...
- An LDAP Browser:
- The screenshots used in this article are made for the "Softerra LDAP Browser" that is configured to use the relevant LDAP Directory Service.
- A command line utility:
- The example commands used are executed with ldapSearch
How to set up an LDAP
...
Configuration
Carry out the following steps:
...
sAMAccountName@domain- The
sAMAccountNameattribute is a unique identifier for an accountAccount.
- The
domain\sAMAccountNamecn- The Common Name attribute value of the account Account is used.
- This format requires the Common Name of an account Account to be unique.
Note that LDAP account Account names may contain blank spaces. See the Authorization section below for a description of how blank spaces are handled when LDAP authentication is used with Shiro authorization.
...
- If Roles are to be assigned in the
shiro.inifile using the JOC Account Management: The LDAP Groups the Account is a member of have no effect. Proceed with Assigning roles in the shiro.ini File - If Roles are to be assigned with the group roles mapping: The LDAP Groups the account is a member of are assigned to JOC Cockpit roles. Proceed with Assigning Roles from LDAP Groups
- If a mix of 1. and 2. is to be used: Proceed with Assigning roles in the shiro.ini File and then with Assigning Roles from LDAP Groups
| Anchor | ||||
|---|---|---|---|---|
|
...
Roles in the shiro.ini File
After assigning Roles in the shiro.ini file the [users] section of the file will look like this:
...
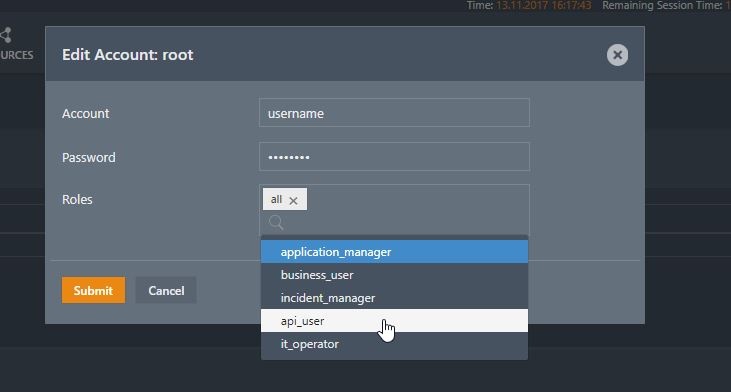
Role assignment in the shiro.ini file is configured in the Manage Accounts view of the JOC Cockpit. Do not enter the Password for a User Account that is to be authenticated by an LDAP Directory Service.
The roles Roles assigned to an entry are saved in the [users] section of the shiro.ini configuration file according to the following syntax:
...
it_operator,administrator
The JOC Cockpit Account Manager Management will add entries to the [users] section for the Role assignment.
- Account names may include blank spaces if they are stored in an LDAP Directory Service. Account names stored in the
shiro.iniconfiguration file may not contain blank spaces.- When a User account Account with blank spaces in its name is configured using the JOC Cockpit's Manage Accounts view then every blank space in the name will be automatically replaced with
%20before the name is written to theshiro.inifile. - When a User account Account with blank spaces in its name is added directly to the
shiro.inifile then every blank space in the name should replaced with %20 before the name is written to theshiro.inifile. - Every occurrence of
%20in an User Account User Name name saved in theshiro.inifile will be automatically converted to a blank space before this name is submitted to the LDAP server.
- When a User account Account with blank spaces in its name is configured using the JOC Cockpit's Manage Accounts view then every blank space in the name will be automatically replaced with
- Passwords may not be specified for Accounts with LDAP authentication when configuring such Accounts using the JOC Cockpit's Manage Accounts view .
- When a domain login is used then the reference has to contain the domain/account pattern e.g.
domain\accountoraccount@domain.
...
There are two options to find the Group membership(s) for a User Account:
- The account Account has a memberOf attribute. Then you can retrieve the list of groups with the User Search. Then proceed with Using memberOf with User Search.
- The account Account does not have a memberOf attribute. The group contains the accounts Accounts that are members of the group, Then proceed with Using group searchGroup Search.
These options cannot be mixed.
| Anchor | ||||
|---|---|---|---|---|
|
If the account Account entries do not have the memberOf attribute then you can skip this section and proceed with Using group searchGroup Search.
Settings:
ldapRealm.searchBaseldapRealm.userSearchFilter
...
| Anchor | ||||
|---|---|---|---|---|
|
b) Using
...
Group Search
If the account Account entries have the memberOf attribute then you can skip this section and proceed with Using memberOf with User Search. Settings:
ldapRealm.groupSearchBaseldapRealm.groupNameAttributeldapRealm.groupSearchFilter
After defining the group search Group Search the shiro.ini configuration file will look like this:
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
[main]
ldapRealm = com.sos.auth.shiro.SOSLdapAuthorizingRealm
ldapRealm.contextFactory.url = ldap://centos6_9_ldap.sos:389
ldapRealm.userDnTemplate = uid={0},ou=People,dc=sos
ldapRealm.groupSearchBase = ou=Groups,dc=sos
ldapRealm.groupNameAttribute = cn
ldapRealm.groupSearchFilter = (uniqueMember=uid=%s,ou=People,dc=sos)
# Mapping of a LDAP group to roles. You can assign more than one role with separator sign |
ldapRealm.groupRolesMap = \
sos : it_operator, \
apl : administrator|application_manager
rolePermissionResolver = com.sos.auth.shiro.SOSPermissionResolverAdapter
rolePermissionResolver.ini = $iniRealm
ldapRealm.rolePermissionResolver = $rolePermissionResolver
securityManager.realms = $ldapRealm
|
When the memberOf attribute is not available for the Account then you can use the group searchGroup Search.
Define the groupSearchBase and the groupSearchFilter. For example:
...
If the value of the member of the groups contain the account Account name from the login then you can skip this chapter
Sometimes the values of the member do not contain the account name Account Name from the login but, for example, the cn of the accountAccount. In that this case you have to search for the account Account first and then specify the name of the attribute that should be used instead of the acount Acount name from the login .
To achieve this, specify a searchBase, a userSearchFilter and a userNameAttribute.
...
ldapsearch -h localhost -p 389 -b "ou=People,dc=sos" -s sub "uid=fTester" -x
This search should return the account Account with the given account Account name. Identify the attribute that should be used for substitution in the group search Group Search base if it is not the account Account name from the login.
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
# extended LDIF # # LDAPv3 # base <ou=People,dc=sos> with scope subtree # filter: uid=fTester # requesting: ALL # # fTester, People, sos dn: uid=fTester,ou=People,dc=sos mail: info@sos-berlin.com uid: fTester givenName: Fritz objectClass: top objectClass: person objectClass: organizationalPerson objectClass: inetorgperson sn: Tester cn: Fritz Tester # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1 |
...