Introduction
- The JS7 - Identity Services offer management of user accounts for authentication and authorization.
- FIDO is a set of authentication standards based on the work of the FIDO Alliance and W3C.
- The underlying WebAuthn API is used by the FIDO2 protocol Passkeys protocols.
- Users can adjust the Identity Service to work compatible with FIDO2 and Passkeys.
- The FIDO Identity Service integration is available from JOC Cockpit
-
FEATURE AVAILABILITY STARTING FROM RELEASE 2.6.0
JOC-1546 - Getting issue details... STATUS
Terminology
The FIDO protocol knows of the following roles involved in authentication:
- Security Key is a physical device that can connect using USB, NFC, BLE etc. and that hosts an Authenticator. Examples include YubiKey®, TrustKey® etc.
- Authenticator is a system that provides credential services such as creating private/public key pairs. Authenticators are available as Roaming Authenticators (=Security Keys) and as Platform Authenticators (=hosted with the user's device or in a cloud service).
- Client is the JOC Cockpit GUI that performs login by use of Authenticator services.
- Relying Party is the JS7 - REST Web Service API that verifies Client signatures to prove the identity of a user.
FIDO Flows
if one or more FIDO Identity Services are configured as a first factor for authentication then this is offered to users from JOC Cockpit's login screen like this:
This suggests the following flow to users:
- Users first have to register their Security Key device.
- Later on users can use the Continue with <Identity Service Name> link to authenticate.
Registration by Users
This step is performed by users who apply for registration of their Security Key to authenticate with JOC Cockpit.
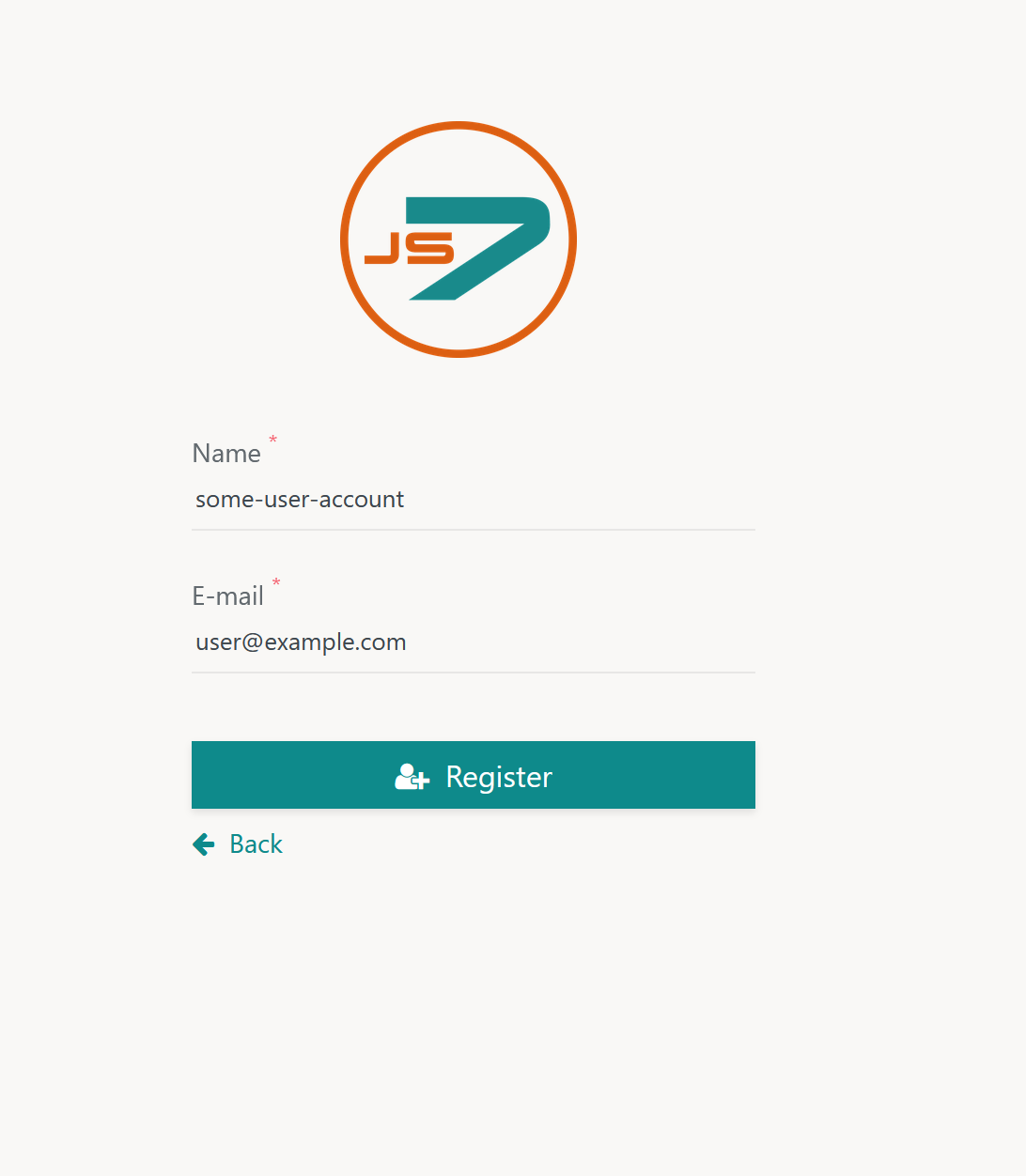
When clicking the Register Security Key link then the following screen is displayed to specify
- the name of the user account,
- the user's e-mail address.
- Users can register just once for a given e-mail address and account.
- Users can register with additional JOC Cockpit instances specifying the same account and e-mail address.
- Users can add additional Security Key devices from their Profile once they are logged in.
If a JS7 - JOC Cockpit Cluster is operated then registration of Security Keys has to be performed for each JOC Cockpit instance individually.
- Users start the registration flow using the secondary JOC Cockpit URL.
- Users register the same Security Key device, account and e-mail address.
The same applies if the JOC Cockpit URL will change.
Registration Request
The steps for registration can look differently if the user's computer is configured to use a number of Authenticators:
- For example, if Windows® Hello is enabled, optionally for Windows login, then users first might receive a popup window to login using the Windows Authenticator.
- Users can cancel the popup window if they want to register a Security Key that is not managed by Windows® Hello.
Next a popup window is displayed that informs about the fact that a Security Key will be used for access to the JOC Cockpit.
At this point in time users should have their Security Key readily available and connected. For example, if a USB stick is used then it should be connected to the computer that runs the browser with access to JOC Cockpit.
A follow-up popup window informs abut the fact that the brand and model of the Security Key will be displayed like this:
In the next step the user is asked to specify the PIN for access to the Security Key. If a PIN, biometric characteristics or other will be requested to access the Security Key depends on the nature of the Authenticator.
- The PIN or other characteristics are configured once during initial operation of a Security Key. The same input is required when the Security Key is used later on.
- If the Security Key is used for the first time then a dialog is added to specify and to confirm the PIN or other characteristics.
The next popup window asks the user for a gesture. This will happen
- if the FIDO Identity Service is configured for preferred or required user verification,
- if the user's Security Key is equipped for use of gestures such as touching a USB Stick.
With this step the registration request is completed.
The user's registration request is added to the Identity Service's Pending Requests, see Approval flow.
E-Mail Confirmation
The user is sent an e-mail from JOC Cockpit that includes a link to JOC Cockpit which is used to confirm the user's e-mail address like this:
Users should check if the indicated e-mail address corresponds to their address and if the URL offered to confirm their e-mail address starts from the same hostname as the JOC Cockpit URL used for registration. If in doubt users should not follow links in the confirmation mail but get in contact to their JS7 administrator.
Clicking the link will bring up a JOC Cockpit confirmation window. The information that a user did follow the link to confirm the e-mail address is stated with the Identity Service's Pending Requests, see Approval flow.
Adding Security Keys
Users who are logged in using the FIDO Identity Service can register additional Security Keys for their account.
The user's profile page offers the action to add Security Keys like this:
If a user clicks the + icon then the same registration dialog occurs as explained above.
As a result the user's account will be added an additional Security Key that can be used alternatively for authentication.
Registration by Administrators
JS7 administrators can register Security Keys on behalf of themselves or of other users.
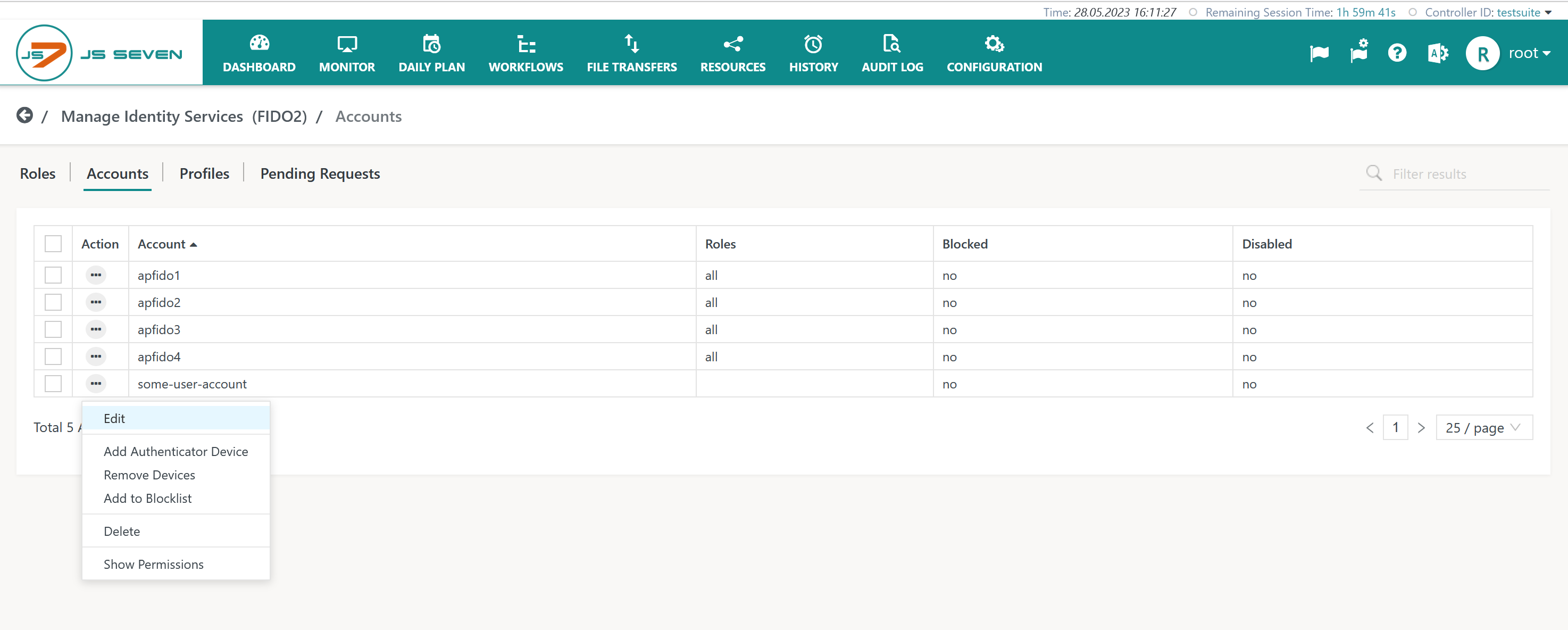
The Accounts sub-view offers the action menu item Add Security Key Device:
When this action menu item is clicked then the same steps occur as for registration by users.
- JS7 Administrators can register Security Keys for themselves.
- JS7 Administrators can create accounts and can register Security Keys for other accounts.
Approval
The approval flow is performed by a JS7 administrator and includes to check pending registration requests.
Pending Requests
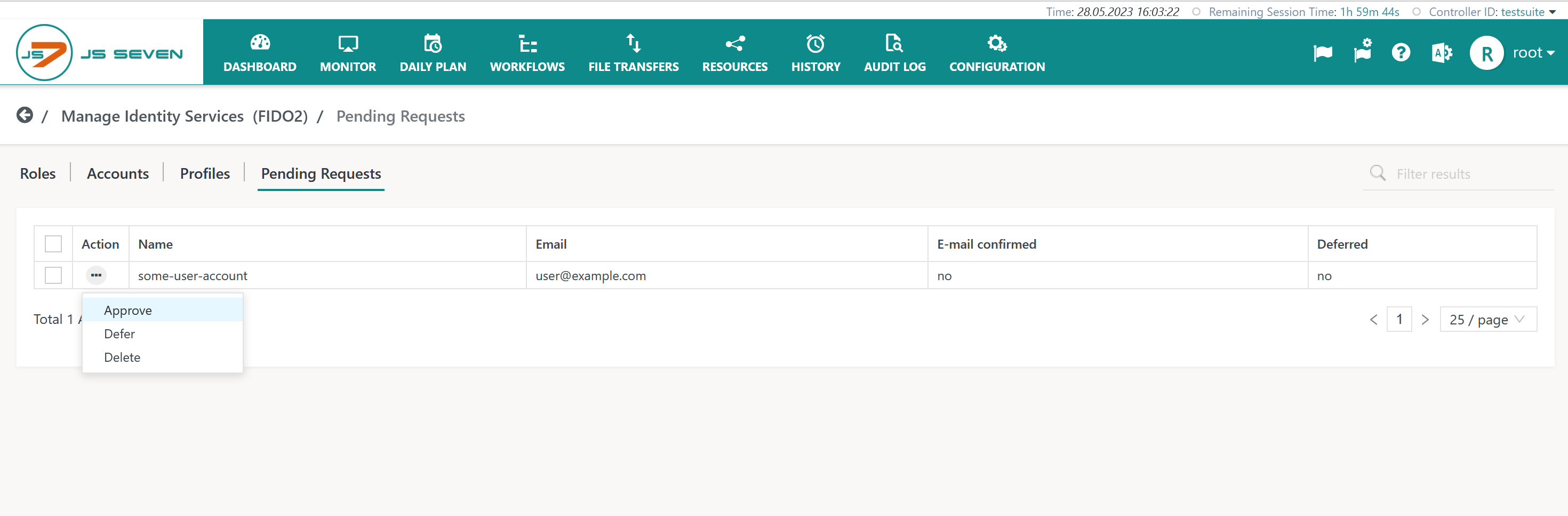
The users' registration requests are added to the Identity Service's Pending Requests sub-view like this:
Explanation:
E-Mail confirmed: The column will hold the value yes if users did follow the link for e-mail confirmation that was sent by mail from JOC Cockpit. JS7 administrators can approve a registration request without considering e-mail confirmation. However, at this stage it is not guaranteed that the e-mail address is owned by the person who requested registration.Deferred: JS7 administrators can use the deferred status to manage priorities of approvals. The deferred status is informational and is not related to approval.
Approval of Requests
To approve a pending request JS7 administrators can use the request's action menu like this:
Explanation:
Approve: The registration request will be approved and will be removed from the list of Pending Requests. At the same time the approved user account is added to the list of accounts in the Accounts sub-view. In a next step the JS7 administrator should assign one or more roles to the user account.Defer: The operation will change the related column value to yes. JS7 administrators can use the deferred status to manage priorities of approvals. The deferred status is informational and is not related to approval.Delete: The pending request will be deleted.
Assignment of Roles
With approval being completed the user account can login to JOC Cockpit. However, it requires assignment of roles to allow the user any actions in the JOC Cockpit user interface and REST Web Service API:
- From the Accounts sub-view the action menu for the respective user account offers a number of actions.
- The Edit action is used to assign roles.
When selecting the Edit action the following popup window is displayed:
- This allows to assign the user account one or more roles.
- The roles can be managed individually per environment. The below screenshot shows the JS7 - Default Roles and Permissions available with JOC Cockpit.
For more information about roles and permissions see JS7 - Management of User Accounts, Roles and Permissions.
E-Mail Notification
With approval of a user's registration request the user is sent an e-mail from JOC Cockpit that notifies about successful completion of the registration request like this:
Users should check if the indicated e-mail address corresponds to their address and if the URL offered to navigate to JOC Cockpit starts from the same hostname as the JOC Cockpit URL used for registration. If in doubt users should not follow links in the confirmation mail but get in contact to their JS7 administrator.
Authentication
After approval of the registration request users can login to JOC Cockpit and can authenticate using their registered Security Key.
From JOC Cockpit's initial login screen users can follow the Continue with FIDO2 link. The name FIDO2 corresponds to the name that is assigned the Identity Service.
The steps for authentication are similar to the registration request:
- The user connects the Security Key device to the computer.
- The user enters a PIN or other characteristics for access to the Security Key.
- The user performs a gesture of consent, for example by touching a USB stick, if requested by the Identity Service.
If Windows® Hello is enabled then as a first step users might have to select from the list of Authenticators offered.
- If Windows® Hello is used as an Authenticator for FIDO Passkeys then this option can be used.
- If a Security Key, for example a USB-Stick, is used then this option has to be selected.