...
ldapsearch -h ldap.forumsys.com -p 389 -b "uid=gauss,dc=example,dc=com" -W -D "uid=gauss,dc=example,dc=com"
...
How to set up the configuration
...
| Anchor | ||||
|---|---|---|---|---|
|
2. Authentication
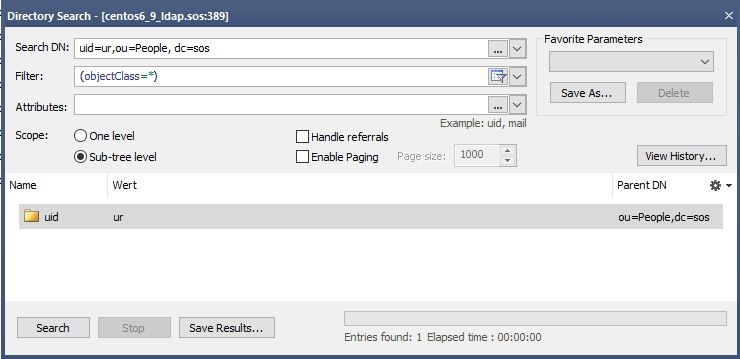
With the authentication you will check for a valid username/password combination. To achieve this, you have to specify the userDnTemplate. The value for the userDnTemplate can be read from the properties page of an user.
...
| Code Block | ||
|---|---|---|
| ||
[main]
ldapRealm = com.sos.auth.shiro.SOSLdapAuthorizingRealm
ldapRealm.userDnTemplate = uid={0},ou=People, dc=sos
ldapRealm.contextFactory.url = ldap://centos6_9_ldap.sos:389
rolePermissionResolver = com.sos.auth.shiro.SOSPermissionResolverAdapter
rolePermissionResolver.ini = $iniRealm
ldapRealm.rolePermissionResolver = $rolePermissionResolver
securityManager.realms = $ldapRealm
cacheManager = org.apache.shiro.cache.MemoryConstrainedCacheManager
securityManager.cacheManager = $cacheManager
securityManager.sessionManager.globalSessionTimeout = 900000
|
Examples for the userDnTemplate:
- Example
ldapRealm.userDnTemplate = uid={0},ou=People, dc=sos
- Configuration with public LDAP Server
...
adLdapRealm.userDnTemplate = sAMAccountName={0},dc=company,dc=com
Verification with ldapSearch
You can check you userDnTemplate with this ldapSearchCommand.
...
| Code Block | ||||
|---|---|---|---|---|
| ||||
# extended LDIF # # LDAPv3 # base <uid=gauss,dc=example,dc=com> with scope subtree # filter: (objectclass=*) # requesting: ALL # # gauss, example.com dn: uid=gauss,dc=example,dc=com objectClass: inetOrgPerson objectClass: organizationalPerson objectClass: person objectClass: top cn: Carl Friedrich Gauss sn: Gauss uid: gauss mail: gauss@ldap.forumsys.com # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1 |
Verification with Softerra LDAP Browser
Search with Search-Dn=userDnTemplate. You should find exactly one entry.
Verification with JOC
Try to login with a username from LDAP and a password. Use a username for which you have verified is correct by executing the ldapSearch described above. When you see this screen, the authentication works.
...
| Anchor | ||||
|---|---|---|---|---|
|
3. Authorization
Authorization means the assignment of roles to users. A role have permissions that are listed in the shiro.ini configuration file. A user have all permissions coming from the assigned roles.
There are two options how to assigns roles to users. Both options can be mixed. The result of the mix is the union of all assigned roles.
Assigning roles in the shiro.ini File
The roles assignment in the shiro.ini file is managed with the JOC Account Manager.
...
| Code Block | ||||
|---|---|---|---|---|
| ||||
[users]
gauss = ,all
newton = ,it_operator,administrator
[main]
ldapRealm = com.sos.auth.shiro.SOSLdapAuthorizingRealm
ldapRealm.userDnTemplate = uid={0},ou=People, dc=sos
ldapRealm.contextFactory.url = ldap://centos6_9_ldap.sos:389
rolePermissionResolver = com.sos.auth.shiro.SOSPermissionResolverAdapter
rolePermissionResolver.ini = $iniRealm
ldapRealm.rolePermissionResolver = $rolePermissionResolver
securityManager.realms = $ldapRealm
cacheManager = org.apache.shiro.cache.MemoryConstrainedCacheManager
securityManager.cacheManager = $cacheManager
securityManager.sessionManager.globalSessionTimeout = 900000
|
Assigning roles from LDAP Groups
| Anchor | ||||
|---|---|---|---|---|
|
The group roles mapping
When assigning the roles from the LDAP Groups the user is a member of the groups the groups will be mapped to the roles that are defined in the shiro.ini configuration file. This will be done with the groupRolesMap
...
Please not that the value of the group depends on the result of the search. It is the value of the attribute you have specified in the groupNameAttribute.
Example
ldapRealm.groupRolesMap = \sos : it_operator, \apl : administrator|application_manager
Example with the Public LDAP Server
ldapRealm.groupRolesMap = \ scientists : it_operator, \ mathematicians : all
Getting the groups a user is a member of
There are two options how to find the membership of the user.
a) Using memberOf with User Search
This approach looks for the user entry and then reads the "memberOf" attribute.
...
Define an userSearchFilter and a searchBase that will find the user (%s will be replaced by the username from the login without the domain)
Example for user group search
ldapRealm.searchBase = ou=People,dc=sos
ldapRealm.userSearchFilter = (uid=%s)
Example for AD
ldapRealm.searchBase = dc=example,dc=com ldapRealm.userSearchFilter = (sAMAcountName=%s)
...
| Anchor | ||||
|---|---|---|---|---|
|
b) Using group search
When the memberOf attribute is not available for the user, you can use the group search.
...
| Anchor | ||||
|---|---|---|---|---|
|
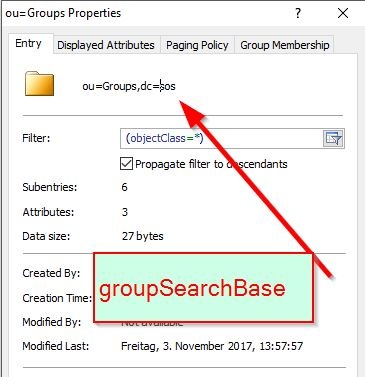
Getting the value for the groupSearchBase
Identify the place where the groups are stored. This is your groupSearchBase.
Getting the value for the groupSearchFilter
Click one groupEntry and see how the members are stored there.
...