Introduction
This is the sixth in a series of articles describing how to get started with using the the YADE Client via its Command Line Interface.
YADE Tutorials List
YADE Client Command Line Interface
- Getting Started and Downloading files
- Simple File Selection
- More Advanced File Selection
- Checking files for completeness
- Public / Private Key Authentication
- Transfer via a Jump Host / DMZ
YADE Background Service
Prerequisites
See the Using the tutorials with the YADE Client Command Line Interface article for guidelines to setting up and running these tutorial examples.
Instructions for installing, configuring and using the XML Editor can be found in the XML Editor series of articles.
Download the configuration file
The configuration described in this tutorial can be downloaded and then directly opened in the XML Editor using the following link:
Public / Private Key Authentication with SFTP
In addition to the password authentication described for FTP and SFTP in the first tutorial in this series YADE can use Public/Private Key Authentication.
In this tutorial we assume here that users are familiar with the concepts of public/private key authentication. Users wishing more information can find a detailed description of the principles behind this form of authentication in the Wikipedia, Public-key Cryptography article.
Public/private key configuration
Private Key
- Download the private key demo_id_rsa for the demo user.
The corresponding demo_id_rsa.pub public key has already been installed on our file transfer test system. - Save the private key in the jade_demo folder alongside the sos-berlin_demo_2_local_pub_priv_key.xml file.
ProtocolFragment
The example presented in this tutorial uses a ProtocolFragment based on the sftp_demo_sos-berlin_pass fragment described in the first tutorial in this series and which used password authentication.
To use public/private key authentication instead of password authentication:
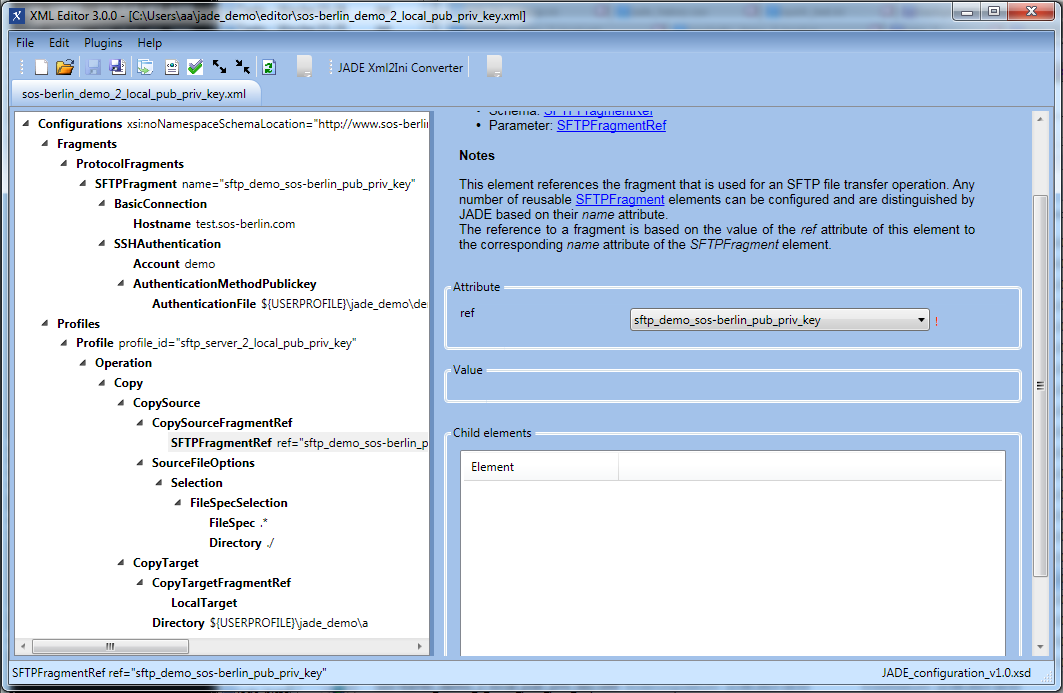
- the AuthenticationMethodPassword element is replaced with an AuthenticationMethodPublickey element and
- an AuthenticationFile element as shown in the XML Editor screenshot below.
Ensure that the path entered for this element is iidentical to the path used for the demo user's demo_id_rsa private key.- Users of a Windows-Unix compatibility software such as Cygwin may prefer to use alternative locations:
- For Windows users:
- %USERPROFILE%\.ssh\demo_id_rsa
where %USERPROFILE% is the path to your Windows user home directory.
- %USERPROFILE%\.ssh\demo_id_rsa
- For Unix users:
- ${HOME}\.ssh\demo_id_rsa
where ${HOME} is the path to your user's home directory.
- ${HOME}\.ssh\demo_id_rsa
- For Windows users:
- Users of a Windows-Unix compatibility software such as Cygwin may prefer to use alternative locations:
Note that the private key itself can be protected by a passphrase that can be specified with a Passphrase child of the AuthenticationMethodPublicKey element.
Profile
Apart from a changed profile_id and SFTPFragmentRef ref attributes, the Profile in this tutorial is identical to that used in the password authentication example described in the first tutorial in this series.
XML Editor Configuration
The Profile Code
The following code boxes can be opened to show the Profile and ProtocolFragments used in this example in XML and in settings.ini formats.
Running the Profile
This profile is called on Windows systems using one of the following commands, depending on the YADE version being used:
jade.cmd -settings="%USERPROFILE%\jade_demo\sos-berlin_demo_2_local_pub_priv_key.ini" -profile="sftp_server_2_local_pub_priv_key"
jade.cmd -settings="%USERPROFILE%\jade_demo\sos-berlin_demo_2_local_pub_priv_key.xml" -profile="sftp_server_2_local_pub_priv_key"
On Unix systems the profile is called using one of the following commands, depending on the YADE version being used:
./jade.sh -settings="${HOME}/jade_demo/sos-berlin_demo_2_local_pub_priv_key.ini" -profile="sftp_server_2_local_pub_priv_key"
./jade.sh -settings="${HOME}/jade_demo/sos-berlin_demo_2_local_pub_priv_key.xml" -profile="sftp_server_2_local_pub_priv_key"
Behavior
Running the profile will cause six files to be downloaded after authentication has succeeded.
The connection will be ended after the download has been completed.