Page History
| Table of Contents |
|---|
Introduction
- When JOC Cockpit is installed for a high security level then deployment of scheduling objects forces external signing.
- For the low security level the private key of the
rootaccount available with the JS7 database is used for all users. - For the medium security level the user's individual private key available with the JS7 database is used.
- For the high security level signing is performed outside of JOC Cockpit.
- For the low security level the private key of the
- For details see JS7 - Security Architecture.
Prerequisites
Required: User Signing Certificate
Each user with the permission to deploy has to add his its X.509 signing certificate to JOC Cockpit.:
Optional: Root CA Certificate
In addition, the X.509 certificate of the Root CA that signed the user's signing certificate can be added to JOC Cockpit. There is a single Root CA certificate for all user profiles.
- Any user signing certificates have to be published rollout out to the Controller and Agents. Certificates are stored to the
config/private/trusted-x509-keysfolder of Controller and Agent installations. - If a Root CA certificate is present in JOC Cockpit, then it is sufficient to add the Root CA certificate to the
config/private/trusted-x509-keysfolder of Controller and Agent installations.- No further user
signingcertificates have to be added to the Controller or Agents as long as the user signing certificates were is created by the given Root CA. - This mechanism implies that any user signing certificate signed by the same Root CA certificate will be accepted.
- Users who do not wish to use this implicit mechanism should not add the Root CA certificate to Controller and Agents but should add individual user signing certificates only.
- No further user
...
The user has to export the desired configuration of scheduling objects with the Export operation available from the Configuration view.
- Deployment tasks include to
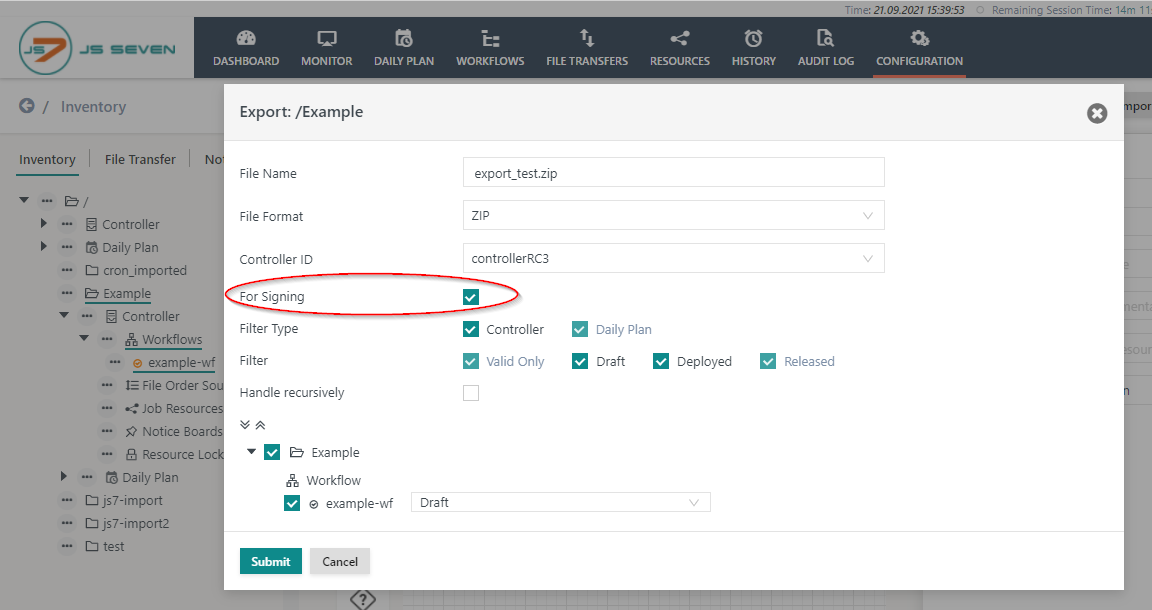
export scheduling objects with the checkbox "for Signing" checked to an archive file (.zip).
- unpack the exported archive
- The archive contains a
meta_inffile and the configurations.
- The archive contains a
- sign the configurations configuration files of scheduling objects and store the signature - base64 encoded - in a file with the same folder.
- Each signature file has to use the same name as the original configuration file of the scheduling object with an additional filename extension.
- for RSA/ECDSA signatures use the filename extension ".pem" or ".sig" respectively.
- for PGP signatures use the default filename extension ".asc".
- pack the archive once again to add signature files and make sure the
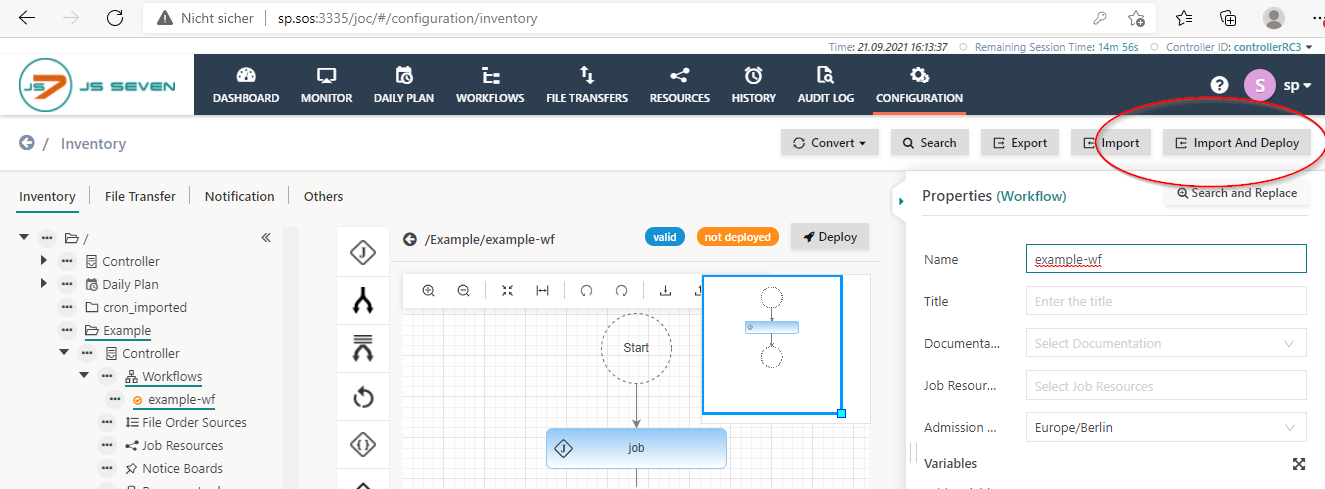
meta_inffile is still available with the root folder of the archive. - upload the archive using the Import And Deploy button.
Example
Export
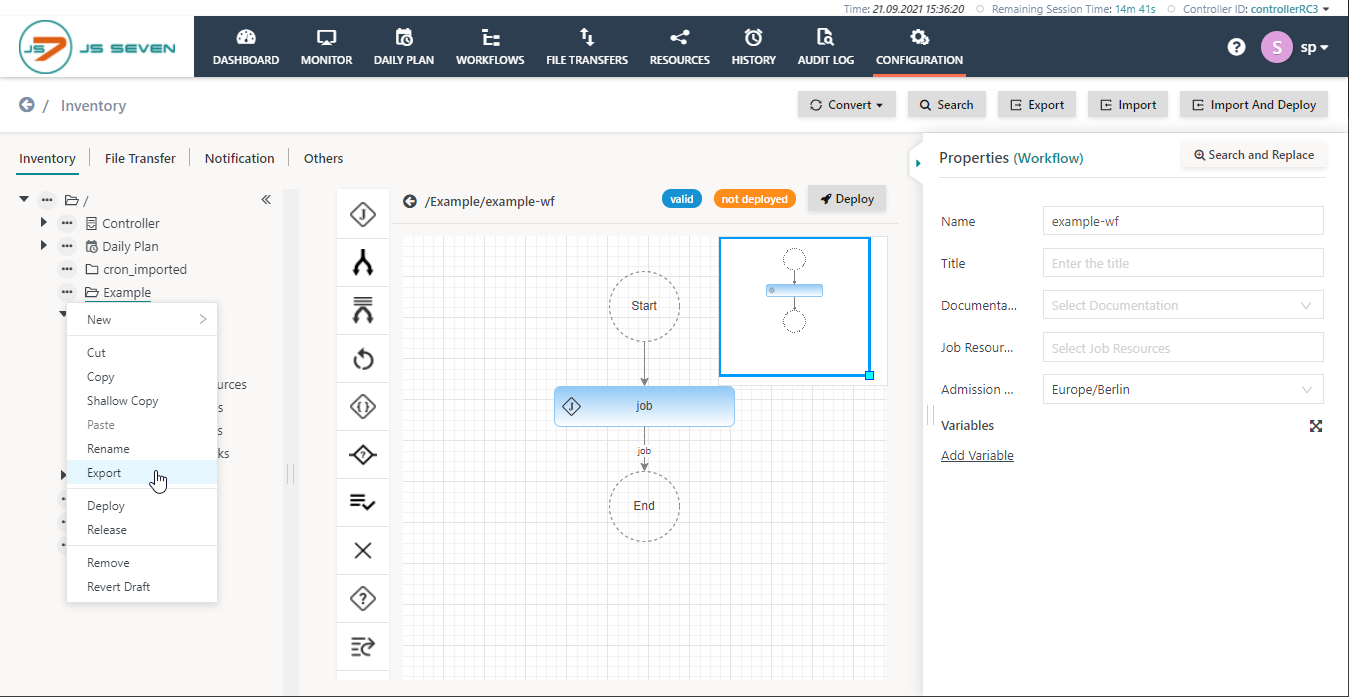
- Click Export either in in the context menu of the folder to export or from the button in the top right corner:
- In the Export pop-up popup window check the checkbox "for Signing":
- Select the scheduling objects to deploy.
Signing
It is recommended to perform the signing procedure on a secure device. It is essential that the signing process is performed in a secure manner outside of the server running JOC Cockpit.
Extract the configuration from the archive and preserve the folder structure of included scheduling objectsobject files:
Signing the configuration
...
-sha256- the signer algorithm
-sign c:\tmp\sos.private-ec-key.pem- the private key file to sign the content of the original configuration file
-out c:\tmp\example-wf.workflow.json.sha256- the path to the output file
- the file contains the binary representation of the signature
c:\tmp\example-wf.workflow.json- the path to original scheduling object file (in this example: workflow)
- the path to original scheduling object file (in this example: workflow)
| Code Block | ||
|---|---|---|
| ||
openssl base64 -in c:\tmp\example-wf.workflow.json.sha256 -out c:\tmp\example-wf.workflow.json.pem |
base64- OpenSSL switch to encode base64
-in c:\tmp\example-wf.workflow.json.sha256- the newly created binary signature file
-out c:\tmp\example-wf.workflow.json.pem- the base64 encoded text signature file according to the JOC Cockpit deployment naming convention
The procedure to add scheduling object files and signatures to an archive includes the following steps:
- Copy the newly created text signature
...
- files to the same
...
- folders as the scheduling object
...
- files.
- Pack the archive once again or add the
...
- signature files to the existing archive.
- The exported archive contains the
meta_inffile. This file does not have to be signed. Make sure the file is present in the root folder of the target archive.
- The exported archive contains the
- Import/Deploy this archive with the Import And Deploy function of JOC Cockpit
...
- .
Enter the signature algorithm using the default Java names for the signature algorithm:
...