Page History
...
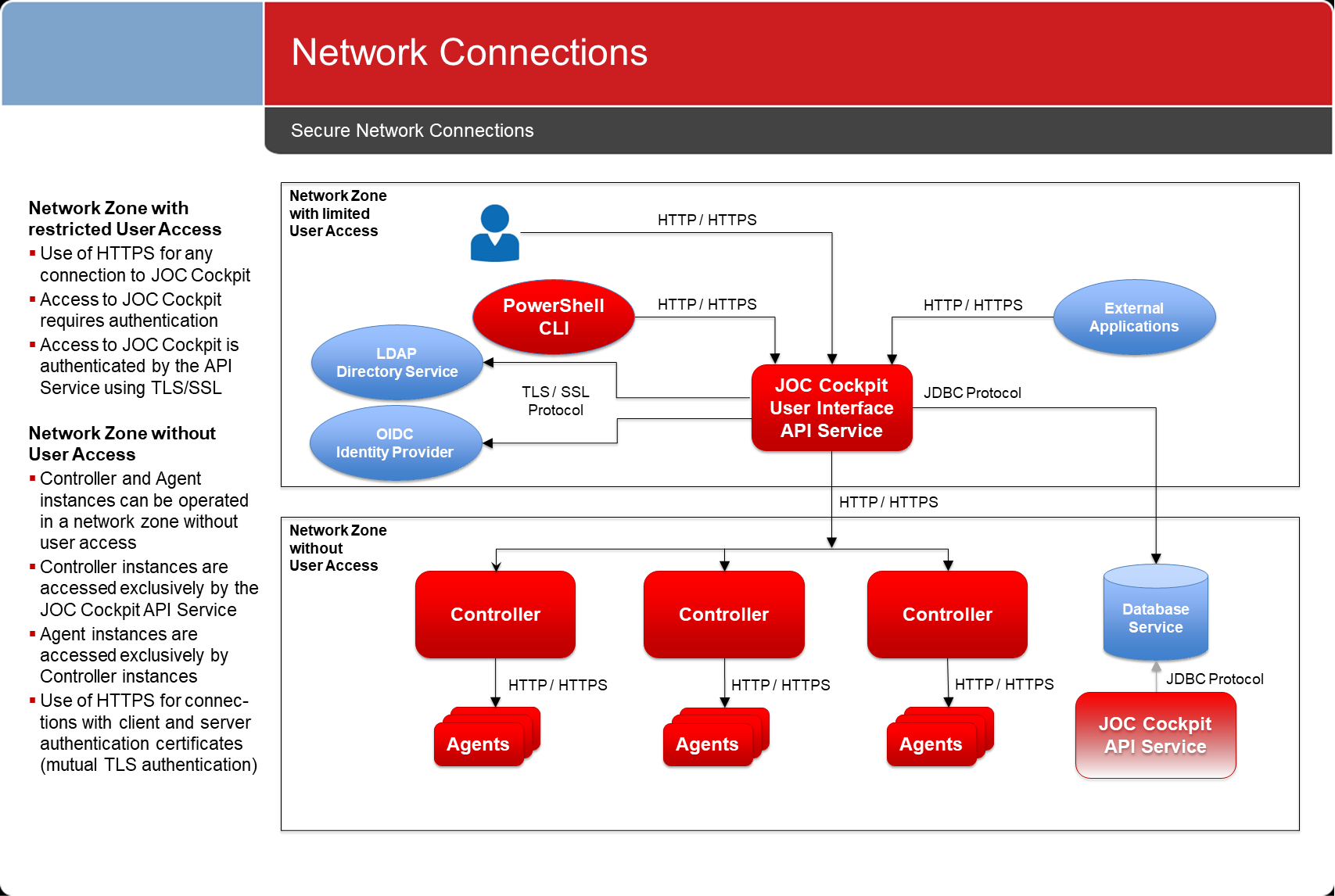
JS7 products use the following connections:
The above diagram suggests that the JOC Cockpit is the only JS7 product that is directly exposed to user access.
- This allows to operate JS7 in different network zones. JOC Cockpit can be located in a deployment zone from which users deploy workflows. Controllers and Agents can be operated in separate network zones.
- The underlying principle is to allow connections from a less secure deployment zone to more secure zones and to deny connections to go the opposite way.
- If jobs are operated on JS7 Agents that require access to the JS7 REST Web Service API then it is recommended to set up additional JOC Cockpit API Server instances. Such instances do not include the user interface but serve the REST Web Service API only. Any number of API Server instances can be set up and they can be operated close to JS7 Agents.
Network Connections
All network connections are unidirectional, as indicated by the direction of the arrows in the diagram above.
...
- All network connections make use of HTTP:
- Connections by users to the JS7 - Browser User Interface
- Connections by the PowerShell CLI or external applications to the JS7 - REST Web Service API
- Connections by the JOC Cockpit to the JS7 Controller using the JS7 REST Web Service API
- Connections by JS7 Controller instances to Agents
- Port Usage
- The JOC Cockpit can be accessed at port 4446
- The JOC Cockpit REST Web Service can be accessed at port 4446
- The JS7 Controller uses port 4444
- The JS7 Agent listens to port 4445
- Network Interface Usage
- By default JS7 products will listen to the above mentioned ports on any available network interfaces.
- Firewall Settings
- Open ports in your firewall exclusively for the hosts, protocols and ports as specified above. Consider allowing connections only for the directions indicated in the diagram above.
...
Database Connections
The JOC Cockpit API Service is the only JS7 product that uses a database.
...
- Refer to the hints provided in the JS7 - JOC Cockpit - Secure Operation article.
- The JOC Cockpit by default ships with the
JOC-INITIALIdentity Service, see JS7 - Identity Services which includes:- use of the JS7 - JOC Identity Service for authentication with user accounts and passwords stored as hash values in the JS7 - Database.
- use of local role assignment,
- the following default values for user accountsaccount, passwords password and assigned roles (see JS7 - Manage User Accounts for more information):
- Active User Account:
- user account:
root - password:
root
- user account:
- Active Role:
all
- Available Roles:
administratorallapi_userapplication_managerbusiness_userincident_managerit_operator
- Active User Account:
- no other accounts are available by default.
- The JS7 Controller is not accessed by users but exclusively by the JOC Cockpit via the JS7 - REST Web Service API.
- Default authentication for the connection from the JOC Cockpit to the Controller is provided by asymmetric passwords available with:
- the JS7 - Settings page in section "joc" with the settings
controller_connection_joc_passwordandcontroller_connection_history_password, - the Controller's
private.conffile which holds thepasswordsetting by default as a hashed value.
- the JS7 - Settings page in section "joc" with the settings
- It is recommended that JS7 - Certificate based Authentication using HTTPS connections with mutual authentication is implemented, see JS7 - Controller HTTPS Connections.
- Default authentication for the connection from the JOC Cockpit to the Controller is provided by asymmetric passwords available with:
- JS7 Agents are not accessed by users but exclusively by a JS7 Controller. Default authentication is not provided.
...
- Using the default
rootuser account that ships with the JOC Cockpit is not recommended. The default user account is intended to enable initial login only. - A fine-grained set of permissions is available that can be applied to any operation in the JOC Cockpit and in the JS7 REST Web Service API. Such permissions can freely be grouped to roles, see JS7 - Authorization.
- JS7 - Identity Services offer a number of authentication methods that can be combined for single-factor and multi-factor authentication (MFA).
- The JS7 - LDAP Identity Service can be used to establish role assignment for users based on membership in LDAP Directory Service security groups.
- The JS7 - Certificate Identity Service and JS7 - FIDO2 Identity Service can be used for MFA.
...
Identity Services
Default Configuration
- LDAP Directory Service integration is available from the JS7 - LDAP Identity Service, but is not active by default.Identity Services offer a number of authentication methods such as LDAP, OIDC, FIDO2 etc.
- By default access to the JOC Cockpit is ruled by local authentication management from the Using the default configuration with local authentication from the JS7 - JOC Identity Service for access to the JOC Cockpit is not recommended as it . This Identity Services stores hashed passwords credentials in the database.
- No other Identity Service is active by default.
Secure Configuration
- Users can switch to one of the supported Identity Services such as
- JS7 - LDAP Identity Service,
- LDAP Directory Services can be accessed for authentication and authorization:
- users can connect by specifying their domain account.
- membership in security groups can be optionally mapped to roles managed with JOC Cockpit.
- The use of LDAP allows operation of a JOC Cockpit configuration that contains neither user account data, passwords nor user role assignments.
- This applies to any LDAP compliant product such as Microsoft Active Directory®, OpenLDAP etc.
- LDAP Directory Services can be accessed for authentication and authorization:
- JS7 - OIDC Identity Service
- OIDC offers token based authentication that includes a direct connection between the user and the Identity Provider.
- JOC Cockpit has no access to passwords in this authentication scheme.
- JS7 - Certificate Identity Service
- Client Authentication certificates can act as a replacement for passwords.
- The Identity Service can be used for single-factor authentication and for MFA.
- JS7 - FIDO2 Identity Service
- Public/private key authentication by use of a secure device eliminates the use of passwords.
- The Identity Service can be used for single-factor authentication and for MFA.
- JS7 - LDAP Identity Service,
- A number of Identity Services can be combined to be optional or required. This allows to authenticate with one Identity Service from a list of available services and it allows to force authentication with all configured Identity Services.
- Users should consider to disable the initial JOC Identity Service when more secure Identity Services are in placeFor details about LDAP support see the JS7 - LDAP Identity Service article.
Credentials Management
Database Credentials
...
Overview
Content Tools