...
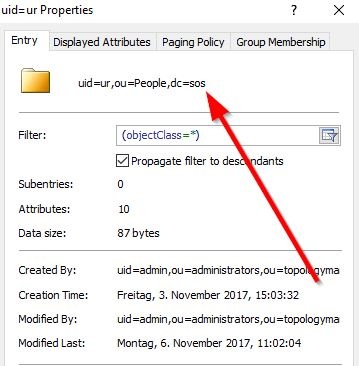
With authentication you will check for a valid account/password combination. To achieve this you have to specify the userDnTemplate. The parameters for the userDnTemplate can be taken from an account's properties page as displayed in the below screenshot taken from an LDAP browser.
For The template setting for the account shown in the screenshot the template setting above would be (replacing the uid value with {0}):
ldapRealm.userDnTemplate = uid={0},ou=People,dc=sos
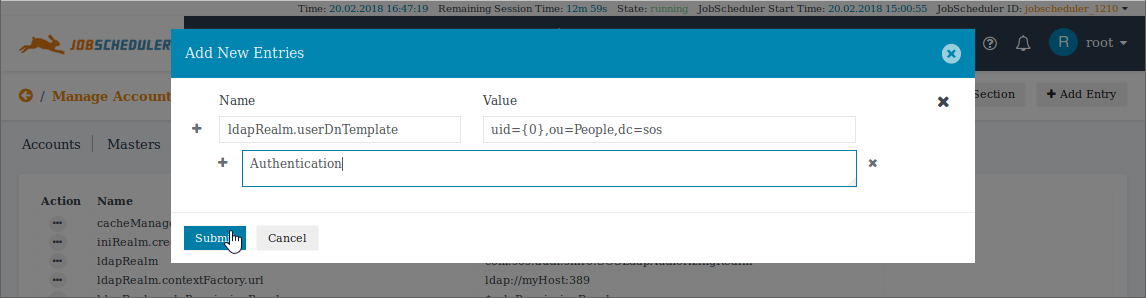
The This userDnTemplate item can be added to the Basic LDAP configuration using the Add Entry button of the Main Section editor as shown in the next screenshot:
Note that the '+' and 'x' symbols in the screenshot can be used to increase the number of entries added at once.
After setting up the Basic LDAP Configuration (described in 1. above) and adding the userDnTemplate the [main] section of the shiro.ini.active file will look like this:
...
| Code Block | ||||||||
|---|---|---|---|---|---|---|---|---|
| ||||||||
# ur, People, sos dn: uid=ur,ou=People,dc=sos mail: ********* uid: ur givenName: Uwe objectClass: top objectClass: person objectClass: organizationalPerson objectClass: inetorgperson sn: Risse cn: Uwe Risse preferredLanguage: de # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1 |
Example for a public LDAP Server
The following example uses a publicly available LDAP server at forumsys.com. In our experience this server provides a reliable means of getting an initial LDAP configuration up and working.
For this server the The command to check the userDnTemplate in the the forumsys ldapSearch utility would be:
...
| Code Block | ||||||||
|---|---|---|---|---|---|---|---|---|
| ||||||||
# extended LDIF # # LDAPv3 # base <uid=gauss,dc=example,dc=com> with scope subtree # filter: (objectclass=*) # requesting: ALL # # gauss, example.com dn: uid=gauss,dc=example,dc=com objectClass: inetOrgPerson objectClass: organizationalPerson objectClass: person objectClass: top cn: Carl Friedrich Gauss sn: Gauss uid: gauss mail: gauss@ldap.forumsys.com # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1 |
Note: ldapSearch Parameters
The option -x is used in all the ldapSearch examples in this article. It is possible that your LDAP Directory Service does not allow this option and you have to specify an Account and a Password. If this is the case then the command would be:
...
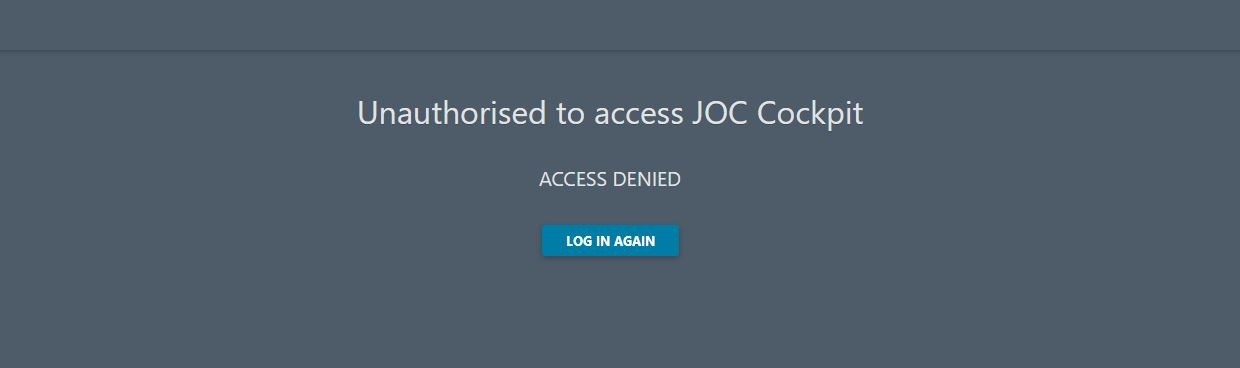
Try to login with an LDAP Account/Password combination. Use an Account that you have verified to be correct by executing the ldapSearch command described above. If there are no Role(s) configured for the Account but the authentication works then you will see the following screen that complains about missing authorization after successful authentication:
| Anchor | ||||
|---|---|---|---|---|
|
...
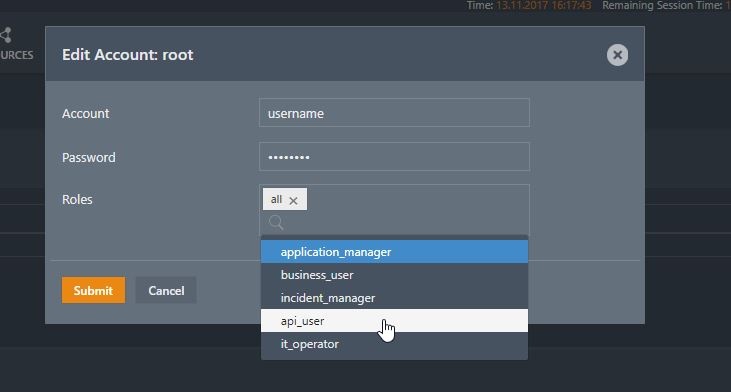
Role assignment in the shiro.ini file is configured in the Manage Accounts view of the JOC Cockpit . Do not enter the Password and is described in the Authentication and Authorization - Managing User Accounts article.
Note that a Password should not be entered for a User Account that is to be authenticated by an LDAP Directory Service.
The following screenshot shows the allocation of one of the default roles:
The Roles assigned to an entry are saved in the [users] section of the shiro.ini configuration file according to the following syntax:
...
The JOC Cockpit Account Management will can be used to add entries to the [users] section for Role assignment.
...
Settings:
ldapRealm.groupRolesMap
If the Roles are assigned with the JOC Cockpit Account Management, i.e. there is a [users] section available in the shiro.ini configuration file, then you can skip this chapter.
shiro.ini configuration file. This is done in the a [main] section with the groupRolesMap setting....
After specifying the User Search the shiro.ini.active configuration file will look like this:
...
The searchBase is the value of the base DN (or ParentDN in the screenshot above).
Hint: If if the attribute name in your environment is not the default memberOf then you can specify the name of the attribute with the groupNameAttribute key as described in the next section.
...