Introduction
Installation, updates, upgrades, patching and uninstallation are performed by use of the Agent Installation Script. The script makes use of the .tar.gz/.zip archives provided for initial installation of newer releases.
- JS7 - Installation instructions apply.
- For environments with a larger number of Agents the installation, update, upgrade, patch and uninstallation processes can be automated in a number of ways:
- Users can apply the Agent Installation Script that is described in this article.
- Users can automate packaging and deployment of Agents, see JS7 - Deployment.
- Users can apply the Agent Installation Script with their preferred tools such as Ansible®, Puppet®, Chef®.
Security
Secure rollout of JS7 products is critical. It is therefore recommended that the solution described here is adjusted to suit specific security needs.
- Rollout of JS7 Agents is considered critical as the software allows jobs to be executed on a larger number of servers.
- Integrity of the sources for downloads of JS7 products deserves attention.
- This includes intermediate devices to which JS7 software installers are stored in a user's environment.
- It is an option to run the Agent Installation Script from
sudoand to use the digest functionality that compares the script to a hash value stored with thesudoersfile.
- The solution provided for updating, upgrading and patching JS7 Agents is based on shell scripting by design:
- to provide readability and to rely on OS commands only,
- to deny the use of any 3rd-party components and additional dependencies that require code to be executed on the machines that run Agents.
- The Agent Installation Script can be integrated in a number of ways:
- by running one's own SSH scripts on top of the Agent Installation Script,
- by use with tools such as Ansible®, Puppet® that make use of an SSH Client,
- by use of JS7 workflow automation as explained below.
- It is recommended that a separate standalone Controller and Agent are set up for deployment purposes, for details see JS7 - Deployment.
- Access to the Controller and Agent for rollout should be securely managed.
- JS7 Agents can be rolled out from a Controller to which the Agents are not registered.
Agent Installation Script
The Agent Installation Script is provided for download and can be used to automate updates, upgrades and patches of JS7 Agents.
- The script is available for Linux, MacOS®, AIX®, Solaris® using bash, dash, ksh and zsh POSIX-compatible shells. For AIX®, Solaris® automated installation is supported, automated configuration is not.
- The script can be used to install, update or patch an Agent using the installation options. In addition it can be used to configure an Agent, for example in case of certificate renewal.
- The script creates
- the
agent_<http-port>.shInstance Start Script in the Agent'sbindirectory if no such file exists, - the
agent_<http-port>.servicesystemd Service File in the Agent'sbindirectory, see JS7 - systemd Service Files for automated Startup and Shutdown with Unix Systems.
- the
- The script terminates with exit code 0 to signal success, with exit code 1 for command line argument errors and with exit code 2 for non-recoverable errors.
- The script is intended as a baseline example for customization by JS7 users and by SOS within the scope of professional services.
- See the information in the JS7 - Agent Command Line Operation article.
Download
Find the Agent Installation Script for download from JS7 - Download.
Usage
Invoking the Agent Installation Script without arguments displays the usage clause:
Usage: js7_install_agent.sh [Options] [Switches]
Installation Options:
--home=<directory> | required: directory to which the Agent will be installed
--data=<directory> | optional: directory for Agent data files, default: <home>/var_4445
--config=<directory> | optional: directory from which the Agent reads configuration files, default: <data>/config
--logs=<directory> | optional: directory to which the Agent writes log files, default: <data>/logs
--work=<directory> | optional: working directory of the Agent, default: <data>
--user=<account> | optional: user account for Agent daemon, default: $USER
--home-owner=<account[:group]> | optional: account and optionally group owning the home directory, requires root or sudo permissions
--data-owner=<account[:group]> | optional: account and optionally group owning the data directory, requires root or sudo permissions
--release=<release-number> | optional: release number such as 2.5.0 for download if --tarball is not used
--tarball=<tar-gz-archive> | optional: the path to a .tar.gz archive that holds the Agent installation or patch tarball,
| if not specified the Agent tarball will be downloaded from the SOS web site
--patch=<issue-key> | optional: identifies a patch for a Change Management issue key
--patch-jar=<jar-file> | optional: the path to a .jar file that holds the patch
--license-key=<key-file> | optional: specifies the path to a license key file to be installed
--license-bin=<binary-file> | optional: specifies the path to the js7-license.jar binary file for licensed code to be installed
| if not specified the file will be downloaded from the SOS web site
--http-port=<port> | optional: specifies the http port the Agent will be operated for, default: 4445
port can be prefixed by network interface, e.g. localhost:4445
--https-port=<port> | optional: specifies the https port the Agent will be operated for
port can be prefixed by network interface, e.g. batch.example.com:4445
--pid-file-dir=<directory> | optional: directory to which the Agent writes its PID file, default: <data>/logs
--pid-file-name=<file-name> | optional: file name used by the Agent to write its PID file, default: agent.pid
--instance-script=<file> | optional: path to the Instance Start Script that will be copied to the Agent, default <home>/bin/<instance-script>
--backup-dir=<directory> | optional: backup directory for existing Agent home directory
--log-dir=<directory> | optional: log directory for log output of this script
--exec-start=<command> | optional: command to start the Agent, e.g. 'StartService'
--exec-stop=<command> | optional: command to stop the Agent, e.g. 'StopService'
--return-values=<file> | optional: path to a file that holds return values such as the path to a log file
Configuration Options:
--deploy-dir=<dir>[,<dir>] | optional: deployment directory from which configuration files are copied to the Agent
--agent-conf=<file> | optional: path to a configuration file that will be copied to <config>/agent.conf
--private-conf=<file> | optional: path to a configuration file that will be copied to <config>/private/private.conf
--controller-id=<identifier> | optional: Controller ID, default: controller
--controller-primary-cert=<file> | optional: path to Primary/Standalone Controller certificate file
--controller-secondary-cert=<file> | optional: path to Secondary Controller certificate file
--controller-primary-subject=<id> | optional: subject of Primary/Standalone Controller certificate
--controller-secondary-subject=<id> | optional: subject of Secondary Controller certificate
--agent-cluster-id=<identifier> | optional: Agent Cluster ID
--director-primary-cert=<file> | optional: path to Primary/Standalone Director Agent certificate file
--director-secondary-cert=<file> | optional: path to Secondary Director Agent certificate file
--director-primary-subject=<id> | optional: subject of Primary Director Agent certificate
--director-secondary-subject=<id> | optional: subject of Secondary Director Agent certificate
--keystore=<file> | optional: path to a PKCS12 keystore file that will be copied to <config>/private/
--keystore-password=<password> | optional: password for access to keystore
--keystore-alias=<alias> | optional: alias name for keystore entry
--client-keystore=<file> | optional: path to a PKCS12 client keystore file that will be copied to <config>/private/
--client-keystore-password=<pass> | optional: password for access to the client keystore
--client-keystore-alias=<alias> | optional: alias name for client keystore entry
--truststore=<file> | optional: path to a PKCS12 truststore file that will be copied to <config>/private/
--truststore-password=<password> | optional: password for access to truststore
--java-home=<directory> | optional: Java Home directory for use with the Instance Start Script
--java-options=<options> | optional: Java Options for use with the Instance Start Script
--service-dir=<directory> | optional: systemd service directory, default: /usr/lib/systemd/system
--service-file=<file> | optional: path to a systemd service file that will be copied to <home>/bin/
--service-name=<identifier> | optional: name of the systemd service to be created, default js7_agent_<http-port>
Switches:
-h | --help | displays usage
--force-sudo | forces use of sudo for operations on directories
--active | makes Director Agent instance the default active node in an Agent Cluster
--standby | makes Director Agent instance the default standby node in an Agent Cluster
--no-yade | excludes YADE from Agent installation
--no-install | skips Agent installation, performs configuration updates only
--use-install | uses existing Agent installation, populates data directory and creates service
--uninstall | uninstalls Agent and removes <home> and <data> directories
--uninstall_home | uninstalls Agent and removes <home> directory only
--uninstall_data | uninstalls Agent and removes <data> directory only
--service-selinux | use SELinux version of systemd service file
--show-logs | shows log output of the script
--make-dirs | creates the specified directories if they do not exist
--make-service | creates the systemd service for the Agent
--move-libs | moves an existing Agent's lib directory instead of removing the directory
--remove-journal | removes an existing Agent's state directory that holds the journal files
--restart | stops a running Agent including tasks and starts the Agent after installation
--wait | waits for running tasks in Agent if used with the --restart switch
--cancel | cancels a running Agent if used with the --restart switch
Installation Options
--home- Specifies the directory in which the Agent should be installed.
--data- Specifies the directory in which Agent data such as configuration files should be stored.
- By default the
<home>/var_<http-port>directory is used, see options--homeand--http-port.
--config- Specifies the directory from which the Agent reads configuration files.
- By default the
<data>/configdirectory is used, see option--data.
--logs- Specifies the directory to which the Agent stores log files.
- By default the
<data>/logsdirectory is used, see option--data.
--work- Specifies the working directory of the Agent.
- By default the
<data>directory is used, see option--data.
--user- Specifies the user account for the Agent daemon running as a systemd service.
- By default the account of the user running the Agent Installation Script is used.
- Should the the home or data directory be owned by an account that is different from the one running the Agent Installation Script then consider use of the
--home-ownerand--data-owneroptions.
--home-owner- Optionally specifies the user account and group that should own the home directory. By default the home directory is created and owned by the current user account.
- Syntactically a user account and optionally a group can be specified, for example
--home-owner=sosor--home-owner=sos:sos. If the group is not specified then a group with the name of the user account is assumed. - Use of this option requires
sudopermissions for the user account that runs the Agent Installation Script.
--data-owner- Optionally specifies the user account and group that should own the data directory. By default the data directory is created and owned by the current user account.
- Syntactically a user account and optionally a group can be specified, for example
--data-owner=sosor--data-owner=sos:sos. If the group is not specified then a group with the name of the user account is assumed. - Use of this option requires
sudopermissions for the user account that runs the Agent Installation Script.
- --release
- Specifies a release number such as 2.3.1 for download from the SOS web site if the
--tarballoption is not used.
- Specifies a release number such as 2.3.1 for download from the SOS web site if the
--tarball- Optionally specifies the path to a .tar.gz file that holds the Agent installation or patch files. If this option is not used the installation or patch tarball will be downloaded from the SOS web site for the release indicated with the
--releaseoption. - Download is performed with
curlthat considershttp_proxyandhttps_proxyenvironment variables and respective settings from a.curlrcfile.
- Optionally specifies the path to a .tar.gz file that holds the Agent installation or patch files. If this option is not used the installation or patch tarball will be downloaded from the SOS web site for the release indicated with the
--patch- A patch is identified by an issue key in the Change Management System, for example JS-1984.
- Patches are downloaded from the SOS web site if the
--tarballoption is not used. - Patches are added to the Agent's
<home>/lib/patchesdirectory. Note that thepatchessub-directory will be emptied when updating an Agent installation later on. - If a backup directory is specified then an Agent's existing installation directory will be added to a .tar.gz backup file in this directory.
--patch-jar- Optionally specifies the path to a .jar file that holds the patch if a patch is provided in this format.
--license-key- Optionally the path to a license key file is specified. Customers with a Commercial License receive the license key file from SOS in .pem or .crt format.
- For details see JS7 - How to apply a JS7 License Key.
--license-bin- Optionally the path to the
js7-license.jarbinary file is specified that includes code that is available for use with a Commercial License only, see JS7 - How to apply a JS7 License Key. - Should this option be omitted and a license key file be specified with the
--license-keyoption then the binary file is downloaded from the SOS Web Site, see JS7 - Download.
- Optionally the path to the
--http-port- Specifies the HTTP port that the Agent is operated for. The default value is
4445. The Agent by default makes use of a data directory<home>/var_<http-port>that will be excluded from a backup taken with the--backup-diroption. In addition the HTTP port is used to identify the Agent Instance Start Script typically available from the<home>/bin/agent_<http-port>.shscript and to specify the value of theJS7_AGENT_HTTP_PORTenvironment variable in the script. - The port can be prefixed by the network interface, for example
localhost:4445. - When used with the
--restartswitch the HTTP port is used to identify if the Agent is running.
- Specifies the HTTP port that the Agent is operated for. The default value is
--https-port- Specifies the HTTPS port that the Agent is operated for. The HTTPS port is specified in the Agent Instance Start Script typically available from the
<home>/bin/agent_<http-port>.shscript with the environment variableJS7_AGENT_HTTPS_PORT. Use of HTTPS requires a keystore and truststore to be present, see--keystoreand--truststoreoptions. - The port can be prefixed by the network interface, for example
batch.example.com:4445.
- Specifies the HTTPS port that the Agent is operated for. The HTTPS port is specified in the Agent Instance Start Script typically available from the
--pid-file-dir- Specifies the directory to which the Agent stores its PID file. By default the
<data>/logsdirectory is used. - When using SELinux then it is recommended to specify and to create the
/var/run/js7directory, see JS7 - How to install for SELinux.
- Specifies the directory to which the Agent stores its PID file. By default the
--pid-file-name- Specifies the name of the PID file. By default the file name
agent.pidis used. - The PID file is created in the directory specified by the
--pid-file-diroption.
- Specifies the name of the PID file. By default the file name
--instance-script- Specifies the path to an Instance Start Script that acts as a template and that is copied to the
<home>/bindirectory. Typically the nameagent_<http-port>.sh. is used. Users are free to choose any name for the Instance Start Script. The script has to be executable for the Agent daemon, see--useroption. Permissions of the script are not changed by the Agent Installation Script. - The Agent Installation Script will perform replacements in the Instance Start Script template for known placeholders such as
<JS7_AGENT_USER>, for details see<home>/bin/agent_instance.sh-example.
- Specifies the path to an Instance Start Script that acts as a template and that is copied to the
--backup-dir- If a backup directory is specified then an Agent's existing installation directory will be added to a .tar.gz file in this directory before applying changes to the Agent installation.
- File names are created according to the pattern:
backup_js7_agent.<hostname>.<release>.<yyyy>-<MM>-<dd>T<hh>-<mm>-<ss>.tar.gz- For example:
backup_js7_agent.centostest_primary.2.3.1.2022-03-19T20-50-45.tar.gz
- For example:
- A backup is intended to restore files in the Agent's installation directory, not in its data directory, see
--data. The purpose of a backup is to restore files that are replaced by the Agent Installation Script, its purpose is not to restore an Agent installation that otherwise is corrupted or removed. No backup will be taken if one of the--uninstalloptions is used.
--log-dir- If a log directory is specified then the Agent Installation Script will write information about processing steps to a log file in this directory.
- File names are created according to the pattern:
install_js7_agent.<hostname>.<yyyy>-<MM>-<dd>T<hh>-<mm>-<ss>.log - For example:
install_js7_agent.centostest_primary.2022-03-19T20-50-45.log
--exec-start- This option can be used should the Agent be started after installation. For example, when using systemd then the option
--exec-start="StartService"will start the Agent service provided that the related systemd service has been created manually or by use of the--make-serviceswitch. Alternatively users can specify individual commands, for example--exec-start="sudo systemctl start js7_agent_4445". - For systemd service files see the JS7 - systemd Service Files for automated Startup and Shutdown with Unix Systems article.
- This option is an alternative to the use of the
--restartswitch which will start the Agent from its Instance Start Script. If specified this option overrules the--restartswitch.
- This option can be used should the Agent be started after installation. For example, when using systemd then the option
--exec-stop- This option can be used should the Agent be stopped before installation. For example, when using systemd then the option
--exec-stop="StopService"will stop the Agent service provided that the related systemd service has been created manually or by use of the--make-serviceswitch. Alternatively users can specify individual commands, for example--exec-stop="sudo systemctl stop js7_agent_4445". - For systemd service files see the JS7 - systemd Service Files for automated Startup and Shutdown with Unix Systems article.
- This option is an alternative to the use of the -
-restartswitch which stops the Agent from its Instance Start Script. If specified this option overrules the--restartswitch.
- This option can be used should the Agent be stopped before installation. For example, when using systemd then the option
--return-values- Optionally specifies the path to a file to which return values will be added in the format
<name>=<key>. For example:log_file=install_js7_agent.centostest_primary.2022-03-20T04-54-31.logbackup_file=backup_js7_agent.centostest_primary.2.3.1.2022-03-20T04-54-31.tar.gz
- An existing file will be overwritten. It is recommended to use a unique file name such as
/tmp/return.$$.$RANDOM.properties. - A value from the file can be retrieved like this:
backup=$(cat /tmp/return.$$.$RANDOM.properties | grep "backup_file" | cut -d'=' -f2)
- Optionally specifies the path to a file to which return values will be added in the format
Configuration Options
--deploy-dir- Specifies the path to a deployment directory that holds configuration files and sub-directories that will be copied to the
<config>directory. A deployment directory allows to manage central copies of configuration files such asagent.conf,private.conf,log4j2.xmletc. - Use of a deployment directory has lower precedence as files can be overwritten by individual options such as
--agent-conf,--private-confetc.
- Specifies the path to a deployment directory that holds configuration files and sub-directories that will be copied to the
--agent-conf- Specifies the path to a configuration file for global JS7 - Agent Configuration Items. The file will be copied to the
<config>/agent.conffile. - Any path to a file can be used as a value of this option, however, the target file name
agent.confwill be used.
- Specifies the path to a configuration file for global JS7 - Agent Configuration Items. The file will be copied to the
--private-conf- Specifies the path to a configuration file for private JS7 - Agent Configuration Items. The file will be copied to the
<config>/private/private.conffile. - Any path to a file can be used as a value of this option, however, the target file name
private.confwill be used. - Users have a choice how to provide the required configuration:
- Download the private.conf-template-agent template, the Agent Installation Script performs replacements of placeholders in the template file from option values, for details see chapter Replacements.
- Users can manually adjust configuration items in the
private.conffile that they specify for the Agent Installation Script, see JS7 - Agent Configuration Items.
- Specifies the path to a configuration file for private JS7 - Agent Configuration Items. The file will be copied to the
--controller-id- Specifies the Controller ID, a unique identifier of the Controller installation. Agents will be dedicated to the Controller with the given Controller ID.
- The Controller ID is used in the Agent's
private.conffile to specify which Controller can access a given Agent.
--controller-primary-cert- Specifies the path to the SSL/TLS certificate of the Primary Controller instance. The Agent Installation Script extracts the distinguished name from the given certificate and adds it to the Agent's
private.conffile to allow HTTPS connections from the given Controller using mutual authentication without the need for passwords. - This option is used alternatively to
--controller-primary-subject.
- Specifies the path to the SSL/TLS certificate of the Primary Controller instance. The Agent Installation Script extracts the distinguished name from the given certificate and adds it to the Agent's
--controller-secondary-cert- Corresponds to the
--controller-primary-certoption and is used for the Secondary Controller instance. - This option is used alternatively to
--controller-secondary-subject.
- Corresponds to the
--controller-primary-subject- Specifies the subject (distinguished name) of the SSL/TLS certificate of the Primary Controller instance. The Agent Installation Script adds the distinguished name to the Agent's
private.conffile to allow HTTPS connections from the given Controller using mutual authentication without the need for passwords. - A certificate's subject can be extracted for example using the command:
openssl x509 -in controller.crt -noout -nameopt RFC2253 -subject - This option is used alternatively to
--controller-primary-cert.
- Specifies the subject (distinguished name) of the SSL/TLS certificate of the Primary Controller instance. The Agent Installation Script adds the distinguished name to the Agent's
--controller-secondary-subject- Corresponds to the
--controller-primary-subjectoption and is used for the Secondary Controller instance. - This option is used alternatively to
--controller-secondary-cert.
- Corresponds to the
--agent-cluster-id- Specifies the Agent Cluster ID, a unique identifier of the Agent Cluster. This is not the Primary/Secondary Director Agent ID.
- Subagents will be dedicated to the Agent Cluster with the given Agent Cluster ID.
- The Agent Cluster ID is used in the Agent's
private.conffile to specify which pairing Director Agent instance can access the given Director Agent instance.
--director-primary-cert- Specifies the path to the SSL/TLS certificate of the Primary Director Agent instance. The Agent Installation Script extracts the distinguished name from the given certificate and adds it to the Agent's
private.conffile to allow HTTPS connections from the given Director Agent instance using mutual authentication without the need for passwords. - This option is used alternatively to
--director-primary-subject.
- Specifies the path to the SSL/TLS certificate of the Primary Director Agent instance. The Agent Installation Script extracts the distinguished name from the given certificate and adds it to the Agent's
--director-secondary-cert- Corresponds to the
--director-primary-certoption and is used for the Secondary Director Agent instance. - This option is used alternatively to
--director-secondary-subject.
- Corresponds to the
--director-primary-subject- Specifies the subject (distinguished name) of the SSL/TLS certificate of the Primary Director Agent instance. The Agent Installation Script adds the distinguished name to the Agent's
private.conffile to allow HTTPS connections from the given Director Agent instance using mutual authentication without the need for passwords. - A certificate's subject can be extracted for example using the command:
openssl x509 -in agent.crt -noout -nameopt RFC2253 -subject - This option is used alternatively to
--director-primary-cert.
- Specifies the subject (distinguished name) of the SSL/TLS certificate of the Primary Director Agent instance. The Agent Installation Script adds the distinguished name to the Agent's
--director-secondary-subject- Corresponds to the
--director-primary-subjectoption and is used for the Secondary Director Agent instance. - This option is used alternatively to
--director-secondary-cert.
- Corresponds to the
--keystore- Specifies the path to a PKCS12 keystore file that holds the private key and certificate for HTTPS connections to the Agent.
- Users are free to specify any file name, typically the name
https-keystore.p12is used. The keystore file will be copied to the<config>/privatedirectory. - If a keystore file is made available then the Agent's
<config>/private/private.conffile has to hold a reference to the keystore location and optionally the keystore password. It is therefore recommended to use the--private-confoption to deploy an individualprivate.conffile that holds settings related to a keystore. - For automating the creation of keystores see JS7 - How to add SSL TLS Certificates to Keystore and Truststore.
--keystore-password- Specifies the password for access to the keystore. Use of a keystore password is required.
- Consider use of quotes when specifying the password.
--keystore-alias- If a keystore holds more than one private key, for example if separate pairs of private keys/certificates for server authentication and client authentication exist, then it is not determined which private key/certificate will be used. The alias name of a given private key/certificate is specified when the entry is added to the keystore. The alias name allows to indicate a specific private key/certificate to be used.
--client-keystore- Use of this setting is optional. It can be used if separate certificates for Server Authentication and Client Authentication are used.
- The Client Authentication private key and certificate can be added to a client keystore. The location and configuration of a client keystore correspond to the
--keystoreoption.
--client-keystore-password- Specifies the password for access to the client keystore. Use of a client keystore password is required if a client keystore is used.
- Consider explanations for the
--keystore-passwordoption.
--client-keystore-alias- If a client keystore holds more than one private key, for example if a number of private keys/certificates for client authentication exist, then it is not determined which private key/certificate will be used.
- Consider explanations for the
--keystore-aliasoption.
--truststore- Specifies the path to a PKCS12 truststore file that holds the certificate(s) for HTTPS connections to the Agent using mutual authentication .
- Users are free to specify any file name, typically the name
https-truststore.p12is used. The truststore file will be copied to the<config>/privatedirectory. - If a truststore file is made available then the Agent's
<config>/private/private.conffile has to hold a reference to the truststore location and optionally the truststore password. It is therefore recommended to use the--private-confoption to deploy an individualprivate.conffile that holds settings related to a truststore. - For automating the creation of truststores see JS7 - How to add SSL TLS Certificates to Keystore and Truststore.
--truststore-password- Specifies the password for access to the truststore. Use of a password is recommended as it is not primarily intended to protect access to the truststore. The password is intended to allow verification that truststore entries have been added using the same password.
- Consider use of quotes when specifying the password.
--java-home- Specifies the Java home directory that will be made available to the Agent from the
JAVA_HOMEenvironment variable specified with the Agent Instance Start Script typically available from the./bin/agent_<http-port>.shscript.
- Specifies the Java home directory that will be made available to the Agent from the
--java-options- Specifies the Java options that will be made available to the Agent from the
JAVA_OPTIONSenvironment variable specified with the Agent Instance Start Script typically available from the./bin/agent_<http-port>.shscript. - Java options can be used for example to specify Java heap space settings for the Agent.
- If more than one Java option is used then the value has to be quoted, for example
--java-options="-Xms256m -Xmx512m".
- Specifies the Java options that will be made available to the Agent from the
--service-dir- Specifies the systemd service directory to which the Agent's service file will be copied if the
--make-serviceswitch is used. - By default the
/usr/lib/systemd/systemdirectory will be used. Users can specify an alternative location.
- Specifies the systemd service directory to which the Agent's service file will be copied if the
--service-file- Specifies the path to a systemd service file that will be copied to the Agent's
<home>/bindirectory. Users are free to choose any file name for the service file. The resulting service file name will beagent_<http-port>.service. - The Agent Installation Script will not perform replacements in the service file to update paths etc., for details see
./bin/agent.service-example.
- Specifies the path to a systemd service file that will be copied to the Agent's
--service-name- Specifies the name of the systemd service that will be created if the
--make-serviceswitch is used. - By default the service name
js7_agent_<http-port>will be used.
- Specifies the name of the systemd service that will be created if the
Switches
-h | --help- Displays usage.
--force-sudo- Specifies that
sudois used when performing operations on directories. This switch is required if the home or data directory is not owned by the user account running the Agent Installation Script.
- Specifies that
--active- This setting is used for Director Agents only. It specifies that the Director Agent instance should act as the active node in a Director Agent Cluster during initial operation.
- This setting is not required for installation of a Primary Director Agent in an Agent Cluster. It can be used to revert a Secondary Director Agent to a Primary Director Agent.
--standby- This setting is used for Director Agents only. It specifies that the Director Agent instance should act as the standby node in a Director Agent Cluster during initial operation.
- This setting is required when installing a Secondary Director Agent instance in an Agent Cluster.
--no-yade- Excludes the YADE file transfer utility from the Agent installation.
- YADE is available from the
yadesub-directory of the Agent's<home>directory. If this switch is used then an existingyadesub-directory will be removed and YADE will not be copied from the installation tarball to the Agent's<home>directory.
--no-install- Specifies if the Installation Script should be used to update configuration items without changes to the binary files of the installation.
In fact no installation is performed but configuration changes as for example specified with the--keystoreoption will be applied.
- Specifies if the Installation Script should be used to update configuration items without changes to the binary files of the installation.
--use-installResuses an existing Agent installation. No installation files are specified as with the
--releaseor--tarballparameters. Instead, the new Agent's data directory and the respective service will be created.
--uninstall- Uninstalls the Agent including the steps to stop and to remove a running Agent service and to remove the
<home>and<data>directories.
- Uninstalls the Agent including the steps to stop and to remove a running Agent service and to remove the
--uninstall-home- Uninstalls the Agent including the steps to stop and to remove a running Agent service and removes the
<home>directory only.
- Uninstalls the Agent including the steps to stop and to remove a running Agent service and removes the
--uninstall-data- Uninstalls the Agent including the steps to stop and to remove a running Agent service and preserves the
<data>directory only.
- Uninstalls the Agent including the steps to stop and to remove a running Agent service and preserves the
--service-selinux- Updates the systemd service file for compliance with SELinux, see JS7 - How to install for SELinux.
--show-logs- Displays the log output created by the script if the
--log-diroption is used.
- Displays the log output created by the script if the
--make-dirs- If directories are missing that are indicated with the
--home,--backup-diror--log-diroptions then they will be created.
- If directories are missing that are indicated with the
--make-service- Specifies that a systemd service should be created for the Agent. The service will be created from the
--service-nameoption or its default value.
- Specifies that a systemd service should be created for the Agent. The service will be created from the
--move-libs- For an existing Agent installation the
libsub-directory includes .jar files that carry the release number in their file names. If replaced by a newer version thelibdirectory has to be moved or removed. This switch tries to move the directory to a previous version number as indicated from the.versionfile in the Agent's home directory, for example to renamelibtolib.2.3.1. - Files in the
lib/user_libsub-directory are preserved.
- For an existing Agent installation the
--remove-journal- If Agents have been installed for the wrong operating mode (standalone, clustered) then the Agent's journal in the
JS7_AGENT_DATA/statedirectory can be removed. This operation removes any orders submitted to an Agent and requires the Agent to be re-registered to a Controller.
- If Agents have been installed for the wrong operating mode (standalone, clustered) then the Agent's journal in the
--restart, --abort- Stops a running Agent before installation and starts the Agent after installation using the Agent's Instance Start Script. Running tasks will be forcibly terminated.
- This switch can be used with the
--waitand--cancelswitches to control the way how the Agent is terminated. This switch is ignored if the--exec-startor--exec-stopoptions are used. - Starting from release 2.7.2, the
--abortswitch is deprecated and is an alias used by previous releases.
--wait- Waits for running tasks including child processes if used with the
--restartswitch. - Starting from release 2.7.2, the
--waitswitch is available.
- Waits for running tasks including child processes if used with the
--cancel, --kill- Forcibly terminates a running Agent and running tasks if used with the
--restartswitch. This includes terminating child processes of running tasks. - Starting from release 2.7.2, the
--cancelswitch is available, the--killswitch is an alias used by previous releases.
- Forcibly terminates a running Agent and running tasks if used with the
Exit Codes
1: argument errors2: non-recoverable errors3: this exit code is returned when used with the--restartswitch and if it cannot be identified whether an Agent is running4: this exit code is returned if no--tarballoption is used and download of the tarball reports errors5: this exit code is returned when used with the--restartswitch and if the Agent cannot be started6: this exit code is returned when used with the--restartswitch and if the Agent cannot be stopped7: this exit code indicates that the Agent systemd service could not be started or stopped when using the--exec-start="StartService"or--exec-stop="StopService"options.
Replacements
The Agent Installation Script performs replacements of placeholders in installation files and configuration files by option values, for details see chapter Replacements.
Common Options
The following option groups are provided for frequent use cases. Options are qualified like this:
n/a: the setting is not applicable and must not be usednot used: the setting is ignoredoptional: the setting can be specifiedrequired: the setting must be specified
Common Options for use with HTTPS Connections
The following matrix shows applicable and required options for HTTPS connections to Agents:
| Option/Switch | Standalone Agent | Primary Director Agent | Secondary Director Agent | Subagent |
|---|---|---|---|---|
--http-port | required | required | required | required |
--https-port | required | required | required | required |
--keystore | required | required | required | required |
--keystore-password | required | required | required | required |
--keystore-alias | optional | optional | optional | optional |
--client-keystore | optional | optional | optional | optional |
--client-keystore-password | optional | optional | optional | optional |
--client-keystore-alias | optional | optional | optional | optional |
--truststore | required | required | required | required |
--truststore-password | required | required | required | required |
--controller-primary-cert | required | required | required | n/a |
--controller-primary-subject | required | required | required | n/a |
--controller-secondary-cert | required | required | required | n/a |
--controller-secondary-subject | required | required | required | n/a |
--director-primary-cert | n/a | not used | required | required |
--director-primary-subject | n/a | not used | required | required |
--director-secondary-cert | n/a | required | not used | required |
--director-secondary-subject | n/a | required | not used | required |
--private-conf | required | required | required | required |
Common Options for use with Agent Clusters
In an Agent Cluster users find the following roles:
- Primary Director Agent: first Director Agent that orchestrates Subagents. By default this is the active instance in a Director Agent Cluster.
- Secondary Director Agent: second Director Agent that orchestrates Subagents. By default this is the standby instance in a Director Agent Cluster.
- Subagent: a worker node in an Agent Cluster that executes jobs.
The following matrix shows applicable and required options for roles in an Agent Cluster as opposed to use of Standalone Agents:
| Option/Switch | Standalone Agent | Primary Director Agent | Secondary Director Agent | Subagent |
|---|---|---|---|---|
--active | n/a | required | n/a | n/a |
--standby | n/a | n/a | required | n/a |
--director-primary-cert | n/a | not used | required for HTTPS mutual authentication | required for HTTPS mutual authentication |
--director-primary-subject | n/a | not used | required for HTTPS mutual authentication | required for HTTPS mutual authentication |
--director-secondary-cert | n/a | required for HTTPS mutual authentication | not used | required for HTTPS mutual authentication |
--director-secondary-subject | n/a | not used | required for HTTPS mutual authentication | required for HTTPS mutual authentication |
--agent-cluster-id | n/a | required | required | required for HTTPS |
--private-conf | required | required | required | required for HTTPS |
--license-key | optional | required | required | optional |
--license-bin | optional | required | required | optional |
Common Options for use with systemd
The following matrix shows applicable and required options for use with systemd:
| Option/Switch | Standalone Agent | Primary Director Agent | Secondary Director Agent | Subagent |
|---|---|---|---|---|
--service-dir | optional | optional | optional | optional |
--service-file | optional | optional | optional | optional |
--service-name | optional | optional | optional | optional |
--service-selinux | optional | optional | optional | optional |
--make-service | required | required | required | required |
--exec-start | required | required | required | required |
--exec-stop | required | required | required | required |
Examples
The following examples illustrate typical use cases. Users should consider to specify current releases, see JS7 - Download.
Install or Update from Download
./js7_install_agent.sh \
--release=2.5.2 \
--home=/home/sos/agent \
--http-port=4445 \
--make-dirs
# downloads the release tarball from the SOS Web Site
# creates the home directory if it does not exist
# extracts the tarball to the Agent's home directory
# operates the Agent for HTTP port 4445
Install or Update from Tarball
curl 'https://download.sos-berlin.com/JobScheduler.2.5/js7_agent_unix.2.5.2.tar.gz' \
-o /tmp/js7_agent_unix.2.5.2.tar.gz
./js7_install_agent.sh \
--tarball=/tmp/js7_agent_unix.2.5.2.tar.gz \
--home=/home/sos/agent \
--http-port=4445 \
--make-dirs
# downloads the release tarball from the SOS Web Site using curl
# creates the home directory if it does not exist
# extracts the tarball to the Agent's home directory
# operates the Agent for HTTP port 4445
Install or Update using separate Home and Data Directories
./js7_install_agent.sh \
--release=2.5.2 \
--home=/opt/sos-berlin.com/js7/agent \
--data=/var/sos-berlin.com/js7/agent \
--http-port=4445 \
--make-dirs
# downloads the release tarball from the SOS Web Site
# makes use of separate home and data directories for configuration data, log data etc.
# creates the home and data directories if they do not exist
# extracts the tarball to the Agent's home directory
# populates the data directory from initial configuration files
# operates the Agent for HTTP port 4445
Install or Update owning Home and Data Directories to separate Accounts
./js7_install_agent.sh \
--release=2.5.2 \
--home=/opt/sos-berlin.com/js7/agent \
--data=/var/sos-berlin.com/js7/agent \
--user=sos2 \
--home-owner=sos1:sos1 \
--data-owner=sos2:sos2 \
--http-port=4445 \
--make-dirs
# downloads the release tarball from the SOS Web Site
# makes use of separate home and data directories for configuration data, log data etc.
# creates the home and data directories if they do not exist
# extracts the tarball to the Agent's home directory
# populates the data directory from initial configuration files
# owns the home and data directories to separate user accounts and groups
# specifies the 'sos2' run-time account with write access to the data directory
# requires to be executed by the root account or by an account with sudo permissions
# operates the Agent for HTTP port 4445
Install or Update parallel Agent
./js7_install_agent.sh \
--home=/opt/sos-berlin.com/js7/agent \
--data=/var/sos-berlin.com/js7/agent_44445 \
--http-port=44445 \
--make-dirs \
--use-install
# makes use of an existing Agent installation in the home directory
# creates the data directory if it does not exist
# populates the data directory from initial configuration files
# operates the Agent for HTTP port 44445
Install or Update and Stop/Start using systemd
curl 'https://download.sos-berlin.com/JobScheduler.2.5/js7_agent_unix.2.5.2.tar.gz' \
-o /tmp/js7_agent_unix.2.5.2.tar.gz
./js7_install_agent.sh \
--tarball=/tmp/js7_agent_unix.2.5.2.tar.gz \
--home=/home/sos/agent \
--http-port=4445 \
--exec-start=StartService \
--exec-stop=StopService \
--make-service \
--make-dirs
# downloads the release tarball from the SOS Web Site using curl
# extracts the tarball to the Agent's home directory
# creates the Agent's systemd service
# stops and starts the Agent's systemd service
# operates the Agent for HTTP port 4445
Install or Update and Stop/Start using Individual Commands
curl 'https://download.sos-berlin.com/JobScheduler.2.5/js7_agent_unix.2.5.2.tar.gz' \
-o /tmp/js7_agent_unix.2.5.2.tar.gz
./js7_install_agent.sh \
--tarball=/tmp/js7_agent_unix.2.5.2.tar.gz \
--home=/home/sos/agent \
--http-port=4445 \
--exec-start="/home/sos/agent/bin/agent_4445.sh start" \
--exec-stop="/home/sos/agent/bin/agent_4445.sh stop" \
--make-dirs
# downloads the release tarball from the SOS Web Site using curl
# extracts the tarball to the Agent's home directory
# stops and starts the Agent by individual commands
# operates the Agent for HTTP port 4445
Install or Update and Stop/Start using Instance Start Script
curl 'https://download.sos-berlin.com/JobScheduler.2.5/js7_agent_unix.2.5.2.tar.gz' \
-o /tmp/js7_agent_unix.2.5.2.tar.gz
./js7_install_agent.sh \
--tarball=/tmp/js7_agent_unix.2.5.2.tar.gz \
--home=/home/sos/agent \
--http-port=4445 \
--restart \
--make-dirs
# downloads the release tarball from the SOS Web Site using curl
# extracts the tarball to the Agent's home directory
# stops and starts the Agent from its instance start script <home>/bin/agent_4445.sh
# operates the Agent for HTTP port 4445
Install or Update using Java Home and Java Options
curl 'https://download.sos-berlin.com/JobScheduler.2.5/js7_agent_unix.2.5.2.tar.gz' \
-o /tmp/js7_agent_unix.2.5.2.tar.gz
./js7_install_agent.sh \
--tarball=/tmp/js7_agent_unix.2.5.2.tar.gz \
--home=/home/sos/agent \
--http-port=4445 \
--java-home=/opt/java/jdk-17.0.2 \
--java-options="-Xmx512m -Xms256m" \
--restart \
--make-dirs
# downloads the release tarball from the SOS Web Site using curl
# extracts the tarball to the Agent's home directory
# specifies the Java version and Java options to be used
# stops and starts the Agent from its instance start script <home>/bin/agent_4445.sh
# operates the Agent for HTTP port 4445
Install or Update with Return Values
curl 'https://download.sos-berlin.com/JobScheduler.2.5/js7_agent_unix.2.5.2.tar.gz' \
-o /tmp/js7_agent_unix.2.5.2.tar.gz
retval=/tmp/js7_install_agent.$$.tmp
./js7_install_agent.sh \
--tarball=/tmp/js7_agent_unix.2.5.2.tar.gz \
--home=/home/sos/agent \
--http-port=4445 \
--backup-dir=/tmp/backups \
--log-dir=/tmp/logs \
--return-values=$retval \
--exec-start=StartService \
--exec-stop=StopService \
--make-service \
--make-dirs
log_file=$(cat $retval | grep "log_file" | cut -d'=' -f2)
backup_file=$(cat $retval | grep "backup_file" | cut -d'=' -f2)
# downloads the release tarball from the SOS Web Site using curl
# creates a backup archive and log file
# extracts the tarball to the Agent's home directory
# stops and starts the Agent from its systemd service
# provides return values from a temporary file which includes the path to the log file and to the backup archive
# operates the Agent for HTTP port 4445
Install or Update with Fallback
curl 'https://download.sos-berlin.com/JobScheduler.2.5/js7_agent_unix.2.5.2.tar.gz' \
-o /tmp/js7_agent_unix.2.5.2.tar.gz
retval=/tmp/js7_install_agent.$$.tmp
./js7_install_agent.sh \
--tarball=/tmp/js7_agent_unix.2.5.2.tar.gz \
--home=/home/sos/agent \
--http-port=4445 \
--backup-dir=/tmp/backups \
--log-dir=/tmp/logs \
--return-values=$retval \
--restart \
--show-logs \
--make-dirs
|| ( backup=$(cat $retval | grep "backup_file" | cut -d'=' -f2 ) \
&& ( test -e "$backup" ) && \
./js7_install_agent.sh \
--tarball=$backup \
--home=/home/sos/agent \
--http-port=4445 \
--log-dir=/tmp/logs \
--restart \
--show-logs )
log_file=$(cat $retval | grep "log_file" | cut -d'=' -f2)
backup_file=$(cat $retval | grep "backup_file" | cut -d'=' -f2)
# downloads the release tarball from the SOS Web Site using curl
# creates a backup archive and log file
# extracts the tarball to the Agent's home directory
# reverts the installation from a backup archive in case of failure
# stops and starts the Agent from its instance start script <home>/bin/agent_4445.sh
# displays log output on termination of the script
Install or Update and Apply Certificates for HTTPS Connections
curl 'https://download.sos-berlin.com/JobScheduler.2.5/js7_agent_unix.2.5.2.tar.gz' \
-o /tmp/js7_agent_unix.2.5.2.tar.gz
./js7_install_agent.sh \
--tarball=/tmp/js7_agent_unix.2.5.2.tar.gz
--home=/home/sos/agent \
--controller-id=controller \
--http-port=localhost:4445 \
--https-port=batch.example.com:4445 \
--private-conf=/home/sos/agent-deployment/private.conf-template-agent \
--controller-primary-cert=/home/sos/agent-deployment/centostest-primary.crt \
--controller-secondary-cert=/home/sos/agent-deployment/centostest-secondary.crt \
--keystore=/home/sos/agent-deployment/https-keystore.p12 \
--keystore-password="jobscheduler" \
--truststore=/home/sos/agent-deployment/https-truststore.p12 \
--truststore-password="jobscheduler" \
--exec-start=StartService \
--exec-stop=StopService \
--make-service \
--make-dirs
# downloads the release tarball from the SOS Web Site using curl
# extracts the tarball to the Agent's home directory
# specifies the Controller ID of the Controller to which the Agent is dedicated
# specifies HTTP port 4445 on the localhost network interface and the same HTTPS port on the server network interface
# specifies the paths to the Primary and Secondary Controller's server certificates if a Controller Cluster is used
# for a Standalone Controller the --controller-secondary-cert option is omitted
# deploys the Agent private configuration file which holds references to keystore and truststore
# deploys keystore and truststore files
# stops and starts the Agent's systemd service
Note:
- For details about certificates and HTTPS connections see JS7 - Agent HTTPS Connections.
- The
private.confconfiguration file holds references to the Controller instances' certificates and the Director Agent instances' certificates in order to verify incoming connections using HTTPS mutual authentication. - Users have a choice how to provide the required configuration:
- Download the private.conf-template-agent template, the Agent Installation Script performs replacements of placeholders in the template file from option values, for details see chapter Replacements.
- Users can manually adjust configuration items in the
private.conffile that they specify for the Agent Installation Script, see JS7 - Agent Configuration Items.
Renew Certificates for HTTPS Connections
./js7_install_agent.sh \
--home=/home/sos/agent \
--controller-id=controller \
--http-port=localhost:4445 \
--https-port=batch.example.com:4445 \
--private-conf=/home/sos/agent-deployment/private.conf-template-agent \
--controller-primary-cert=/home/sos/agent-deployment/centostest-primary.crt \
--controller-secondary-cert=/home/sos/agent-deployment/centostest-secondary.crt \
--keystore=/home/sos/agent-deployment/https-keystore.p12 \
--keystore-password="jobscheduler" \
--truststore=/home/sos/agent-deployment/https-truststore.p12 \
--truststore-password="jobscheduler" \
--exec-start=StartService \
--exec-stop=StopService \
--no-install
# performs no installation but certificate renewal only
# specifies the Controller ID of the Controller to which the Agent is dedicated
# addresses an existing Agent operated for HTTP port 4445 on the localhost network interface and the same HTTPS port on the server network interface
# specifies the paths to the Primary and Secondary Controller's server certificates if a Controller Cluster is used
# for a Standalone Controller the --controller-secondary-cert option is omitted
# deploys the Agent private configuration file that holds references to keystore and truststore
# deploys keystore and truststore files
# stops and starts the Agent's systemd service
Install or Update Primary Director Agent and Apply Certificates for HTTPS Connections
curl 'https://download.sos-berlin.com/JobScheduler.2.6/js7_agent_unix.2.6.0.tar.gz' \
-o /tmp/js7_agent_unix.2.6.0.tar.gz
curl 'https://download.sos-berlin.com/JobScheduler.2.6/js7-license.jar' \
-o /tmp/js7-license.jar
./js7_install_agent.sh \
--tarball=/tmp/js7_agent_unix.2.6.0.tar.gz \
--home=/opt/sos-berlin.com/js7/agent \
--data=/var/sos-berlin.com/js7/agent_4445 \
--controller-id=controller \
--agent-cluster-id=agent-cluster \
--http-port=localhost:4445 \
--https-port=batch.example.com:4445 \
--license-key=/home/sos/agent-deployment/example.pem \
--license-bin=/tmp/js7-license.jar \
--private-conf=/home/sos/agent-deployment/private.conf-template-agent \
--controller-primary-cert=/home/sos/agent-deployment/centostest-primary.crt \
--controller-secondary-cert=/home/sos/agent-deployment/centostest-secondary.crt \
--director-primary-cert=/home/sos/agent-deployment/centostest-primary.crt \
--director-secondary-cert=/home/sos/agent-deployment/centostest-secondary.crt \
--keystore=/home/sos/agent-deployment/https-keystore.p12 \
--keystore-password="jobscheduler" \
--truststore=/home/sos/agent-deployment/https-truststore.p12 \
--truststore-password="jobscheduler" \
--active \
--make-dirs
# downloads the release tarball from the SOS Web Site using curl
# downloads the binary file for licensed code to enable cluster operations
# extracts the release tarball to the Agent's home directory
# specifies the Controller ID of the Controller to which the Agent is dedicated
# specifies the Agent Cluster ID
# specifies HTTP port 4445 on the localhost network interface and the same HTTPS port on the server network interface
# specifies the paths to the Primary and Secondary Controller's server certificates if a Controller Cluster is used
# for a Standalone Controller the --controller-secondary-cert option is omitted
# deploys the Agent private configuration file which holds references to keystore and truststore
# deploys keystore and truststore files
# makes the Agent the active Director Agent in an Agent Cluster
# stops and starts the Agent's systemd service
Note:
- For details about certificates and HTTPS connections see JS7 - Agent HTTPS Connections.
- The
private.confconfiguration file holds references to the Controller instances' certificates and the Director Agent instances' certificates in order to verify incoming connections using HTTPS mutual authentication. - Users have a choice how to provide the required configuration:
- Download the private.conf-template-agent template, the Agent Installation Script performs replacements of placeholders in the template file from option values, for details see chapter Replacements.
- Users can manually adjust configuration items in the
private.conffile that they specify for the Agent Installation Script, see JS7 - Agent Configuration Items.
Install or Update Secondary Director Agent and Apply Certificates for HTTPS Connections
curl 'https://download.sos-berlin.com/JobScheduler.2.6/js7_agent_unix.2.6.0.tar.gz' \
-o /tmp/js7_agent_unix.2.6.0.tar.gz
curl 'https://download.sos-berlin.com/JobScheduler.2.6/js7-license.jar' \
-o /tmp/js7-license.jar
./js7_install_agent.sh \
--tarball=/tmp/js7_agent_unix.2.6.0.tar.gz \
--home=/opt/sos-berlin.com/js7/agent \
--data=/var/sos-berlin.com/js7/agent_4445 \
--controller-id=controller \
--agent-cluster-id=agent-cluster \
--http-port=localhost:4445 \
--https-port=batch.example.com:4445 \
--license-key=/home/sos/agent-deployment/example.pem \
--license-bin=/tmp/js7-license.jar \
--private-conf=/home/sos/agent-deployment/private.conf-template-agent \
--controller-primary-cert=/home/sos/agent-deployment/centostest-primary.crt \
--controller-secondary-cert=/home/sos/agent-deployment/centostest-secondary.crt \
--director-primary-cert=/home/sos/agent-deployment/centostest-primary.crt \
--director-secondary-cert=/home/sos/agent-deployment/centostest-secondary.crt \
--keystore=/home/sos/agent-deployment/https-keystore.p12 \
--keystore-password="jobscheduler" \
--truststore=/home/sos/agent-deployment/https-truststore.p12 \
--truststore-password="jobscheduler" \
--standby \
--make-dirs
# parameterization is the same as from the previous example for a Primary Director Agent
# the one exception being use of the --standby switch for a Secondary Director Agent
Install or Update Subgent and Apply Certificates for HTTPS Connections
curl 'https://download.sos-berlin.com/JobScheduler.2.6/js7_agent_unix.2.6.0.tar.gz' \
-o /tmp/js7_agent_unix.2.6.0.tar.gz
./js7_install_agent.sh \
--tarball=/tmp/js7_agent_unix.2.6.0.tar.gz \
--home=/opt/sos-berlin.com/js7/agent \
--data=/var/sos-berlin.com/js7/agent_4445 \
--agent-cluster-id=agent-cluster \
--http-port=localhost:4445 \
--https-port=batch.example.com:4445 \
--private-conf=/home/sos/agent-deployment/private.conf-template-agent \
--director-primary-cert=/home/sos/agent-deployment/centostest-primary.crt \
--director-secondary-cert=/home/sos/agent-deployment/centostest-secondary.crt \
--keystore=/home/sos/agent-deployment/https-keystore.p12 \
--keystore-password="jobscheduler" \
--truststore=/home/sos/agent-deployment/https-truststore.p12 \
--truststore-password="jobscheduler" \
--make-dirs
# downloads the release tarball from the SOS Web Site using curl
# extracts the release tarball to the Agent's home directory
# specifies the Agent Cluster ID
# specifies HTTP port 4445 on the localhost network interface and the same HTTPS port on the server network interface
# specifies the paths to the Primary and Secondary Director Agents' server certificates
# deploys the Agent private configuration file which holds references to keystore and truststore
# deploys keystore and truststore files
# stops and starts the Agent's systemd service
Note:
- For details about certificates and HTTPS connections see JS7 - Agent HTTPS Connections.
- The
private.confconfiguration file holds references to the Director Agent instances' certificates in order to verify incoming connections using HTTPS mutual authentication. - Users have a choice how to provide the required configuration:
- Download the private.conf-template-agent template, the Agent Installation Script performs replacements of placeholders in the template file from option values, for details see chapter Replacements.
- Users can manually adjust configuration items in the
private.conffile that they specify for the Agent Installation Script, see JS7 - Agent Configuration Items.
Start Agent
./js7_install_agent.sh \
--home=/home/sos/agent \
--http-port=4445 \
--exec-start=StartService \
--exec-stop=StopService \
--no-install
# stops the Agent's systemd service if the Agent is running
# starts the Agent's systemd service
Stop Agent
./js7_install_agent.sh \
--home=/home/sos/agent \
--http-port=4445 \
--exec-stop=StopService \
--no-install
# stops the Agent's systemd service if the Agent is running
Patch from Download
./js7_install_agent.sh \
--release=2.2.3 \
--patch=JS-1984 \
--home=/home/sos/agent \
--http-port=4445 \
--exec-start=StartService \
--exec-stop=StopService
# downloads the patch tarball from the SOS Web Site
# extracts the patch tarball to the Agent's home directory
# stores the patch files to the Agent's <home>/lib/patches sub-directory
# stops and starts the Agent's systemd service
Patch from Tarball
curl 'https://download.sos-berlin.com/patches/2.2.3-patch/js7_agent.2.2.3-PATCH.JS-1984.tar.gz' \
-o /tmp/js7_agent.2.2.3-PATCH.JS-1984.tar.gz
./js7_install_agent.sh \
--tarball=/tmp/js7_agent.2.2.3-PATCH.JS-1984.tar.gz \
--patch=JS-1984 \
--home=/home/sos/agent \
--http-port=4445 \
--exec-start=StartService \
--exec-stop=StopService
# downloads the patch tarball from the SOS Web Site using curl
# extracts the patch tarball to the Agent's home directory
# stores patch files to the Agent's <home>/lib/patches sub-directory
# stops and starts the Agent's systemd service
Patch from .jar File
curl 'https://download.sos-berlin.com/patches/2.2.3-patch/js7_agent.2.2.3-PATCH.JS-1984.jar' \
-o /tmp/js7_agent.2.2.3-PATCH.JS-1984.jar
./js7_install_agent.sh \
--patch-jar=/tmp/js7_agent.2.2.3-PATCH.JS-1984.jar \
--patch=JS-1984 \
--home=/home/sos/agent \
--http-port=4445 \
--exec-start=StartService \
--exec-stop=StopService
# downloads the patch .jar file from the SOS Web Site using curl
# stores patch files to the Agent's <home>/lib/patches sub-directory
# stops and starts the Agent's systemd service
Uninstall
./js7_install_agent.sh \
--home=/home/sos/agent \
--http-port=4445 \
--exec-stop=StopService \
--uninstall
# stops the Agent's systemd service
# removes the Agent's systemd service
# removes the Agent's home and data directories
Uninstall and Preserve Home Directory
./js7_install_agent.sh \
--home=/opt/sos-berlin.com/js7/agent \
--data=/var/sos-berlin.com/js7/agent \
--http-port=4445 \
--exec-stop=StopService \
--uninstall-data
# stops the Agent's systemd service
# removes the Agent's systemd service
# removes the Agent's data directory
# preserves the Agent's home directory that might be used by parallel Agents
Uninstall and Preserve Data Directory
./js7_install_agent.sh \
--home=/opt/sos-berlin.com/js7/agent \
--data=/var/sos-berlin.com/js7/agent \
--http-port=4445 \
--exec-stop=StopService \
--uninstall-home
# stops the Agent's systemd service
# removes the Agent's systemd service
# removes the Agent's home directory
# preserves the Agent's data directory
Replacements
The Agent Installation Script performs replacements of placeholders in installation files and configuration files by option values.
Installation files
<home>/bin/agent_<http-port>.shReplacements are performed for the following placeholders used for environment variables by respective option values:
Placeholder Option Value JS7_AGENT_HOME--homeJS7_AGENT_DATA--dataJS7_AGENT_USER--userJS7_AGENT_HTTP_PORT--http-portJS7_AGENT_HTTPS_PORT--https-portJS7_AGENT_CONFIG_DIR--configJS7_AGENT_LOGS--logsJS7_AGENT_WORK_DIR--workJS7_AGENT_PID_FILE_DIR--pid-file-dirJS7_AGENT_PID_FILE_NAME--pid-file-nameJAVA_HOME--java-homeJAVA_OPTIONS--java-options
<home>/bin/agent_<http-port>.serviceReplacements are performed for the following placeholders by respective option values:
Placeholder Option Value <JS7_AGENT_HTTP_PORT>--http-portPIDFile=--pid-file-dirUser=--userExecStart=, ExecStop=, ExecReload=--home
Configuration files
<config>/private/private.confReplacements are performed for the following placeholders by respective option values:
Placeholder Option Value {{controller-id}}--controller-id{{controller-primary-distinguished-name}}--controller-primary-cert{{controller-secondary-distinguished-name}}--controller-secondary-cert{{agent-cluster-id}}--agent-cluster-id{{director-primary-distinguished-name}}--director-primary-cert{{director-secondary-distinguished-name}}--director-secondary-cert{{keystore-file}}--keystore{{keystore-password}}--keystore-password{{keystore-alias}}--keystore-alias{{client-keystore-file}}--client-keystore{{client-keystore-password}}--client-keystore-password{{client-keystore-alias}}--client-keystore-alias{{truststore-file}}--truststore{{truststore-password}}--truststore-passwordFind a template for a
private.conffile using placeholders for HTTPS mutual authentication:
Download the private.conf-template-agent template,
Automation from a Job
The Agent Installation Script can be executed from a job for automated update and upgrade of JS7 Agents.
Add Workflow from Example
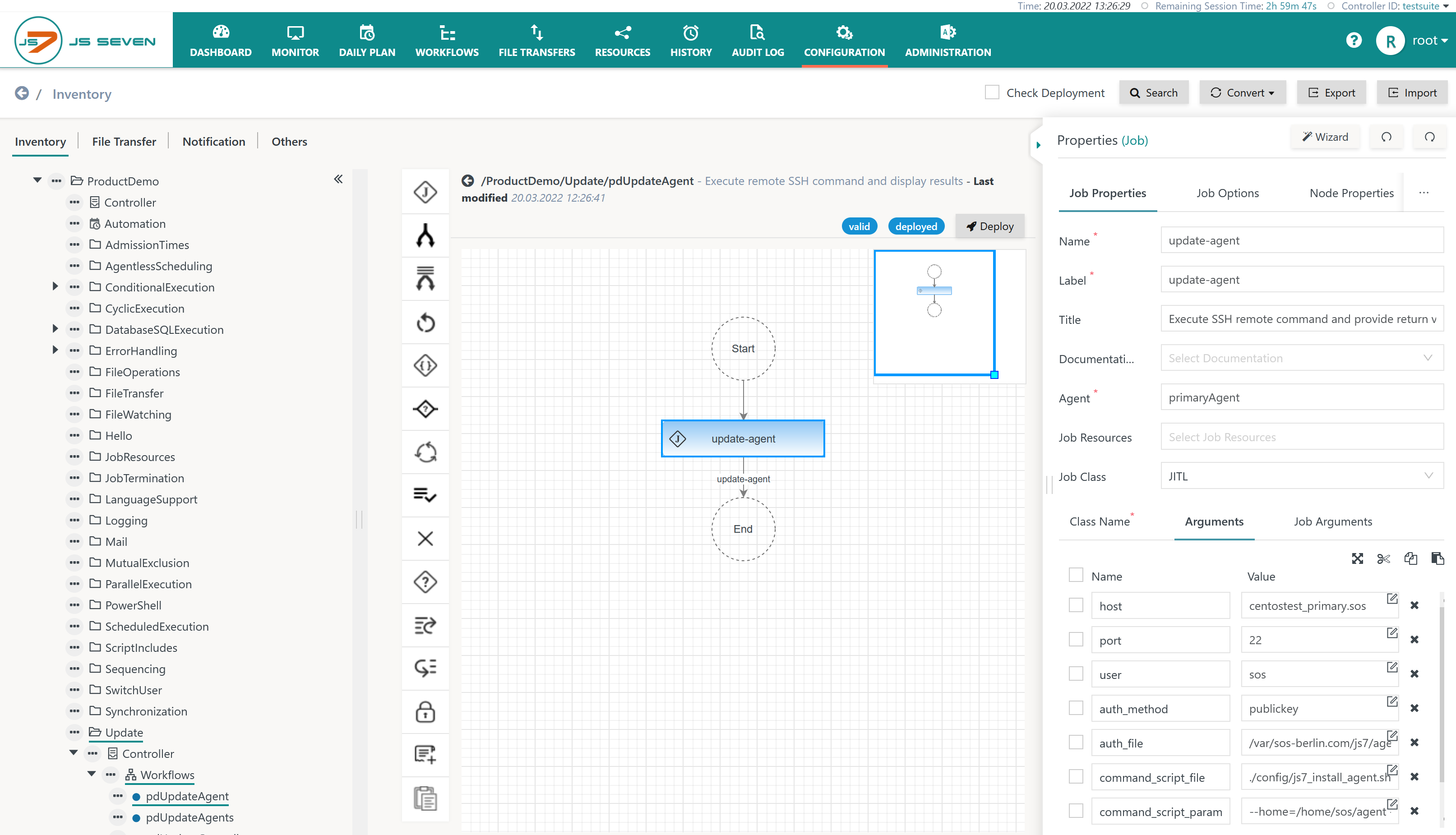
Download Workflow (upload .json): pdUpdateAgent.workflow.json
When uploading the example the workflow should look like this:
Explanation:
- The above sample can be uploaded to create the workflow including the job
- Alternatively a new workflow can be created and the Wizard, which can be started using a button in the upper right hand corner of the screenshot, can be used.
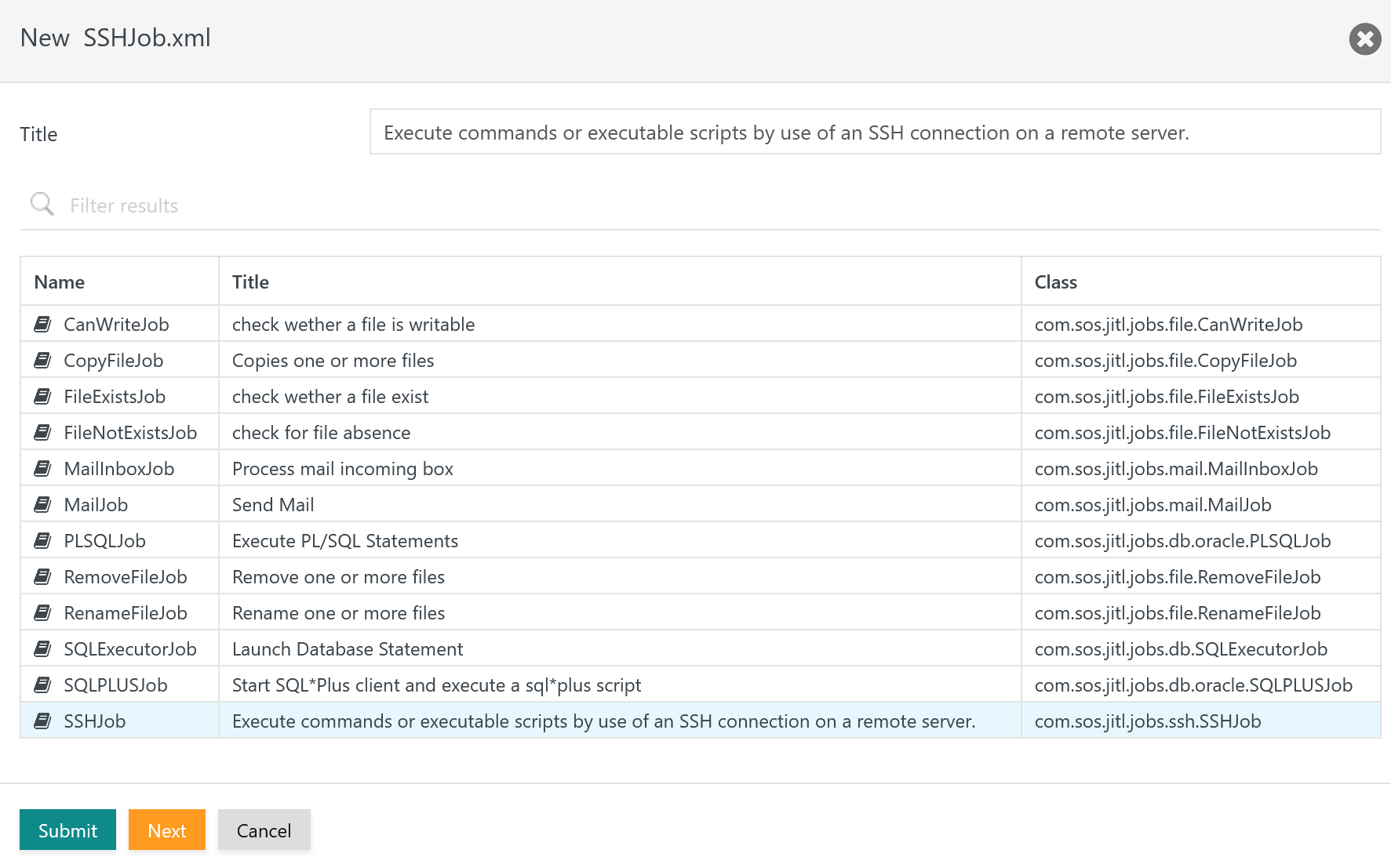
Add SSHJob from Wizard
Invoking the Wizard brings forward the following popup window:
When selecting the SSHJob and using the Next button the following popup window is displayed that provides a list of available arguments:
Explanation:
- The job basically makes use of the following arguments:
- Connection
- host: specifies the host name or IP address of the remote host.
- port: specifies the SSH port on the remote host, defaults to 22.
- Authentication
- user: specifies the user account used to login with the remote host.
- auth_method: is one of
passwordorpublickey. - auth_file: specifies the path to identify the file that holds the private key for use with the
publickeyauthentication method. A relative path is specified, see the descriptions below.
- Command Execution
- command_script_file: specifies the path to the Agent Installation Script that should be executed on the remote host.
- The indicated path
./config/js7_install_agent.shstarts from the Agents working directory that holds theconfigsub-directory. The working directory by defaults uses the namevar_<port>, for examplevar_4445, for the HTTP port for which the Agent is operated. This directory can be specified during JS7 - Agent Installation On Premises and JS7 - Agent Installation for Containers. - The SSHJob transfers the Agent Installation Script to the remote host.
- The indicated path
- command_script_param: specifies the arguments used when invoking the Agent Installation Script.
- A typical parameterization can look like this:
--home=/home/sos/agent --tarball=/mnt/releases/js7/js7_agent_unix.2.3.1.tar.gz --log-dir=/tmp/logs --show-logs --make-dirs
- A typical parameterization can look like this:
- command_script_file: specifies the path to the Agent Installation Script that should be executed on the remote host.
- Connection
- More information about parameterization of the job can be found in the JS7 - JITL SSHJob article.
Automation for Mass-rollout
Users who operate larger numbers of Agents can extend the above solution to use a single workflow to perform mass-rollout of Agents.
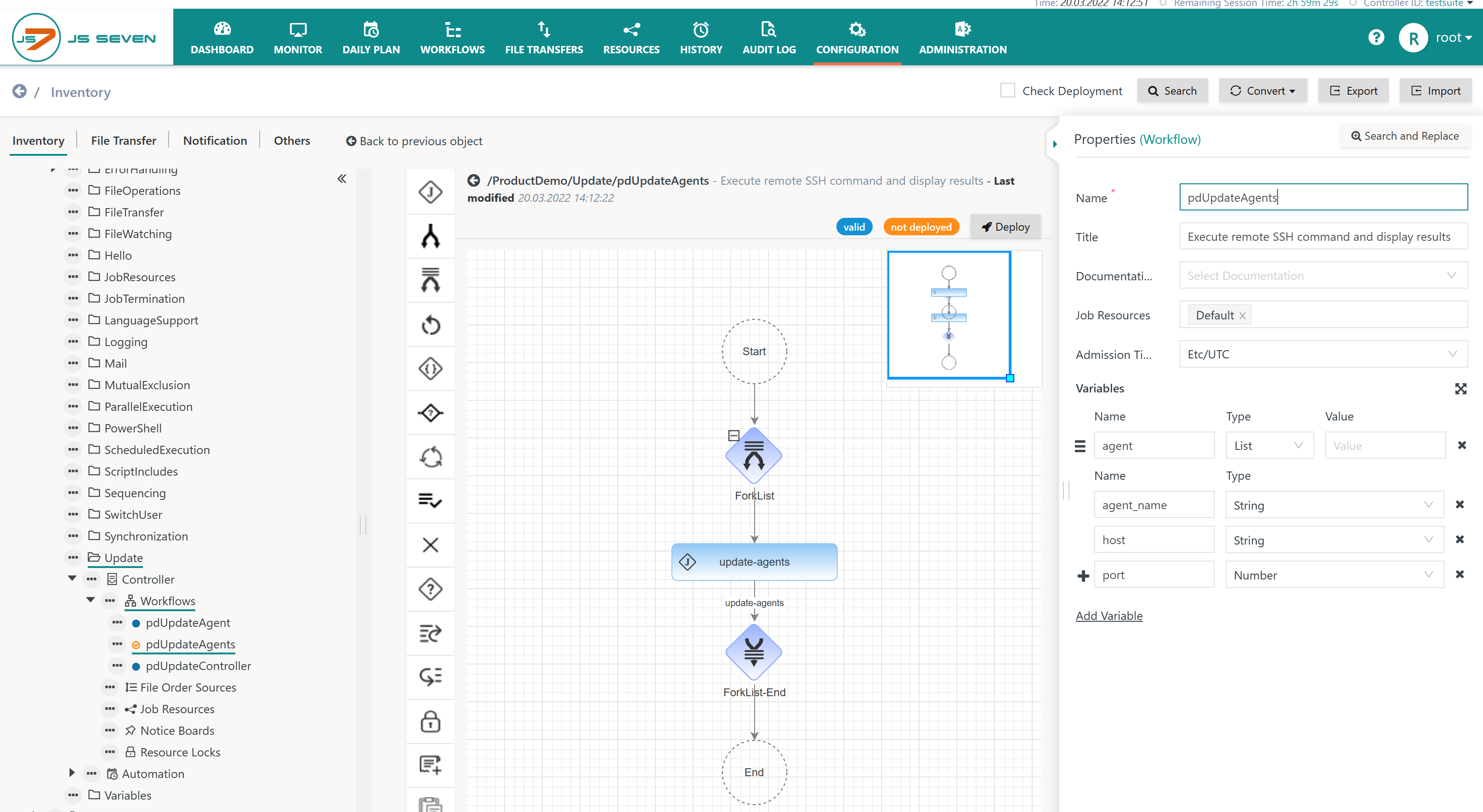
Add Workflow from Example
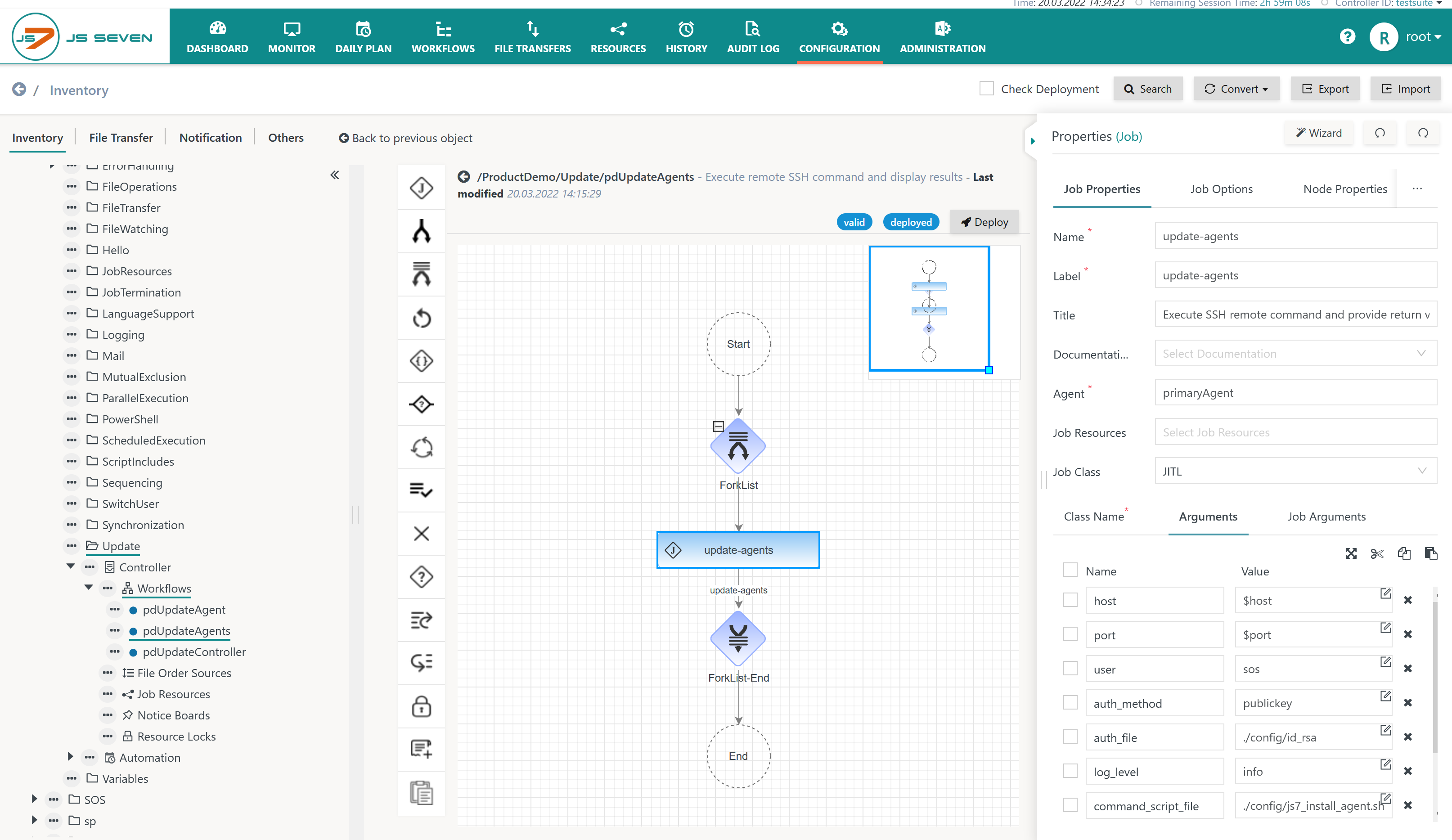
Download Workflow (upload .json): pdUpdateAgents.workflow.json
When uploading the example the workflow should look like this:
Explanation:
- The example makes use of the JS7 - ForkList-Join Instruction that allows specification of a single branch with any number of jobs and additional instructions. Orders can carry variable sets that are used to parameterize the ForkList Instruction. For each variable set the ForkList Instruction dynamically creates a new branch at run-time. This allows parallelism for updates and upgrades of Agents.
- The workflow declares the variable set from the example above as follows:
- Name of List Variable: the name
agentis used and the datatypelistis selected to indicate a Variable Set. - Name of Variable: Additional variables are added such as
agent_name,host,portthat will be populated when adding an order to the workflow.- Later on the variables are assigned the SSHJob to connect to the relevant host and port.
- One of the variables declared must hold a unique value, for example the
agent_name, that allows identification of a Variable Set.
- Name of List Variable: the name
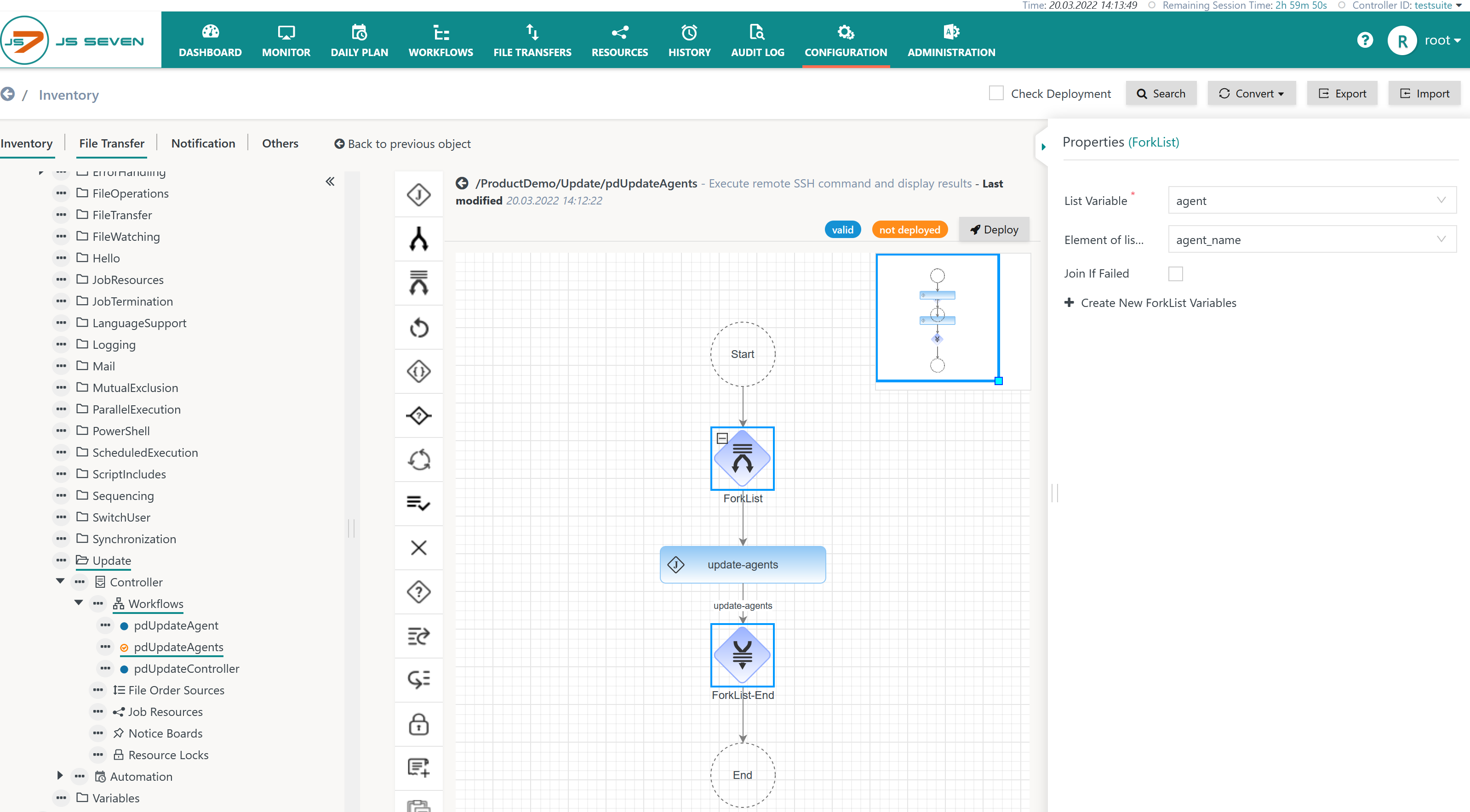
When clicking the ForkList Instruction then the instruction's properties are displayed as shown in this screenshot:
Explanation:
- The ForkList Instruction is assigned the List Variable that is declared with the workflow.
- One of the elements of the List Variable is selected and is used to create a unique branch for each Variable Set carried by the order.
Add SSHJob
Basically the same explanations apply for the SSHJob as stated in the Add SSHJob from Wizard section above.
The difference lies in the use of different hosts and ports when connecting to remote machines to update or to upgrade Agents:
Explanation:
- The following job arguments use variables instead of constant values:
- host: specifies the host name or IP address of the remote host. The argument is assigned the
$hostvariable from the Variable Set. - port: specifies the SSH port on the remote host, defaults to 22. The argument is assigned the
$portvariable from the Variable Set.
- host: specifies the host name or IP address of the remote host. The argument is assigned the
- The assumptions in this example include:
- the same user account and private key can be used for connections to any hosts on which Agents are to be updated or upgraded,
- the same parameterization can be used - for example, the same location of the Agent's home directory - for the Agent Installation Script on any host.
- Users to whom these assumptions do not apply should consider adding relevant variables for the auth_file and command_script_param arguments to their Variable Set.
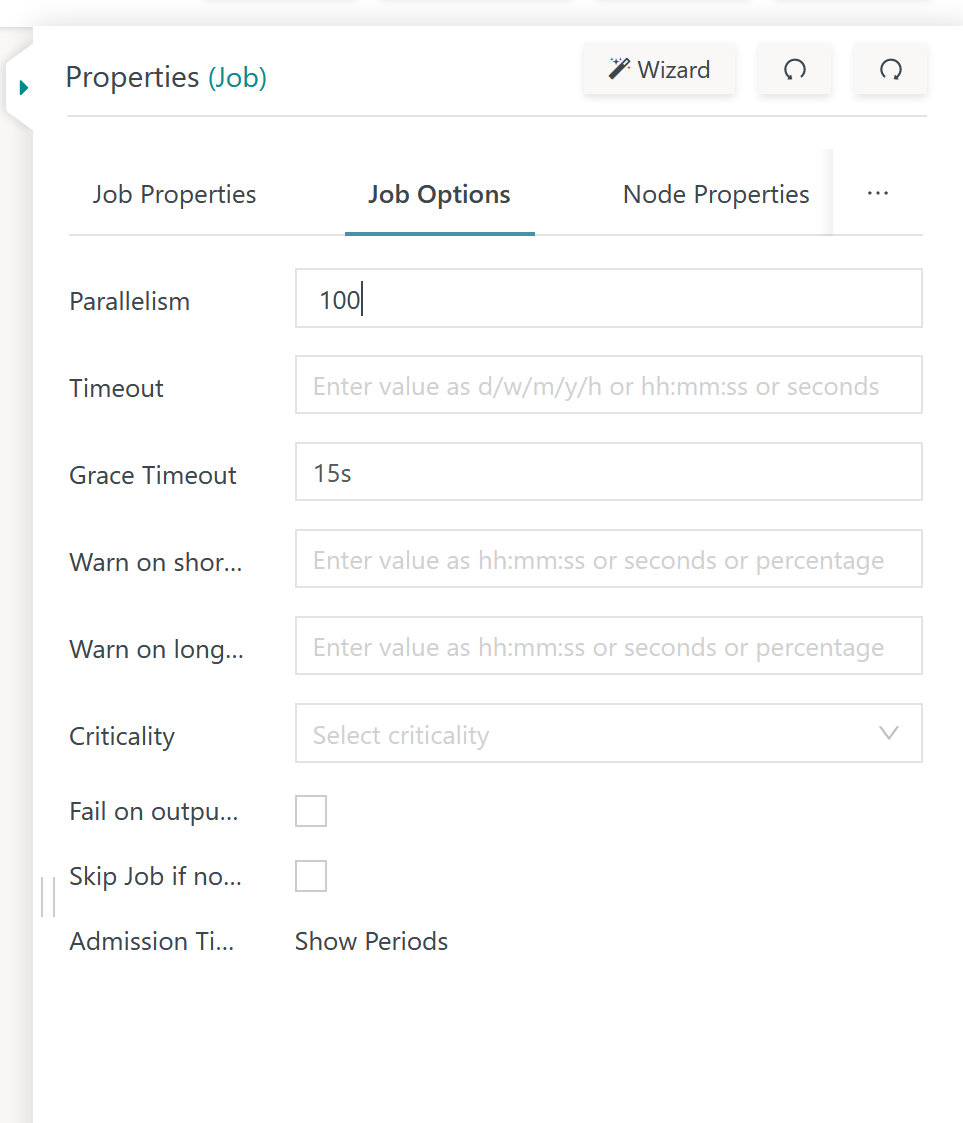
The Job Options tab of the job property window should be used to allow parallelism of job execution:
- Users should specify the maximum number of parallel executions. Running updates for 100 and more Agents at the same time is a typical use case.
- Resource consumption of the SSHJob preferably is about main memory as the job runs within an Agent's Java Virtual Machine.
- It is safe to assume a maximum of 24 MB main memory consumption per instance of the SSHJob.
- Should more memory be required then heap space settings have to be increased when starting the Agent, see JS7 - How To - Apply Java Options for more information.
Add Schedule
A Schedule is created for automated execution of the workflow.
- The Schedule specifies:
- the Workflow from the example above to which an order should be added,
- any number of Variable Sets that carry variables for the hosts on which Agents are to be updated and upgraded,
- the point in time when the order should be started.
- For details see the JS7 - Schedules article.
Explanation:
- The Schedule allows the addition of any number of Variable Sets to a single order.
- The Variable Set is declared from the Workflow and is considered by the Schedule.
- Note that both checkboxes should not be selected:
- Plan Order automatically,
- Submit Order to Controller when planned.
- Users often do not want to update or upgrade Agents at regular intervals according to a calendar. Instead, this Schedule is intended to be used for manually adding an order to update or upgrade Agents at a given date.
- A number of Schedules can be used to manage groups of Agents that are to be updated or upgraded at a common point in time.
When operating a larger number of JS7 Agents then it is an option to automate the management of Schedules.
- The JS7 - REST Web Service API allows creation and population of Schedules.
- This can also be achieved using the JS7 - PowerShell Module which allows generation and management of schedules with a few lines of script code.
Add Order from Schedule to Daily Plan
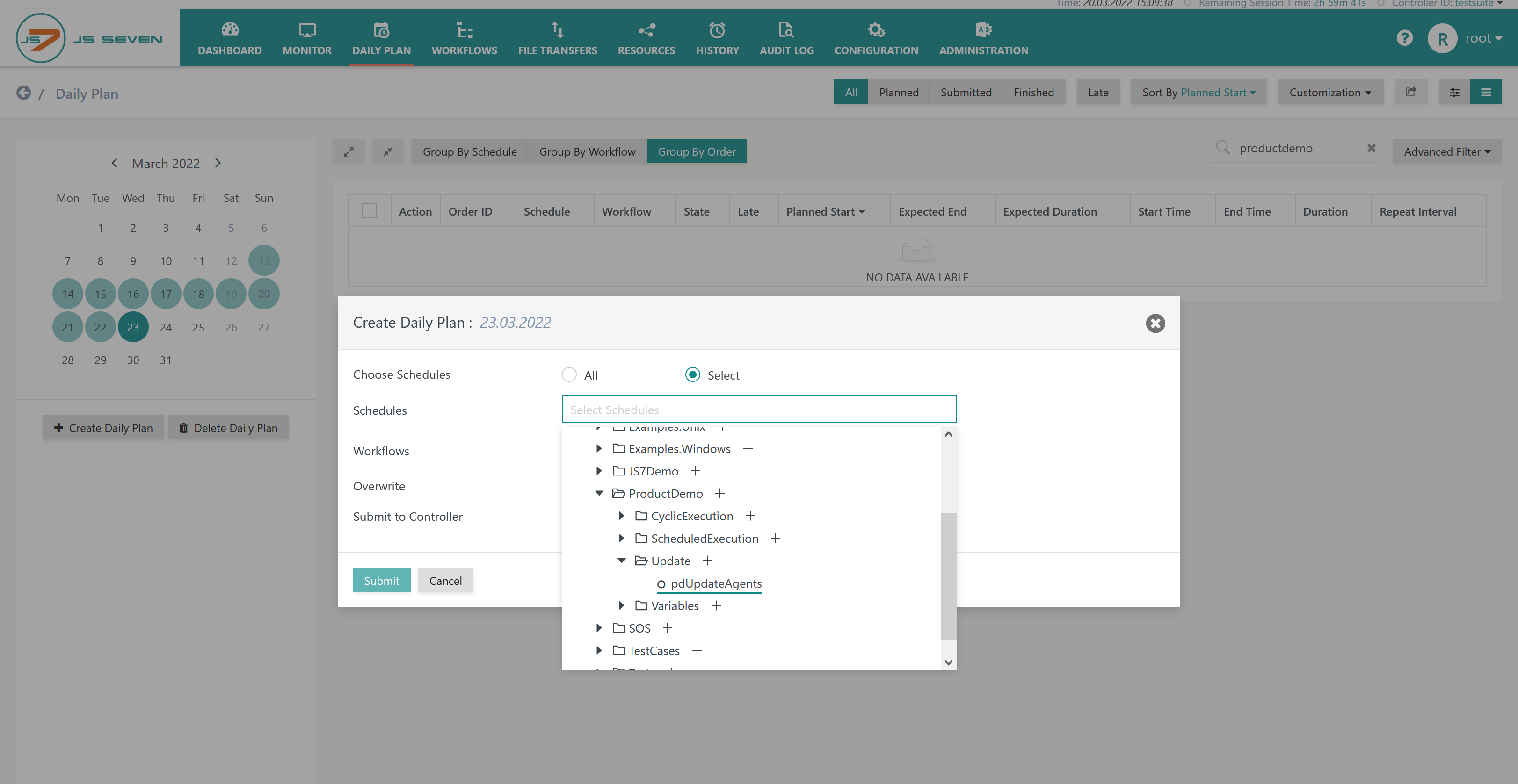
Starting from the fact that the previously introduced Schedule is not automatically applied by the JS7 - Daily Plan Service this Schedule is used to manually create Daily Plan entries.
- In the JS7 - Daily Plan view the button Create Daily Plan can be used to add orders from a Schedule for the date selected with the calendar.
- In the popup window that is brought forward when clicking the Create Daily Plan button users should select the Schedule as shown here:
From the previously introduced Schedule a single order is created that carries a number of Variable Sets for hosts on which to update or upgrade Agents.
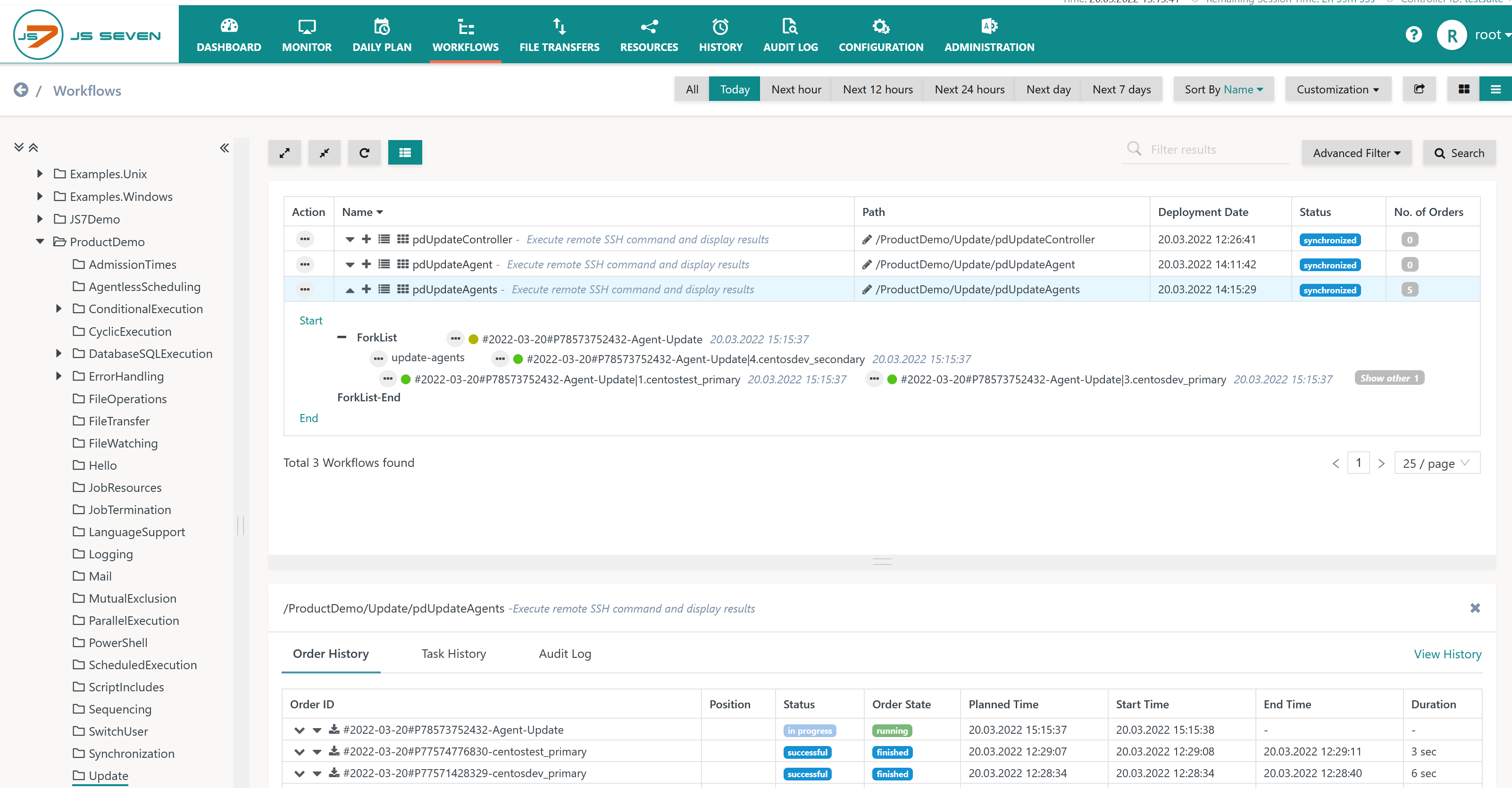
Control Order Execution
The Workflows view allows monitoring and control of orders for updating or upgrading Agents:
- From the screenshot a single parent order is visible in yellow-greenish color.
- A child order is created for each Variable Set of the parent order. Child orders run in parallel in individual branches that are dynamically created by the ForkList Instruction.
Further Resources
- JS7 - Automated Installation and Update
- JS7 - How to create X.509 SSL TLS Certificates
- JS7 - How to add SSL TLS Certificates to Keystore and Truststore
- JS7 - ForkList-Join Instruction