LDAP Configuration items
There are some configuration items that configure the ldap realm that should be used. These items can not be changed with the Account Management in JOC.
...
| Table of Contents |
|---|
We refere in this document to a public LDAP server. To configure a realm for accessing the public LDAP server please add
| Code Block | ||
|---|---|---|
| ||
publicLdapRealm = |
...
com.sos.auth.shiro.SOSLdapAuthorizingRealm publicLdapRealm.userDnTemplate = uid={0},dc=example,dc=com publicLdapRealm.searchBase = dc=example,dc=com publicLdapRealm.contextFactory.url = ldap://ldap.forumsys.com:389 publicLdapRealm.groupNameAttribute = ou publicLdapRealm.userNameAttribute = uid publicLdapRealm.userSearchFilter = (uniqueMember=uid=%s,dc=example,dc=com) publicLdapRealm.groupRolesMap = \ scientists : it_operator, \ mathematics: all |
There are some configuration items that configure the ldap realm that should be used. These items can not be changed with the Account Management in JOC.
| Key | Value | Description |
|---|---|---|
| ldapReam | The key is the name of the realm. You can define any name. The name is taken as a reference to set the properties of the realm. The value is the name of the class that implements the realm. The implementation from SOS extends | |
ldapRealm.contextFactory.url | ldap://host:port | The host and the port of your LDAP server. You can check whether the server is reachable with Make sure that the firewall is open for the given port. |
ldapRealm.useStartTls | true|false | To enable starttls set the value to true (Default is Please note the the server must be prepared to serve with Starttls. To check this, you can use a LDAP browser like "Softerra LDAP Browser". Configure your LDAP Server there and click the "Enable Starttls Button" On Client Site you will need the certificate and you have to add the certificate to your truststore. The path of your truststore is definied in the JOC configuration file joc.properties.
e.g.
|
ldapRealm.hostNameVerification | on|off true|false | To enable the host name verification of the certificate. The default is off. |
rolePermissionResolver | com.sos.auth.shiro.SOSPermissionResolverAdapterSOSLdapAuthorizingRealm | The implementationkey is the name of the permission resolver. The SOS implementation sets anrealm. You can define any name. The name is taken as a reference to set the properties of the realm. The value is the name of the class that implements the realm. The implementation from SOS extends shiro.ini in the same way it is done when using the iniRealm. |
ldapRealm.rolePermissionResolver | $rolePermissionResolver | Sets the role permission resolver for the ldap realm. |
securityManager.realms | $ldapRealm | Sets the list of realm that should be used for authentication. This is a comma seperated list of realms. e.g.
|
| Code Block |
|---|
[main]
...
ldapRealm = com.sos.auth.shiro.SOSLdapAuthorizingRealm
ldapRealm.contextFactory.url = ldap://myHost:389
ldapRealm.useStartTls = true
ldapRealm.hostNameVerification = off
rolePermissionResolver = com.sos.auth.shiro.SOSPermissionResolverAdapter
rolePermissionResolver.ini = $iniRealm
ldapRealm.rolePermissionResolver = $rolePermissionResolver
securityManager.realms = $ldapRealm
...
|
Authentication
| ||
ldapRealm.contextFactory.url | ldap://host:port | The host and the port of your LDAP server. You can check whether the server is reachable with Make sure that the firewall is open for the given port. |
ldapRealm.useStartTls | true|false | To enable starttls set the value to true (Default is Please note the the server must be prepared to serve with Starttls. To check this, you can use a LDAP browser like "Softerra LDAP Browser". Configure your LDAP Server there and click the "Enable Starttls Button" On Client Site you will need the certificate and you have to add the certificate to your truststore. The path of your truststore is definied in the JOC configuration file joc.properties.
e.g.
|
ldapRealm.hostNameVerification | on|off true|false | To enable the host name verification of the certificate. The default is off. |
rolePermissionResolver | com.sos.auth.shiro.SOSPermissionResolverAdapter | The implementation of the permission resolver. The SOS implementation sets an org.apache.shiro.realm.text.IniRealm to resolve the permissions. That means that the permissions a role have are specified in the configuration file shiro.ini in the same way it is done when using the iniRealm. |
ldapRealm.rolePermissionResolver | $rolePermissionResolver | Sets the role permission resolver for the ldap realm. |
securityManager.realms | $ldapRealm | Sets the list of realm that should be used for authentication. This is a comma seperated list of realms. e.g.
|
| Code Block |
|---|
[main]
...
ldapRealm = com.sos.auth.shiro.SOSLdapAuthorizingRealm
ldapRealm.contextFactory.url = ldap://myHost:389
ldapRealm.useStartTls = true
ldapRealm.hostNameVerification = off
rolePermissionResolver = com.sos.auth.shiro.SOSPermissionResolverAdapter
rolePermissionResolver.ini = $iniRealm
ldapRealm.rolePermissionResolver = $rolePermissionResolver
securityManager.realms = $ldapRealm
...
|
Authentication
With the authentication you will check for a valid username/password combination. To achive this, you have to specify the userDnTemplate.
Username
The username is part of the login patterns
- username@domain
- domain\username
- username
Username may have blanks if they are stored in a LDAP directory. Usernames stored in the configuration file shiro.ini may not have blanks.
When refering to usernames from the LDAP directory to keys in the [users] section to assign roles to the user, you have to change blanks to %20. The password must be empty. When you login with a domain the reference must contain the whole domain/username pattern e.g. user@domain
Configuration in the configuration file shiro.ini
Examples:
- Example
ldapRealm.userDnTemplate = uid={0},ou=People, dc=sos
- Configuration with public LDAP Server
publicLdapRealm.userDnTemplate = uid={0},dc=example,dc=com
- Configuration with a Microsoft AD
adLdapRealm.userDnTemplate = sAMAccountName={0},dc=company,dc=com
- Try this at first.
ldapRealm.userDnTemplate = {}
Verification with ldapSearch
In all ldapSearch examples the option -x is used. It is possible that your LDAP Server does not allow this and you have to specify a user and a password like:
ldapsearch -h ldap.forumsys.com -p 389 -b "uid=gauss,dc=example,dc=com" -W -D "uid=gauss,dc=example,dc=com"
You can check you userDnTemplate with this ldapSearchCommand.
ldapsearch -h localhost -p 389 -b "uid=ur,ou=People, dc=sos" -x
Should give a result like:
| Code Block | ||||
|---|---|---|---|---|
| ||||
# ur, People, sos
dn: uid=ur,ou=People,dc=sos
mail: uwe.risse@sos-berlin.com
uid: ur
givenName: Uwe
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: inetorgperson
sn: Risse
cn: Uwe Risse
preferredLanguage: de
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
|
Example with the public server
ldapsearch -h ldap.forumsys.com -p 389 -b "uid=gauss,dc=example,dc=com" -x
| Code Block | ||||
|---|---|---|---|---|
| ||||
# extended LDIF
#
# LDAPv3
# base <uid=gauss,dc=example,dc=com> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# gauss, example.com
dn: uid=gauss,dc=example,dc=com
objectClass: inetOrgPerson
objectClass: organizationalPerson
objectClass: person
objectClass: top
cn: Carl Friedrich Gauss
sn: Gauss
uid: gauss
mail: gauss@ldap.forumsys.com
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
|
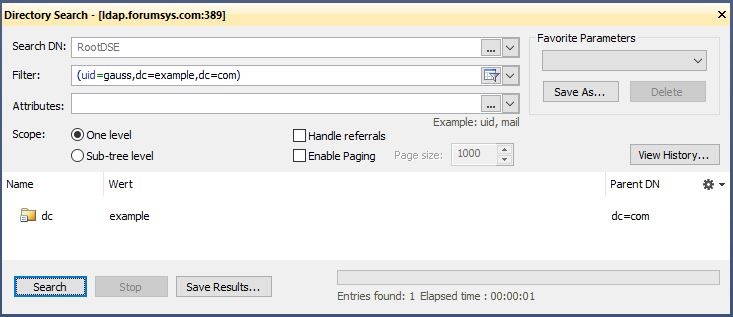
Verification mit Softerra LDAP Browser
Search from root with the userDnTemplate as the user search filter. You should find exactly one entry.
Authorization
Assigning roles from shiro.ini
...