...
- The "Password Safe" (Credential Store, CS) allows connection and other data to be encrypted and stored securely and independently of the application(s) such as.YADE and the JobScheduler YADE JITL Jobs that use this data. Access to the CS is only possible with access methods such as an SSH key or password.
- Currently The CS is using can use "KeePass 1.x" and "KeePassX" with the db version 1.0, thus CS can be used on most popular OS platforms.KeePass 2.x" but note that:
- KeePass 2.x can be used on more operating systems than Keepass 1.x see the Keepass Web Site for more information.
- KeePass 2.x allows more security features that are relevant for its use as a credential store than Keepass 1.x. Again, see the Keepass Web Site for more information.
- The advantage of using a CS is that the The advantage of using CS is that CS stores the credentials (and other information/parameters) into in a standardized, secure and fully encrypted database , i.e. Keepass. YADE will and sensitive authentication information is not exposed in use. Applications access the CS database using via a standard interface. The CS database can only be accessed using password, encryption-key file (ppk) or a combination of both. The CS password is used to encrypt the contents stored in the CS database with AES.
- The CS can be used to securely store information or parameters, database connection URL, run-time decryption key and other access data.
The following information can be retrieved from CS standard fields:
- UserID : The user identification of a user who is authorized for the operation.
- Password : Assigned password for the user.
- Server-Name : Target server name or IP address
- Notes : In the notes section of the CS other parameters/options can be stored, i.e. YADE parameters, database connection URL etc. The extra options are defined in a similarly way as used on the command line.
- File-Attachment : Files such as PGP or SSH private key files can be stored in the CS as attachments. Applications will retrieve the attached file at run-time and will delete the file immediately once operation is completed.
Scope
This article describes the use of the Credential Store with the YADE Client via the client's command line interface.
A description of the use of the Credential Store with the YADE JITL job can be found in the Jobs JADEJob & JADE4DMZJob article.
Configuration Procedure
The examples presented in this article are based on the simple file transfer example described in the The YADE Client Command Line Interface - Tutorial 1 - Getting Started article. This tutorial describes the configuration required to download a number of files from a online server provided by the SOS GmbH and save these file on the user's local file system. Using this server means that users can get a working example up and running with a minimum of effort. A simplified version of the configuration used in the tutorial (only specifying FTP) is available as a download: sos-berlin_demo_2_local.xml. Instructions for installing and configuring the YADE Client can be found in the YADE - Tutorials article.
The configuration provided in the download file will cause six files in the root server folder to be copied to a local /jade_demo/transfer_receive folder, generating the target folder in the user's home or profile directory if required and permissions are available. The files will be transferred by FTP and authentication for the server (user name and password) is specified in the download file.
Installing and configuring the Credential Store
The installation of KeePass II is described on the Keepass Web Site.
For the examples described in the current article the following database was configured (on a Windows system):
- Path & name:
%USERPROFILE%\jade_demo\keepass\demo_cred_store.kdbx - Master Password:
sos
Scope
This article describes the use of the Credential Store with the YADE Client via the client's command line interface.
A description of the use of the Credential Store with the YADE JITL job can be found in the Jobs JADEJob & JADE4DMZJob article.
Configuration Procedure
The examples presented in this article are based on the simple file transfer example described in the The YADE Client Command Line Interface - Tutorial 1 - Getting Started article. This tutorial describes the configuration required to download a number of files from a online server provided by the SOS GmbH and save these file on the user's local file system. Using this server means that users can get a working example up and running with a minimum of effort. A simplified version of the configuration used in the tutorial (only specifying FTP) is available as a download: sos-berlin_demo_2_local.xml. Instructions for installing and configuring the YADE Client can be found in the YADE - Tutorials article.
The configuration provided in the download file will cause six files in the root server folder to be copied to a local /jade_demo/transfer_receive folder, generating the target folder in the user's home or profile directory if required and permissions are available. The files will be transferred by FTP and authentication for the server (user name and password) is specified in the download file.
Installing and configuring the Credential Store
The installation of KeePass is described on the Keepass Web Site.
For the examples described in the current article the following database was configured (on a Windows system):
- Path & name:
%USERPROFILE%\jade_demo\keepass\demo_cred_store.kdbx - Master Password:
sos
The following information can be retrieved from CS standard fields:
- User name : The user identification of a user who is authorized for the operation.
- Password : Assigned password for the user.
- Server-Name : Target server name or IP address
- Notes : Additional parameters/options such as YADE parameters, database connection URL, etc. can be stored in this section of the CS. The extra options are defined in a similarly way as used on the command line.
- File-Attachment : Files such as PGP or SSH private key files can be stored in the CS as attachments. Applications will retrieve the attached file at run-time and will delete the file immediately after the operation has been completed.
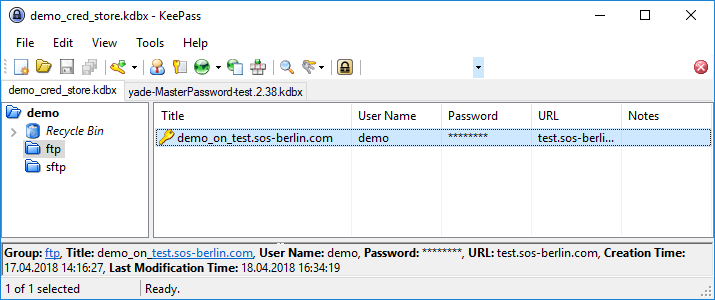
Configuration of an individual entry in the CS:
The following information was specified for the example The following information was specified in the database:
- Database:
demo_database - Group:
demo - Title:
demo on test.sos-berlin.com - UserIdUser name:
demo - Password:
demo - URL:
test.sos-berlin.com(alternativelyAlternatively, the IP address could have been specified here.)
Integrating the Credential Store in a File Transfer Configuration
...