Page History
...
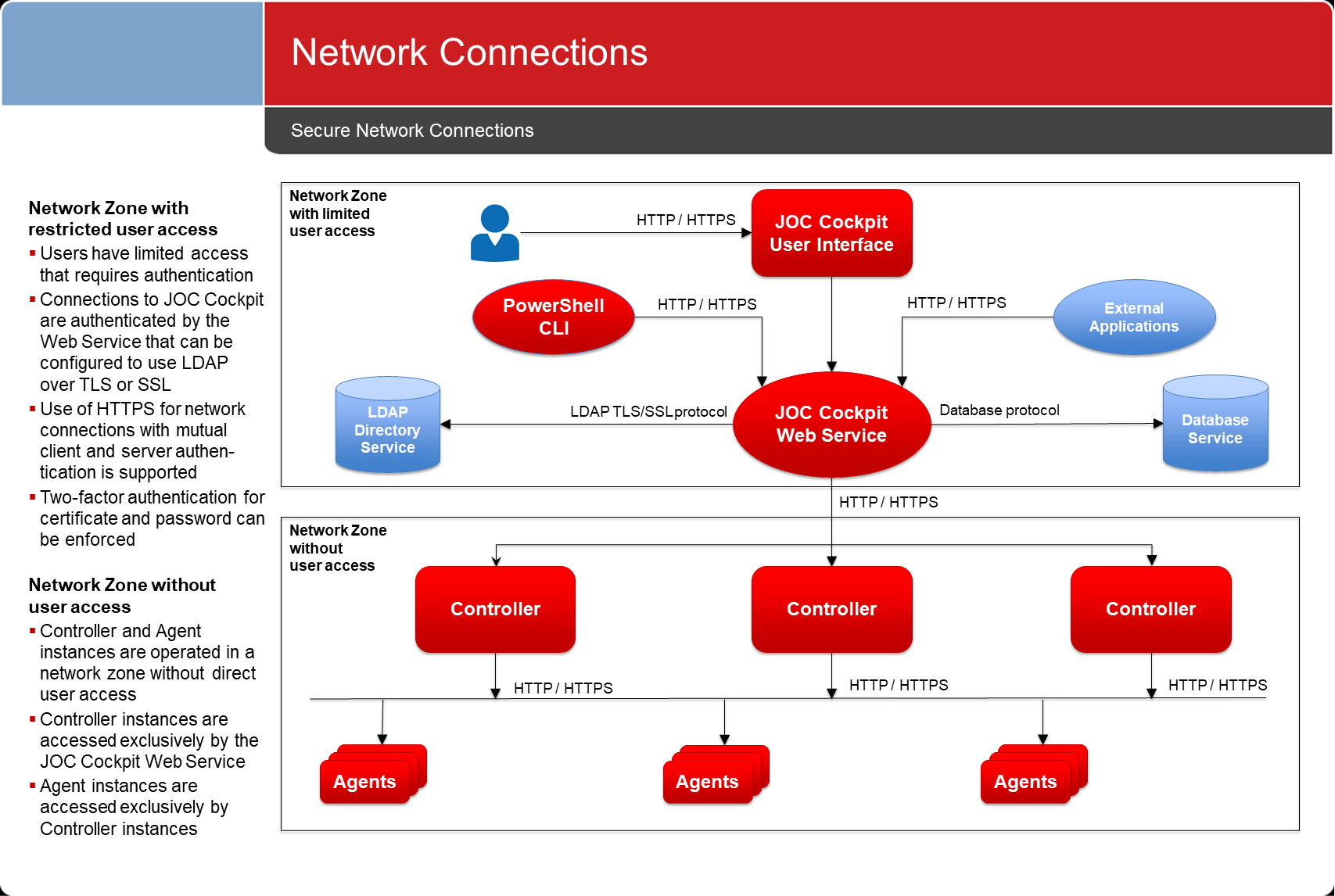
- Network connections between components use the HTTPS protocol.
- Such connections are secured by
- Connections are established in one direction only.
Certificate Management
Certificate
...
Preparation
| Flowchart |
|---|
JOC [label=" JOC Cockpit ",fillcolor="green"]
CA_Root [label=" Root CA ",fillcolor="orange"]
CA_Intermediate [label=" Intermediate CA ",fillcolor="orange"]
CA_RootCertificate [shape="ellipse",shape="ellipse",label="Root CA Certificate",fillcolor="orange"]
CA_IntermediateCertificate [shape="ellipse",label="Intermediate CA Certificate",fillcolor="orange"]
CA_Bundle [shape="ellipse",label="CA Bundle",fillcolor="yellow"]
PrimaryMaster_PrivateKey [shape="ellipse",label="PrimaryMaster Private Key",fillcolor="lightskyblue"]
# PrimaryMaster_Certificate [shape="ellipse",label="Primary Master Certificate",fillcolor="white"]
BackupMaster_PrivateKey [shape="ellipse",label="Backup Master Private Key",fillcolor="lightskyblue"]
# BackupMaster_Certificate [shape="ellipse",label="Backup Master Certificate",fillcolor="white"]
Agent_PrivateKey [shape="ellipse",label="Agent Private Key",fillcolor="lightskyblue"]
JOC -> CA_Root
JOC -> CA_Intermediate
CA_Root -> CA_RootCertificate [label=" create and sign "]
CA_Root -> CA_IntermediateCertificate [label=" sign "]
CA_Intermediate -> CA_IntermediateCertificate [label=" create "]
CA_RootCertificate -> CA_Bundle [label=" add "]
CA_IntermediateCertificate -> CA_Bundle [label=" add "]
# CA_Intermediate -> PrimaryMaster_PrivateKey [label=" create and sign "]
CA_IntermediateCertificate -> PrimaryMaster_PrivateKey [label=" create/sign "]
# CA_Intermediate -> BackupMaster_PrivateKey [label=" create and sign "]
CA_IntermediateCertificate -> BackupMaster_PrivateKey [label=" create/sign "]
# CA_Intermediate -> Agent_PrivateKey [label=" create and sign "]
CA_IntermediateCertificate -> Agent_PrivateKey [label=" create/sign "]
|
Certificate Deployment
| Flowchart |
|---|
JOC [label=" JOC Cockpit ",fillcolor="green"]
PrimaryMaster [label=" Primary Master ",fillcolor="lightskyblue"]
BackupMaster [label=" Backup Master ",fillcolor="lightskyblue"]
Agent [label=" Agent ",fillcolor="lightskyblue"]
CA_Bundle [shape="ellipse",label="CA Bundle",fillcolor="yellow"]
PrimaryMaster_PrivateKey [shape="ellipse",label="PrimaryMaster Private Key",fillcolor="lightskyblue"]
# PrimaryMaster_Certificate [shape="ellipse",label="Primary Master Certificate",fillcolor="white"]
BackupMaster_PrivateKey [shape="ellipse",label="Backup Master Private Key",fillcolor="lightskyblue"]
# BackupMaster_Certificate [shape="ellipse",label="Backup Master Certificate",fillcolor="white"]
Agent_PrivateKey [shape="ellipse",label="Agent Private Key",fillcolor="lightskyblue"]
JOC -> CA_Bundle
JOC -> PrimaryMaster_PrivateKey [label=" create/sign "]
PrimaryMaster_PrivateKey -> PrimaryMaster [label=" deploy "]
CA_Bundle -> PrimaryMaster [label=" deploy "]
JOC -> BackupMaster_PrivateKey [label=" create/sign "]
BackupMaster_PrivateKey -> BackupMaster [label=" deploy "]
CA_Bundle -> BackupMaster [label=" deploy "]
JOC -> Agent_PrivateKey [label=" create/sign "]
Agent_PrivateKey -> Agent [label=" deploy "]
CA_Bundle -> Agent [label=" deploy "]
|
Certificate Life Cycle
...
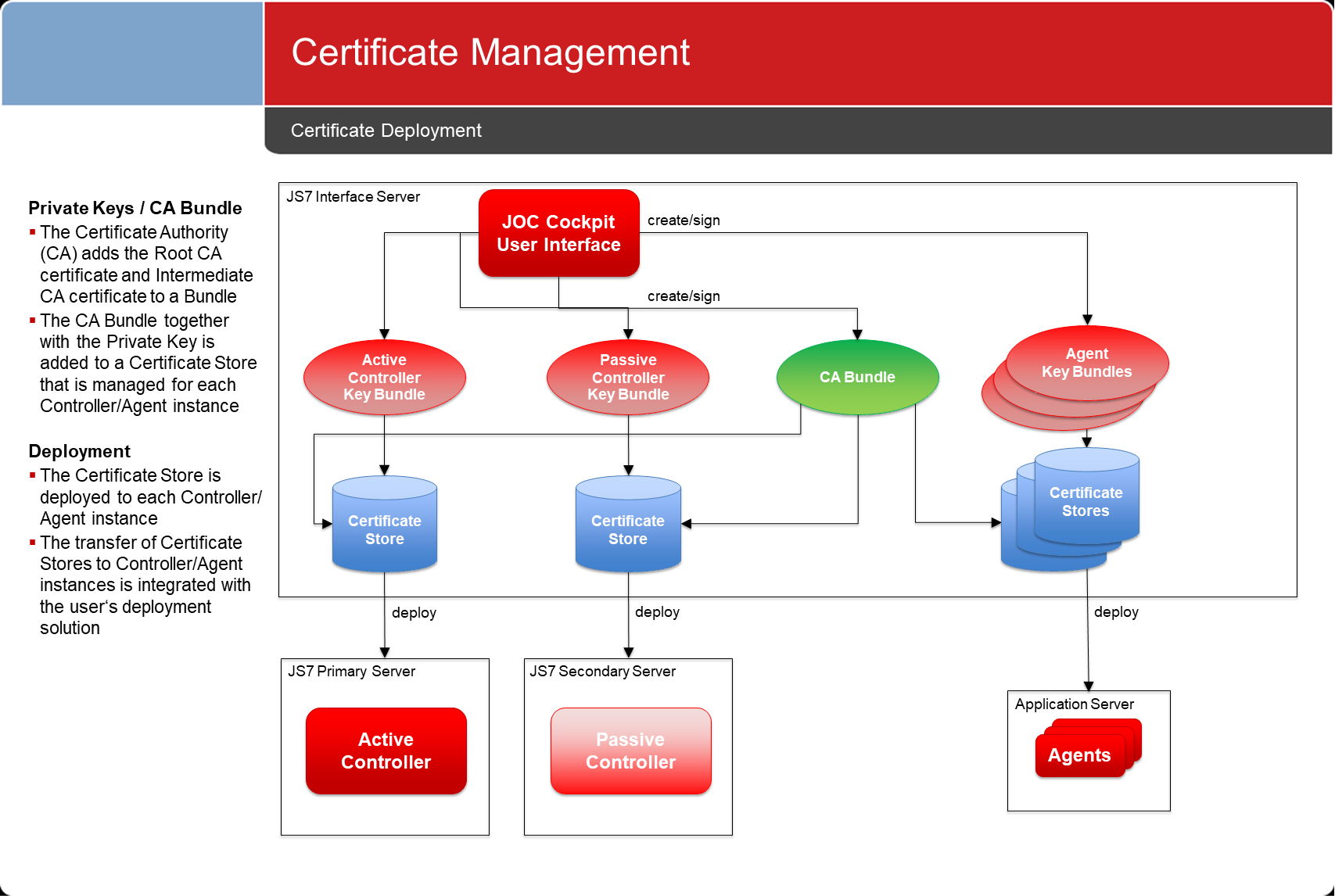
Certificate Deployment
Certificate Management Life Cycle
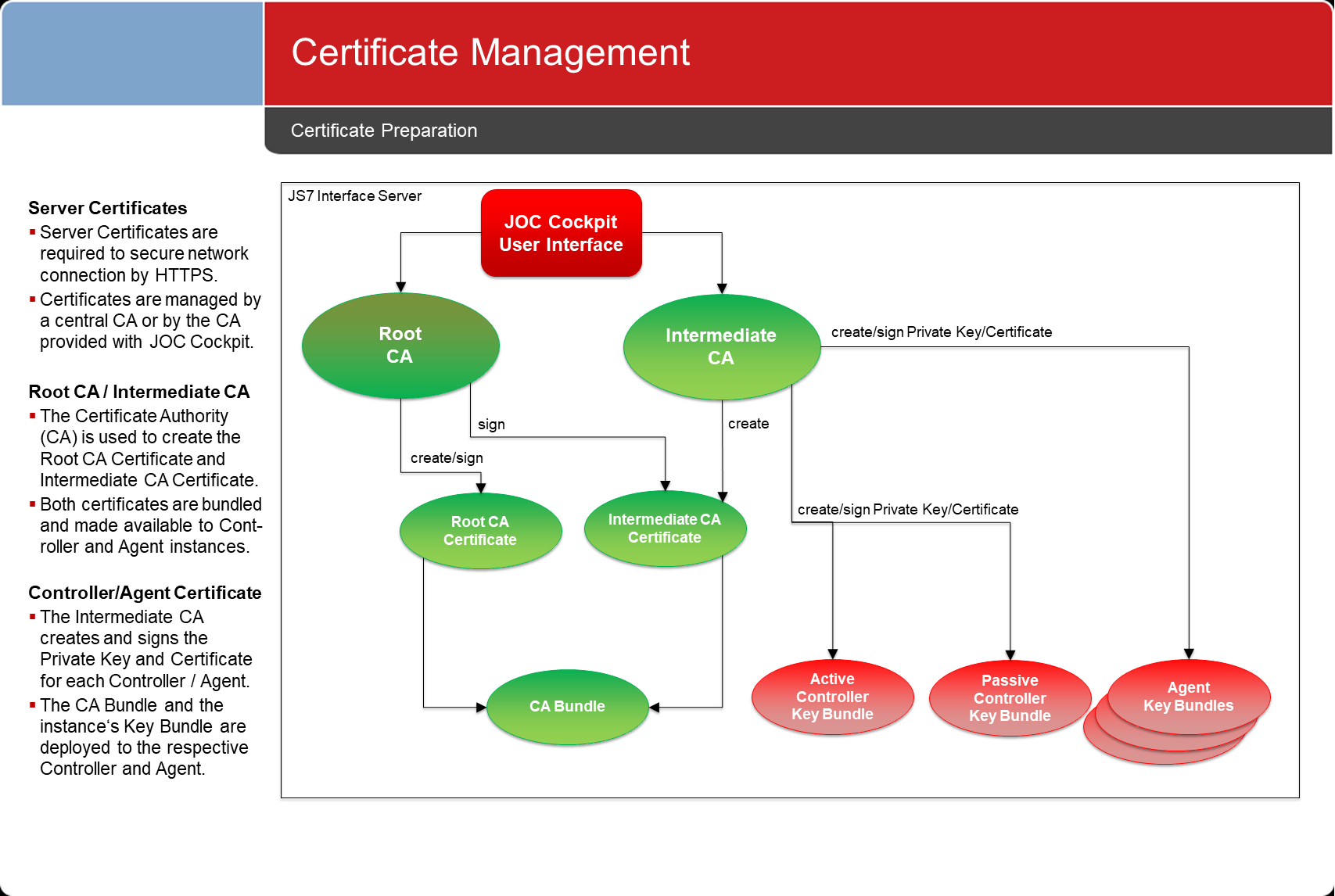
Certificate Preparation
- Certificates are created
- either from a CA independently from JS7
- This applies to users of JS7 who require high security levels and therefore operate a CA on their own.
- or directly from the JS7 JOC Cockpit
- This applies to users of JS7 who prefer a modest security level without the effort of maintaining a CA.
- The JOC Cockpit implements
- a Root CA and Intermediate CA to create certificates for JS7 components.
- deployment capabilities to prepare the security configuration for JS7 components, i.e. to generate keystores and truststores that are added the respective certificates.
- either from a CA independently from JS7
- Certificates can be maintained with JOC Cockpit should no individual CA be in place.
- Private Keys and Certificates are stored with the JS7 database.
- A user interface is available for any operations on certificates, such as creating, updating and deleting certificates.
- Certificates are prepared for deployment:
- For each JS7 component such as Masters and Agents a keystore and truststore is created that holds the required certificates.
- Keystores and truststores can be forwarded to Masters and Agents by any suitable means, e.g. file transfer, SSH, transportable disks etc.
- Keystores and truststores can be imported to Masters and Agents by use of a shell script.
Certificate Revocation
- Certificates are revoked by deploying updated certificates.
- Support for Certificate Revocation Lists (CRL) can be added at a later point in time if such demand occurs.
- The Java architecture and certificate types allow implementation of a CRL.
...
Overview
Content Tools