Scope
- The JobScheduler components are easy to install out-of-the-box. However, some more configuration items have to be considered to operate JobScheduler in a secure environment.
- Secure operation is applied at the following levels
- Connection Management
- Network Connections
- Database Connections
- Access Management
- Authentication
- Authorization
- Credentials Management
- Database Credentials
- Job Credentials
- Connection Management
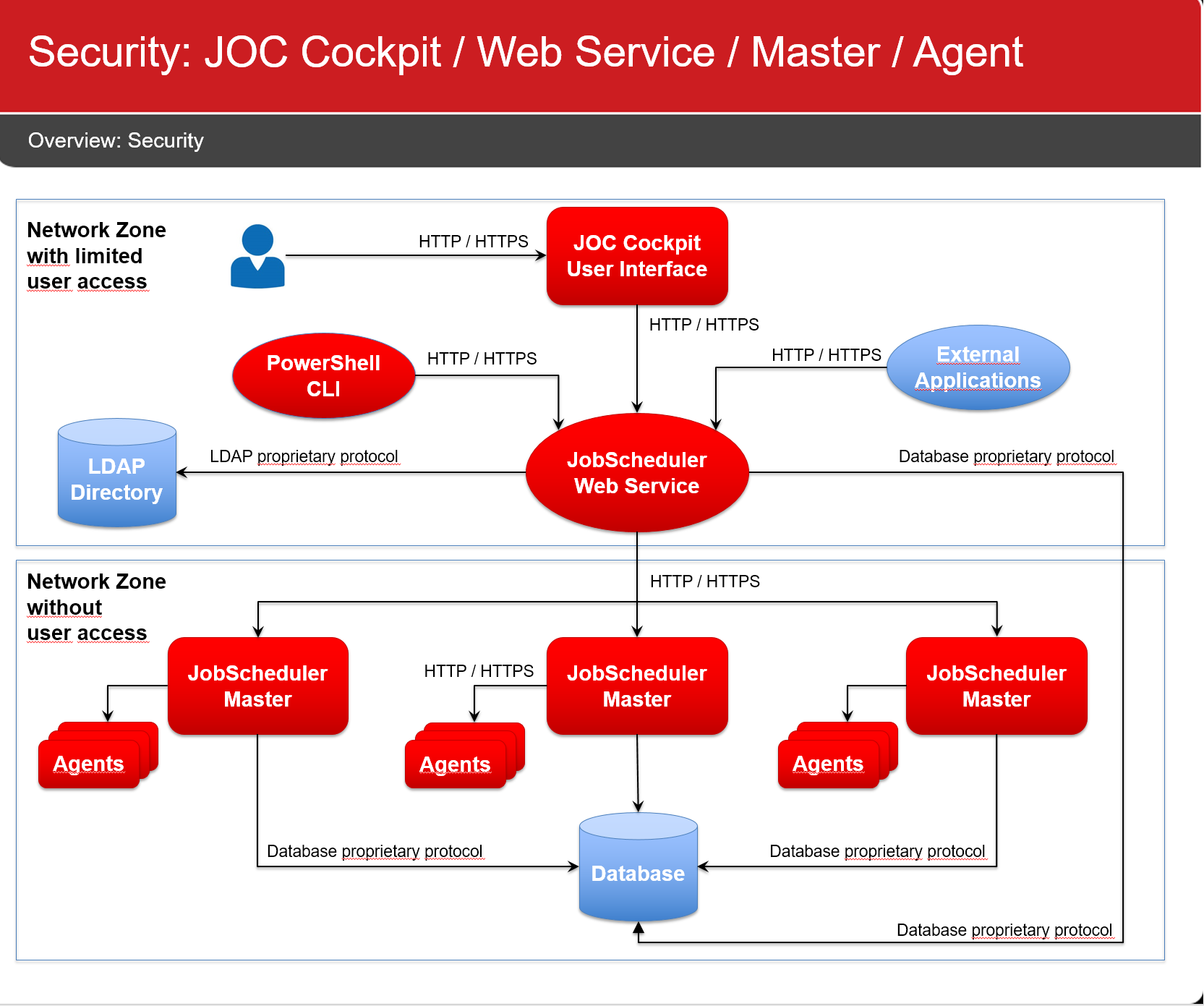
Connection Management
JobScheduler components make use of the following connections:
Network Connections
Default Configuration
The following default configuration is applied by the installer if users would not modify settings during installation:
- All network connections make use of HTTP
- Connections from a user browser to the JOC Cockpit
- Connections from the PowerShell CLI to the JOC Cockpit REST Web Service
- Connections from the JOC Cockpit REST Web Service to the JobScheduler Master
- Connections from the JobScheduler Master to Agents
- Port Usage
- The JOC Cockpit can be accessed at port 4446
- The JOC Cockpit REST Web Service can be accessed at port 4446
- The JobScheduler Master makes use of the following ports
- Access to the JobScheduler Master Web Service at port 40444
- Access to the JobScheduler Master via TCP at port 4444
- Access to the JobScheduler Master via UDP at port 4444
- The JobScheduler Agent listens to port 4445
- Network Interface Usage
- By default JobScheduler components will listen to the above mentioned ports on all available network interfaces.
Secure Configuration
The following recommendations should be applied to secure network connections.
- Configure network connections to use HTTPS
- Use of HTTPS includes that users provide valid certificates for the hosts that JobScheduler components are operated for. Use of self-signed certificates is a no-go.
- As HTTPS is restricted to secure the connection, in addition authentication is added to the configuration, e.g. when using HTTPS then a JobScheduler Master is configured to authenticate with an Agent in order to guarantee that the Master is what it claims to be and is entitled to access an Agent.
- For detailed instructions on the configuration see
- JOC Cockpit - HTTPS Authentication explains HTTPS for the JOC Cockpit and connection to the JobScheduler Master.
- JobScheduler Universal Agent - HTTPS Agent and Master Authentication
- Close the JobScheduler Master UDP and TCP port
- This port is not required for standard operation with releases starting from 1.11.
- This port is required for previous releases that include the "classic" JOC GUI running in the JobScheduler Master.
- Access to this port can be restricted with the
<allowed_host>setting in ./config/scheduler.xml
- Access to this port can be restricted with the
- This port is required for any releases if a JobScheduler Supervisor is used.
- Restrict use of network interfaces
- Consider to restrict the JobScheduler components to listen to specific network interfaces only.
- The JobScheduler Master can be configured by use of TBD
- The JobScheduler Agent can be configured by use of TBD
Database Connections
ss
- x
Access Management
Authentication
Authorization
Credentials Management
Database Credentials
Job Credentials
x