscheduler_master:view:mainlogsos:products:joc_cockpit:jobscheduler_master:view:parameters
The following Permissions can be set to allow the business_user Role to view JobScheduler Master statuses and log files but not parameters:
sos:products:joc_cockpit:jobscheduler_master:view:statussos:products:joc_cockpit:jobscheduler_master:view:mainlog
Alternatively, it may make sense in some situations to grant the Role a higher level Permission and then remove specific Permissions. This approach is shown in the following combination:
sos:products:joc_cockpit:jobscheduler_master:view-sos:products:joc_cockpit:jobscheduler_master:view:parameters
where the ...jobscheduler_master:view Permission is an overall 'view' Permission and the -sos:...jobscheduler_master:view Permission is removed from the :parametersbusiness_user Role.
Caution
Users have to have a Role with the following Permission - or higher - before they are able to log into the JOC Cockpit:
sos:products:joc_cockpit:jobscheduler_master:view:status
Editing Procedures
Three editing procedures are available:
- Adding Permissions:
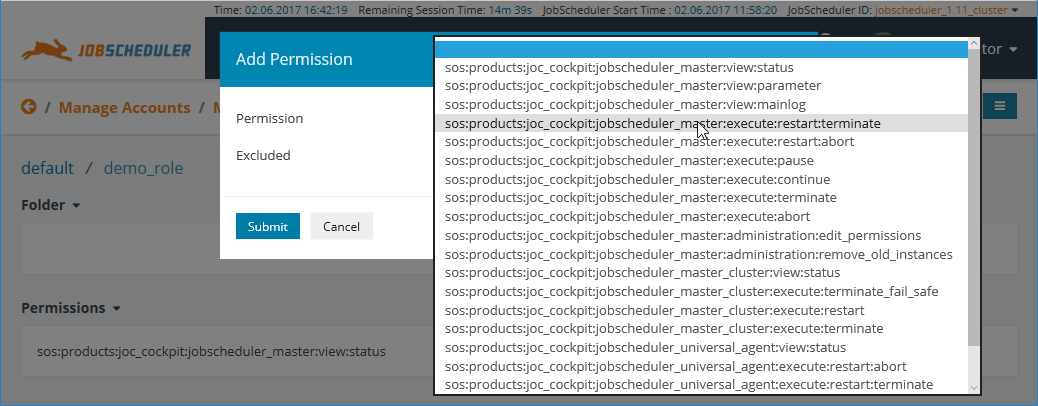
- The Add Permission button in the Permissions View allows a Permission to be selected from a list of all available Permissions as shown in the screenshot below.
- Note that the Permissions listed are all individual Permissions. They can be edited to make them higher level / less specific.
- For example, the screenshot below shows that the
...jobscheduler_master:execute:restart:terminatepermission in the process being selected. - Once selected the Permission can be edited before the Submit button is clicked. This allows, for example, the Permission to be modified to
..., allowing the Role to carry out all operations covered by this Permission. These are:jobscheduler_master:execute:restartsos:products:joccockpit:jobscheduler_master:execute:restart:terminatesos:products:joccockpit:jobscheduler_master:execute:restart:abort
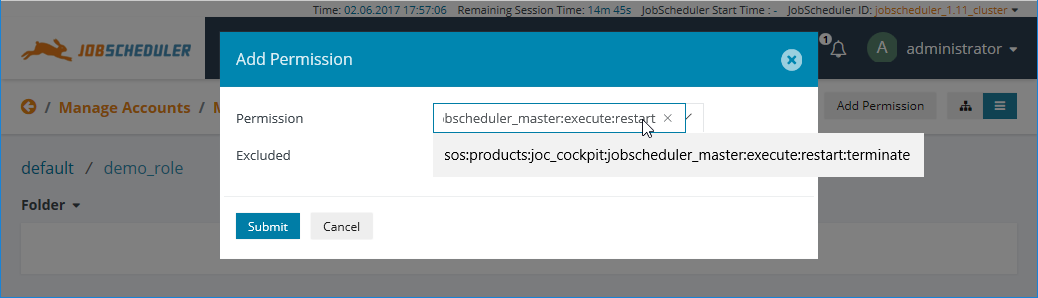
- The following screenshot shows the edited version alongside the original:
- The editing function can also be used to make a selected permission subtractive - i.e. to remove a specific part of a higher level Permission.
- This is done by directly prefixing the Permission with a minus symbol - i.e. without a space between the minus and the Permission.
- For example, the screenshot below shows that the
- Note that the Permissions listed are all individual Permissions. They can be edited to make them higher level / less specific.
- The Add Permission button in the Permissions View allows a Permission to be selected from a list of all available Permissions as shown in the screenshot below.
- Modifying Existing Permissions:
- The pencil symbol shown alongside existing Permissions in the Permissions view (shown in the screenshot above) can be used to change the function of a Permission in a Role - to make an additive Permission subtractive and vice-versa. It cannot be used to edit a Permission.
- The X symbol shown alongside existing Permissions in the Permissions view can be used to remove an existing Permission from a Role.
- Graphical Permissions Editing:
- ...
JobSchedulers
By default Permissions are granted for all the JobScheduler Masters and JobScheduler Master Clusters in an environment.
Folders
Folders are used to restrict User access to JobScheduler Objects such as Jobs, Orders and Schedules. This means that, for example, Users can be can be restricted to accessing only Objects for particular mandators / clients.
By default Permissions are granted for all the folders within a JobScheduler's live folder. However Roles can be restricted to accessing specific folders within a live folder.
This is done by granting a Folder Permission, i.e. Permissions to view the content of a Folder. When this is done, the Permissions to view all other Folders are automatically revoked.
Granting Folder Permissions
Folder Permissions are granted in the Permissions View. Note that before Folder Permissions can be saved for a Role, the Role has to be specified for a User. In the example below, a demo_user and demo_role as well as a demo Folder have already been configured.
To open the Permissions view for a particular Role, first open the Manage Accounts Masters view and select the Role that is to be granted Folder Permissions. To do this, click on the Role name in the Roles list.
Now click on the Add Folders button and in the Add Folders modal window, specify the folder Path either by:
- entering the Path relative to the JobScheduler Master's live Folder (e.g.
/demoor/demo/*) or - clicking on the folder icon to open a tree view of the live Folder and selecting the Folder as shown in the screenshot below:
Note that the JobScheduler will have to be restarted if the Folder for the Permissions has been added with a File manager - and not JOE - before the folder will show in the tree view.
Check the Recursive box in the Add Folders modal window if required and then click on Submit.
Any User that is allocated this demo_role will now only be able to see JobScheduler Objects in the demo_folder.
Note that the demo_user will only be able to log in to the JOC Cockpit if they have at least one Role granting them the following Permission:
sos:products:joc_cockpit:jobscheduler_master:view:status
Roles with Folder Permissions are often configured for Users in combination with default Roles. For example, if the demo_user described here was allocated the it_operator Role in addition to the demo_role, they would be able to carry out the tasks allowed by the default IT Operator Permissions but only for JobScheduler Objects in the demo folder and, if configured, its child Folders. See the Use Case below for an example configuration.
Use Cases
Multi-Mandator Scheduling
A JobScheduler Master can be used to provide job scheduling services for a number of mandators / clients and ensure that Users such as operators or support staff associated with one mandator do not have access to scheduling activities or configuration information for another mandator. This is achieved by configuring a combination of Roles and Folder Permissions.
Consider a JobScheduler Master carrying out scheduler activities for two clients mandator A and mandator B:
- The JobScheduler's
liveFolder is structured as follows:livemandator_a_folder(for all Jobs, Orders, etc. for this client)mandator_b_folder(for all Jobs, Orders, etc. for this client)sos(the default folder for Housekeeping and other Jobs, Orders, etc.)
- Incident management for each mandator is carried out by separate User with the default incident_manager Role and a Role with Folder Permissions restricting them to the respective mandator Folder- i.e.
mandator_a_im_user(Incident Manager User for mandator A)- incident_manager (common default Role)
- mandator_a_role (mandator-specific Role)
mandator_a_folder(Folder Permission)
mandator_b_im_user(Incident Manager User for mandator B)- incident_manager (common default Role)
- mandator_b_role (mandator-specific Role)
mandator_b_folder(Folder Permission)
The above configuration means that the incident manager Users for mandator A and mandator B will only be able to see the Jobs, Orders, log files, and other possibly confidential information for their respective mandator.
See the Folders Section (above) for instructions about configuring Folder Permissions.
Example Files
A working example of the above use case can be downloaded from this link:
When unpacked three archive elements will shown:
- two folders:
mandator_a_folderandmandator_b_folderand
- a
shiro.iniconfiguration file.
Copy the two folders with all their contents to your JobScheduler's live folder. It is not necessary to delete any of the existing folders.
Make a backup of the current shiro.ini file in the /joc/resources/joc folder and then overwrite the current shiro.ini file from the version from the download archive. See the Installation Instructions for the JobScheduler and JOC Cockpit for information about the default location of these folders.
Each of the mandator folders contains a hello_world sub-folder with job chains and orders that are scheduled to run once an hour.
The shiro.ini file contains a configuration based on the shiro.ini file delivered with the JOC Cockpit installation with the following roles active:
| User | Role | Password |
|---|---|---|
| root | all | root |
| administrator | administrator | secret |
| api_user | api_user | secret |
| application_manager | application_manager | secret |
| business_user | business_user | secret |
| incident_manager | incident_manager | secret |
| it_operator | it_operator | secret |
In addition the following mandator-specific Users and Roles have been configured:
| User | Roles | Password |
|---|---|---|
| mandator_a_bu_user | mandator_a_role business_user | secret |
| mandator_a_im_user | mandator_a_role incident_manager | secret |
| mandator_a_ito_user | mandator_a_role it_operator | secret |
| mandator_b_bu_user | mandator_b_role business_user | secret |
| mandator_b_im_user | mandator_b_role incident_manager | secret |
| mandator_b_ito_user | mandator_b_role it_operator | secret |
Explanation
Holders of the three mandator_a_* user accounts are only able to access the Jobs, Orders, Schedules, etc in the relevant mandator_*_folder and its sub-folders. In addition, access to Run Plan, History, Audit Log and log file information is only available to user accounts with the correct Permissions,
Note that the user accounts with the it_operator Role are the only ones configured in this example that have the necessary Permissions to start Orders.