Page History
...
- The Security Architecture includes:
- Secure Communication:
- Certificate Management: Create and deploy certificates for secure network communication between products.
- Life Cycle Management: Create, update and delete certificates and deploy changes to products.
- Secure Configuration:
- Configurations include workflows, jobs and related objects.
- These objects are digitally signed and deployed by a responsible person.
- Secure Operation:
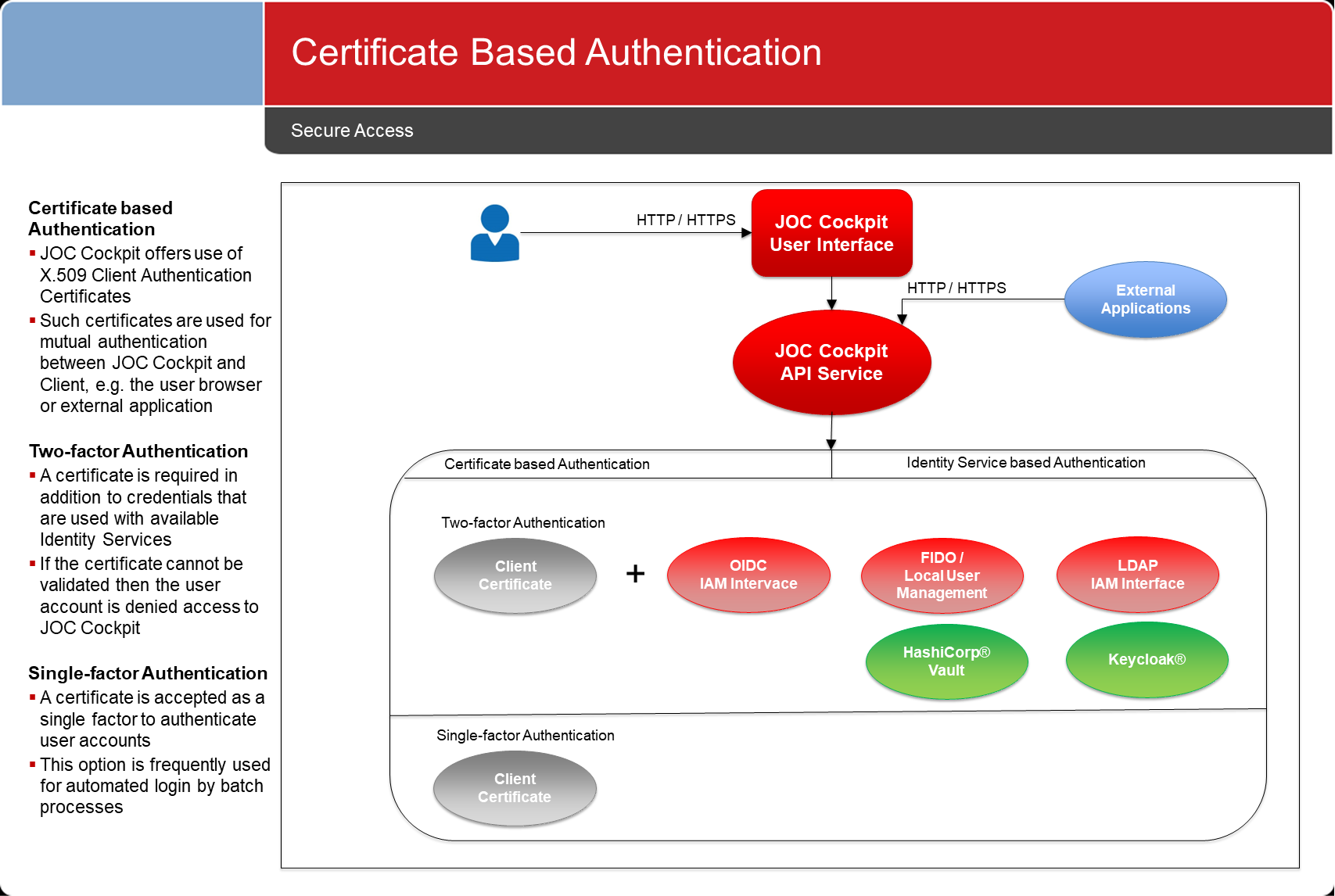
- Access Management: Authentication and Authorization via a LDAP, OIDC, FIDO2 Certificates, FIDO etc.
- Credential Management: Use of a Credential Store for confidential data.
- Secure Communication:
- Wording
- The term Deployment applies to a situation when a configuration is transferred from the JOC Cockpit to a Controller and Agents.
- The term Roll-out applies to a situation when a configuration is transferred between environments, for example from non-production to production environments. Within the respective target environment a Deployment is performed to transfer configuration objects to Controllers and Agents.
...
- Access Management includes access to JOC Cockpit and to the REST Web Service API. This applies to both users who access the JOC Cockpit GUI and & scripts, and applications that directly access the REST Web Service API.
- The Controller is not accessed by users directly but exclusively via the JOC Cockpit REST Web Service API. No default authentication is provided if the insecure HTTP protocol is used.
- Agents are not accessed by users directly but exclusively by a Controller. No default authentication is provided if the insecure HTTP protocol is used.
...
- Identity Services with built-in support for local user management, LDAP, OIDC, Certificates, FIDO2FIDO.
- Identity Services for use with external Identity Providers such as Keycloak®, HashiCorp® Vault
...
- Permissions for operations in the GUI and in the JS7 REST Web Service API can freely be grouped to roles.
- Users are assigned roles.
...
Certificates can be used as a single factor for authentication or as a second factor (MFA):. For details see JS7 - Certificate Identity Service.
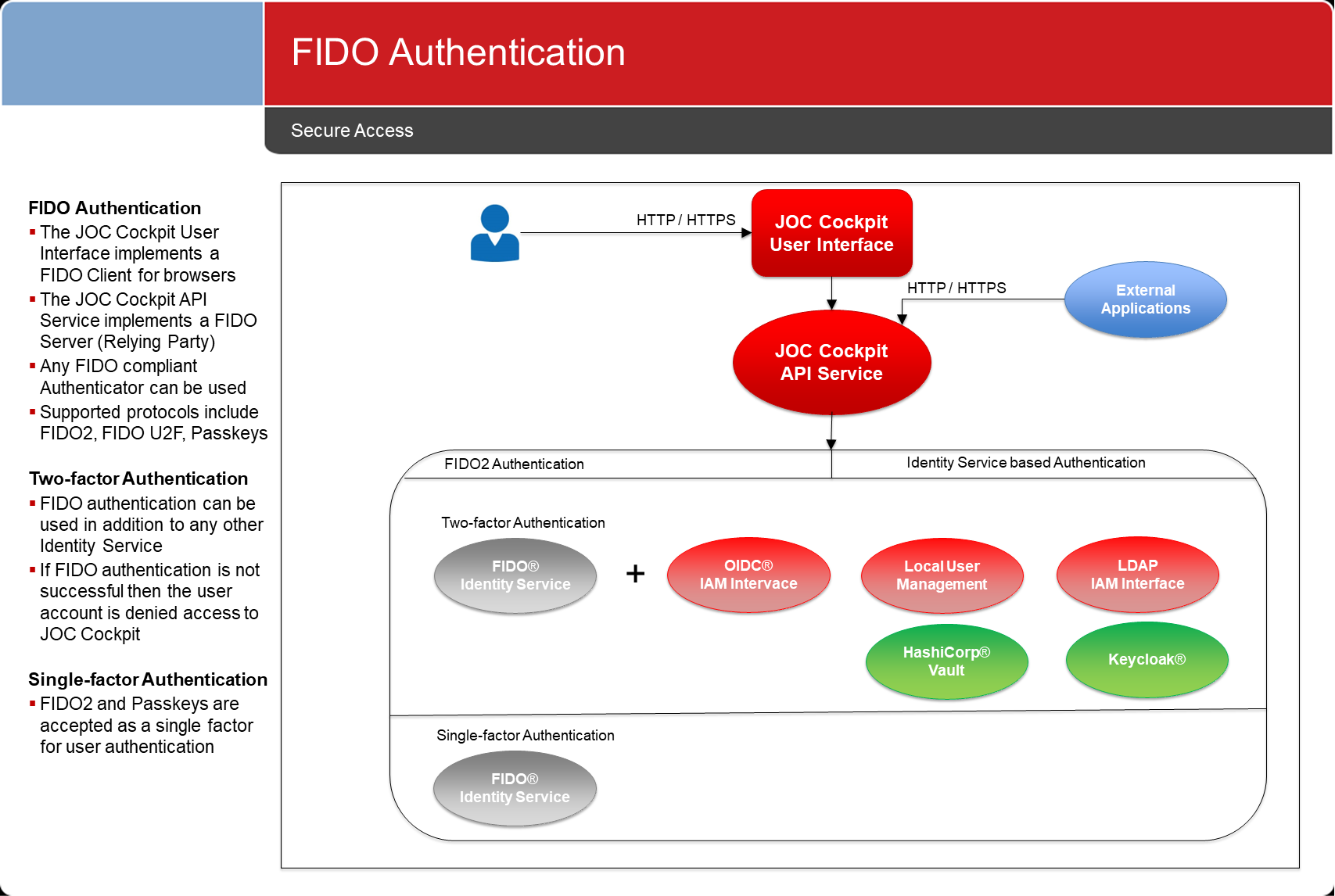
FIDO Authentication
The FIDO family of protocols offers FIDO2 and Passkeys as a single factor and as second factor in MFA. The FIDO U2F protocol can be used as a second factor.
For details see JS7 - FIDO Identity Service.
Credential Management
- Users frequently ask if JobScheduler can encrypt credentials. The answer is "no" as it makes no sense to handle a symmetric key that is stored in the JS7 configuration. Encrypting credentials contributes to obfuscation, not to security.
- There is only one way to handle passwords: not to use them.
- Alternatives include use of a JS7 - Credential Store.
...
Overview
Content Tools