Page History
...
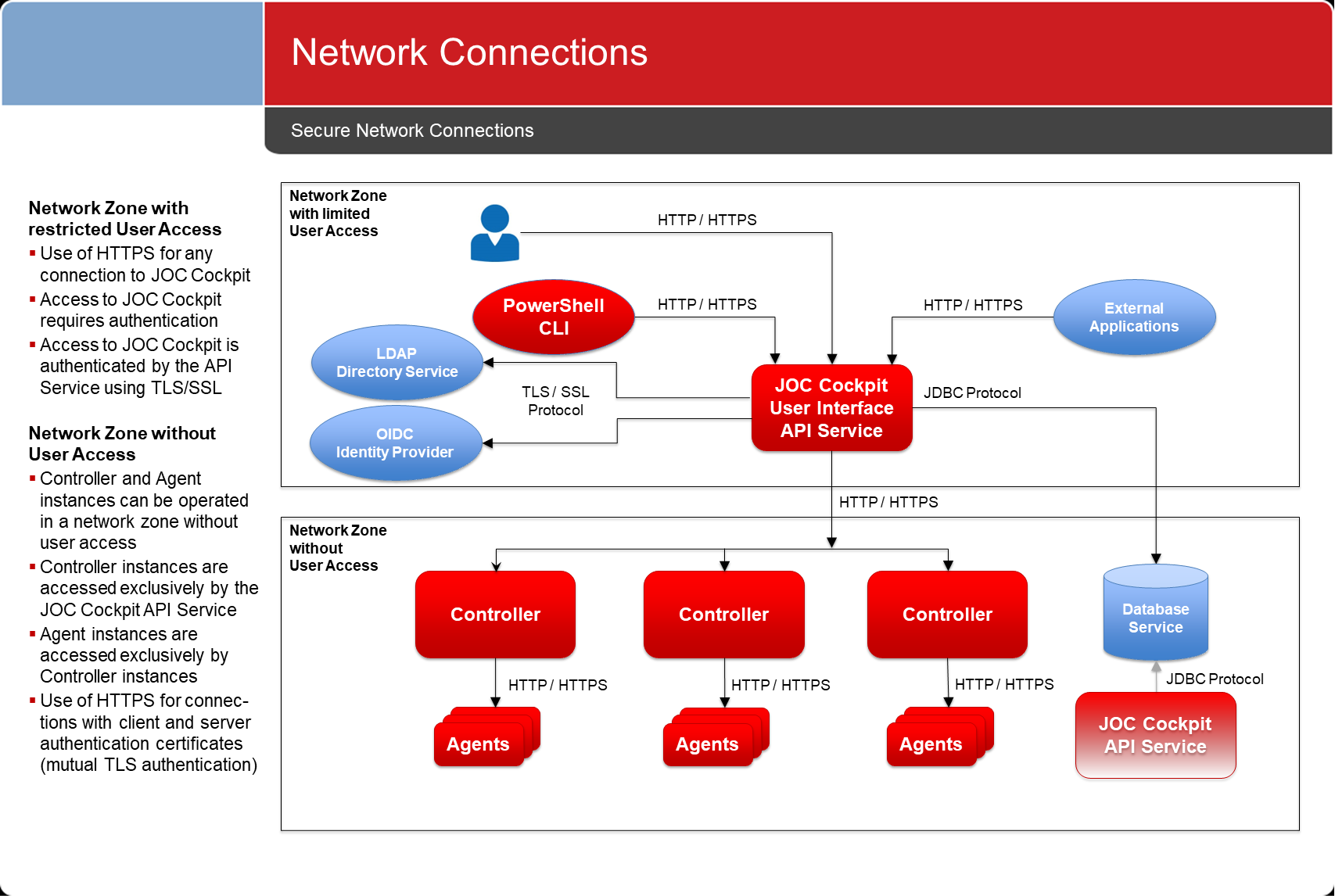
The architecture introduced with the JOC Cockpit ensures that users are restricted to directly access accessing the JOC Cockpit as illustrated with in the diagram below. The JOC Cockpit calls the JS7 - REST Web Service API which, in turn, has access to the JS7 Controller instances. There is no connection from the JOC Cockpit to Agents.
See the JS7 - System Architecture article for more information.
...
HTTP / HTTPS Connections
As indicated with in the schematic architecture diagram above, connections between the JOC Cockpit, the REST Web Service API and the Controllers & Agents can be carried out using both HTTP and HTTPS protocols. By default after installation HTTP will be used. However, system administrators are recommended to implement HTTPS connections.
- Information about securing JOC Cockpit connections can be found from the JS7 - JOC Cockpit HTTPS Connections article.
- Information about setting up secure connections between the JOC Cockpit and Controllers can be found from in the JS7 - Controller HTTPS Connections article.
- Consider Refer to the JS7 - Agent HTTPS Connections for article for information about securing the connections between Controller instances and Agents.
...
Authorization tokens are used for communication between users and the JOC Cockpit, between the JS7 REST Web Service API and between the Controller instances and Agents. This means that if an attacker is able to take over and to use a token they will only be able to bypass a part of the communication chain only.
Authorization Token for JOC Cockpit
The JOC Cockpit generates an authorization token each time a user logs on and saves this token either in the browser's local storage , if Remember Me is set on logging in, or in the browser's session storage , if Remember Me is not set. Note that there are situations when users can leave a valid authorization token on their file system although they are no longer working with the JOC Cockpit:
...
The default value of 900.000 milliseconds translates to 15 minutes. To apply changes to this value the The JOC Cockpit has to be restarted to apply changes made to this value.
If a user does not logout from the JOC Cockpit but, for example, closes the browser or browser tab then:
- the authorization token will remain valid for the specified period since the user's last activity,
- the user session in JOC Cockpit will be closed, however, the JS7 REST Web Service API will accept the authorization token for the specified period.
...
JOC Cockpit stores the user's profile settings with in its database. When a user logs in for the first time then the settings of the default profile account are copied to the user profile. By default the profile of the "root" account that ships with the shiro.ini file is used as the default user profile.
...
The Remember Me setting in the JOC Cockpit Log In form shown below is a convenient function for users working in "normal" environments. However it should be used with caution in sensitive environments as it could allow unauthorized access to JOC Cockpit by third parties when users would do not rigorously lock their computer. In addition, storing credentials with the browser can be considered a questionable practice.
...
- The Log In form will not be emptied after a period of time when Remember Me is set and a user does not log in again,
- The behavior specified in the table above is independent of the fact that whether or not the browser is configured to store login information.
...
A user password cannot be reset or changed with the JOC Cockpit. Depending on the configuration set in the shiro.ini configuration file:
- users should ask their system administrator to modify their password in the
shiro.inifile if local user management is used, - any password changes effected for a directory service are automatically considered when using the JOC Cockpit if LDAP configuration is used.
...