| Table of Contents | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
|
Introduction
- The "Password Safe" ( Credential Store , (CS) allows connection and other sensitive data to be encrypted and stored securely and independently of the application(s) such as . YADE and the JobScheduler YADE JITL Jobs that use this data. Access to the CS is only possible with access methods such as an SSH a key file and/or password.
- The CS requires the use of a
.kdbxdatabase and the installation of a kdbx-compatible user interface such as "KeePass 2" or "KeePass-X". - The advantage of using a CS is that the CS stores the credentials (and other information/parameters) sensitive information such as credentials in a standardized, secure and fully encrypted database and sensitive authentication information is not exposed in use. Applications access the CS database via a standard interface. The CS database can only be accessed by using password, encryption-key file (ppk) or a combination of both. The CS password is used to encrypt the contents stored in the CS database with AES.
- The CS can be used to securely store information or of parameters, database connection URL, run-time decryption key URLs, private key files and other access sensitive data.
Scope
This article describes the use of the Credential Store with the YADE Client via the client's command line interface.
A description of the use of the Credential Store with the YADE JITL job can be found in the Jobs JADEJob & JADE4DMZJob article.
...
KeePass 2 is used in the current article to install implement the credential store database.
...
For the examples described in the current article the following database was configured (on a Windows system):
- Path & name:
%USERPROFILE%\jade_demo\keepass\demo_cred_store.kdbx - Master Password:
sos
...
Adding Data to the Credential Store
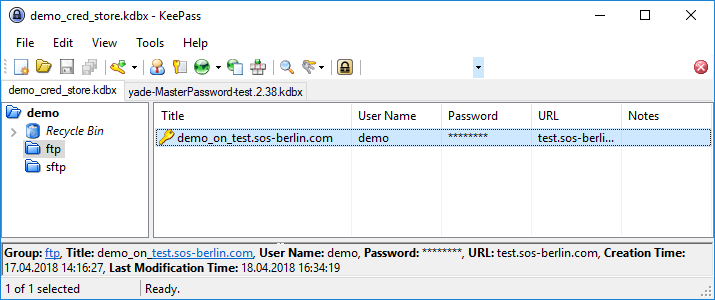
A group named ftp has been is used for the current example along with the entry "demo in on test.sos-berlin.com".
The following information can be retrieved from CS standard fields:
- Title: Target server name or IP address
- User name: The user identification of a user who is authorized authenticated for the operation.
- Password: Assigned password for the user.
- Server-name : Target server name or IP address
- Notes : Additional parameters/options such as YADE parameters, database connection URL, etc. can be stored in this section of the CS. The extra options are defined in a similarly way as used on the command line.
- a user account or passphrase for a private key.
- File File- Attachment: Files such as PGP or SSH private key files can be stored in the CS as attachments. Applications YADE will retrieve the contents of the attached file at run-time and will delete the file immediately after the operation has been completed- no intermediate or temporary files are created when reading attachments.
Configuration of an individual entry in the CS:
...
- A Credential Store Fragments element at the same level in the XML hierarchy as the Protocol Fragments elements.
- A Credential Store Fragment element that is referenced from the Protocol Fragment. This Fragment specifies the location and authentication for the Credential Store.
- Password, keyfile key file and combined password-keyfile /key file authentication methods are possible.
- The values of the connection and authentication elements are modified to refer to elements stored within the Credential Store.
...
The use of the Credential Store is contained within the settings file and is not exposed when calling the YADE clientClient. For example, on Windows systems, the YADE client Client could be called for the current example using:
...
...
london