The JOC Cockpit has been designed from the beginning to ensure that it is suitable for use in security-sensitive areas.
Architecture
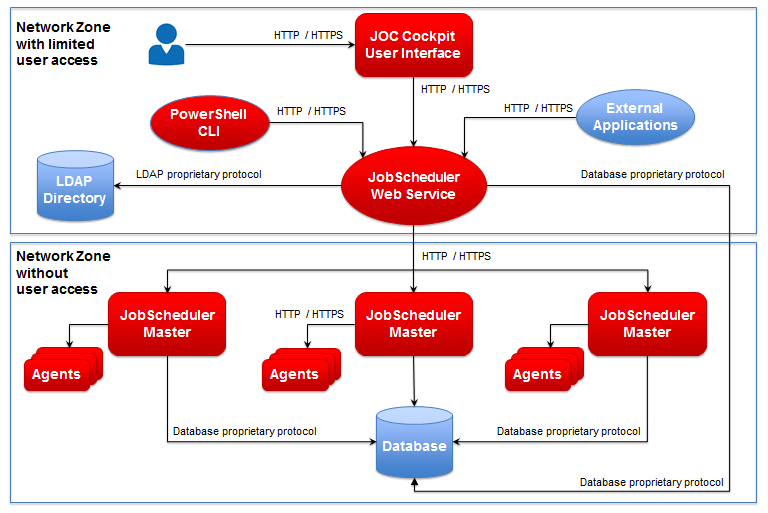
The architecture introduced with the JOC Cockpit ensures that users are restricted to only being able to directly access to the JOC Cockpit as illustrated in the diagram below. The JOC Cockpit then calls the Web Service which has access to the JobScheduler Masters themselves.
See the JOC Cockpit - Architecture article for more information.
Log In Form
The Remember Me setting in the JOC Cockpit Log In form shown below allows users to prevent misuse of log in information cached by the browser.
The behavior of the JOC Cockpit when Remember Me is set or not set depends on the situation. This behavior is specified in the following table:
| Situation | Remember Me Set | Remember Me Not set |
|---|---|---|
| User logs out, browser reverts to Log In page | Log In information shown, credentials are available | Log In form is empty, input of credentials required |
| Session expires, browser reverts to Log In page | Log In information shown | Log In form is empty, input of credentials required |
| Browser is closed during session and then reopened; Log In page is opened by user | User is automatically logged in | Log In form is empty, input of credentials required |
Note that:
- the Log In form will not be emptied after a period of time when Remember Me is set and a user does not log in again,
- the behavior specified in the table is independent of whether or not the browser is set to save login information.
- therefore do not use Remember Me if you are working in a security-sensitive environment.
Authorization Tokens
Separate authorization tokens are used for each communication step between the JOC Cockpit, the Web Service and the JobScheduler Masters and Agents. This means that if an attacker is able to take over and use a token they will only be able to bypass a part of the communication chain. This means that it will be harder for the attacker to remain undetected. CORRECT? RELEVANT?
Authorization Token for the JOC Cockpit
When a user logs on the JOC Cockpit generates an authorization token and saves it twice (Keys $SOS$accessTokenId and $SOS$permission), either in the browser's local storage, if Remember Me is set on logging in or in the browser's session storage, if Remember Me is not set.
ADD MATRIX TABLE
| Situation | Remember Me Set | Remember Me Not set |
|---|---|---|
| User logs out, browser reverts to Log In page | Access token remains in browser's local storage | Access token is deleted with the session storage |
| Session expires, browser reverts to Log In page | Access token is deleted | Access token is deleted with the session storage |
| Browser tab is closed during session and then reopened by opening recent tab (Firefox) | Access token remains in browser's local storage | Access token remains in browser's session storage |
Note that:
HTTP / HTTPS Communication
As indicated in the schematic architecture diagram above, communication between the JOC Cockpit, the Web Service and the JobScheduler Masters can be carried out using both HTTP and HTTPS protocols. By default after installation HTTP will be used. However, HTTPS should be implemented by system administrators for all communication steps when the JobScheduler is to be used in sensitive environments. Information about the configuration of the Jetty Web Server delivered with the JOC Cockpit for HTTPS can be found on the Jetty Web Site.