...
When the memberOf attribute is not available for the user, you can use the group search.
Define the groubSearchBase groupSearchBase and the groupSearchFilter
ldapRealm.groupSearchBase = ou=Groups,dc=sos
...
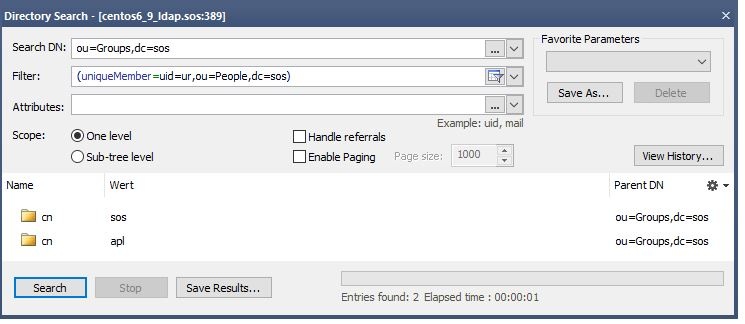
To get the correct values for these key a LDAP client like the "Softerra LDAP Browser" is helpful.
| Anchor | ||||
|---|---|---|---|---|
|
Getting the value for the groupSearchBase
...
ldapRealm.groupSearchFilter = (uniqueMember=uid=%s,ou=People,dc=sos)
To verify this you can perform a directory search with you groupSearchBase and your groupSearchFilter. The result should show all groups the user is a member of.
Now set the groupNameAttribute to the name of the attribute that contains the group name.
ldapRealm.groupNameAttribute = cn
Hint: Please note that the whole content of this attribute must be used in the groupRolesMap attribute. Sometimes here is something like ou=Groups, dc=sos, cn=groupname . Please take the whole value for the mapping.
The whole configuration looks like this
...
| title | Group Search |
|---|---|
| collapse | true |
Verification with ldapSearch
ldapsearch -h localhost -p 389 -b "ou=Groups,dc=sos" -s sub "uniqueMember=uid=ur,ou=People,dc=sos" -x
This search should return the group entries the user is a member. Please identify the attribute that contains the group name that should be used in the user roles mapping.
| Code Block | ||
|---|---|---|
| ||
# extended LDIF
#
# LDAPv3
# base <ou=Groups,dc=sos> with scope subtree
# filter: uniqueMember=uid=ur,ou=People,dc=sos
# requesting: ALL
#
# sos, Groups, sos
dn: cn=sos,ou=Groups,dc=sos
description: Employees of SOS GmbH
objectClass: top
objectClass: groupofuniquenames
cn: sos
uniqueMember: uid=ur |
...
,ou=People,dc=sos |
...
uniqueMember: uid=fTester,ou=People,dc=sos
# apl, Groups, sos
dn: cn=apl,ou=Groups,dc=sos
objectClass: top
objectClass: groupofuniquenames
cn: apl
uniqueMember: uid=ur,ou=People,dc=sos
uniqueMember: uid=fTester,ou=People,dc=sos
# search result
search: 2
result: 0 Success
# numResponses: 3
# numEntries: 2
|
Verification with LDAP Browser
groupSearchBase and your groupSearchFilter. The result should show all groups the user is a member of.Now set the groupNameAttribute to the name of the attribute that contains the group name.
ldapRealm.groupNameAttribute = cn
Hint: Please note that the whole content of this attribute must be used in the groupRolesMap attribute. Sometimes here is something like ou=Groups, dc=sos, cn=groupname . Please take the whole value for the mapping.
The whole configuration looks like this
| Code Block | ||||
|---|---|---|---|---|
| ||||
[main]
ldapRealm = com.sos.auth.shiro.SOSLdapAuthorizingRealm
ldapRealm.contextFactory.url = ldap://centos6_9_ldap.sos:389
ldapRealm.userDnTemplate = uid={0},ou=People, dc=sos
ldapRealm.groupSearchBase = ou=Groups,dc=sos
ldapRealm.groupNameAttribute = cnldapRealm.groupSearchFilter = (uniqueMember=uid=%s,ou=People,dc=sos)
# Mapping of a LDAP group to roles. You can assign more than one role with separator sign |
ldapRealm.groupRolesMap = \
sos : it_operator, \
apl : administrator|application_manager
rolePermissionResolver = com.sos.auth.shiro.SOSPermissionResolverAdapter
rolePermissionResolver.ini = $iniRealm
ldapRealm.rolePermissionResolver = $rolePermissionResolver
securityManager.realms = $ldapRealm
cacheManager = org.apache.shiro.cache.MemoryConstrainedCacheManager
securityManager.cacheManager = $cacheManager
# Session timeout in milliseconds
securityManager.sessionManager.globalSessionTimeout = 900000
|
Substitution of the username
Sometimes the values of the member to not contain the username from the login but e.g. the cn of the user. In that case you have to search the user first and specify the name of the attribute that should be used instead of the username from the login .
To achive this, specify a searchBase, a userSearchFilter and a userNameAttribute.
ldapRealm.searchBase = ou=People,dc=sosldapRealm.userSearchFilter = (uid=%s)
Verification with ldapSearch
ldapsearch -h localhost -p 389 -b "ou=People,dc=sos" -s sub "uid=fTester" -x
This search should return the user with the given username. Please identify the attribute that should be used for the substitution in the group search base if it is not the username from the login.
| Code Block | ||
|---|---|---|
| ||
# extended LDIF
#
# LDAPv3
# base <ou=People,dc=sos> with scope subtree
# filter: uid=fTester
# requesting: ALL
#
# fTester, People, sos
dn: uid=fTester,ou=People,dc=sos
mail: info@sos-berlin.com
uid: fTester
givenName: Fritz
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: inetorgperson
sn: Tester
cn: Fritz Tester
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
|
Verification with LDAP Browser
Substitution of the username
Sometimes the values of the member to not contain the username from the login but e.g. the cn of the user. In that case you have to search the user first and specify the name of the attribute that should be used instead of the username from the login .
To achive this, specify a searchBase, a userSearchFilter and a userNameAttribute.
ldapRealm.searchBase = ou=People,dc=sosldapRealm.userSearchFilter = (uid=%s)To check the user search perform a directory search with your LDAP client. You should find exactly the one user entry of the given username.
...