Page History
...
- Identity Services implement Authentication Methods and access to Identity Providers, for . For example, credentials such as user account/password are used as an Authentication Method to access an LDAP Directory Service acting as the Identity Provider, see . See JS7 - Identity and Access Management.
- JOC Cockpit implements a flexible architecture that allows to add external Identity Service products to be added with future JS7 releases.
- By default JS7 ships with two the following built-in Identity Services:
includes to manageDisplay feature availability StartingFromRelease 2.2.0 - which includes management of user accounts with the JOC Cockpit and
- uses the JS7 database for persistence.
- The JS7 - LDAP Identity Service includes
- authentication of users with an LDAP Directory Service.
Display feature availability StartingFromRelease 2.5.0 - The JS7 - OIDC Identity Service
Jira server SOS JIRA columnIds issuekey,summary,issuetype,created,updated,duedate,assignee,reporter,priority,status,resolution columns key,summary,type,created,updated,due,assignee,reporter,priority,status,resolution serverId 6dc67751-9d67-34cd-985b-194a8cdc9602 key JOC-1370
- The JS7 - OIDC Identity Service
Display feature availability StartingFromRelease 2.6.0 - The JS7 - Certificate Identity Service
Jira server SOS JIRA columnIds issuekey,summary,issuetype,created,updated,duedate,assignee,reporter,priority,status,resolution columns key,summary,type,created,updated,due,assignee,reporter,priority,status,resolution serverId 6dc67751-9d67-34cd-985b-194a8cdc9602 key JOC-1547 - The JS7 - FIDO Identity Service
Jira server SOS JIRA columnIds issuekey,summary,issuetype,created,updated,duedate,assignee,reporter,priority,status,resolution columns key,summary,type,created,updated,due,assignee,reporter,priority,status,resolution serverId 6dc67751-9d67-34cd-985b-194a8cdc9602 key JOC-1546
- The JS7 - Certificate Identity Service
- For compatibility reasons, early releases of JS7 include the JS7 - Shiro Identity Service (deprecated), see
Jira server SOS JIRA columns key,summary,type,created,updated,due,assignee,reporter,priority,status,resolution serverId 6dc67751-9d67-34cd-985b-194a8cdc9602 key JOC-1145
3Display feature availability EndingWithRelease 2. 4.0
Matrix of Identity Services
Identity Services can be used in a number of flavors depending on the fact :
- which application manages user accounts/passwords:
- the Identity Provider that is specific to an Identity Service,
- JOC Cockpit that propagates user accounts/passwords to the Identity Service but does not store such credentials with the JS7 database.
- where assignments of roles to user accounts are stored:
- with the Identity Provider of the Identity Service,
- with the the JS7 database- Database.
| Identity Service | Identity Service Configuration Items | JOC Cockpit Configuration | |||||||
|---|---|---|---|---|---|---|---|---|---|
| Service Type | Built-in | User Accounts/Passwords stored with | User Accounts/Passwords managed by | Roles/Permissions stored with | Roles->User Accounts Mapping managed with | Roles Mapping | |||
| JOC | yes | JS7 Database | JOC Cockpit | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit | |||
| LDAP | yes | LDAP Server | LDAP Server | JS7 Database | LDAP Server | Mapping of LDAP Security Groups to JOC Cockpit Roles performed with the LDAP Server | |||
| LDAP-JOC | yes | LDAP Server | LDAP Server | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit | |||
| OIDC | yes | OIDC Identity Provider | OIDC Identity Provider | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit | |||
| CERTIFICATE | yes | CA / User Private Key | CA / User | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit | |||
| FIDO | yes | Authenticator | Authenticator | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit | |||
| VAULT | no | Vault Server | Vault Server | JS7 Database | Vault Server | Mapping of Vault Policies to JOC Cockpit Roles | |||
| VAULT-JOC | no | Vault Server | Vault Server | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit | |||
| VAULT-JOC-ACTIVE | no | Vault Server | Vault Server / JOC Cockpit | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit | |||
| KEYCLOAK | no | Keycloak Server | Keycloak Server | JS7 Database | Keycloak Server | Mapping of Keycloak Policies to JOC Cockpit Roles | |||
| KEYCLOAK-JOC | no | Keycloak Server | Keycloak Server | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit | KEYCLOAK-JOC-ACTIVE | no | Keycloak Server | Keycloak Server /
| SHIRO | yes | JS7 Database / shiro.ini | JOC Cockpit | JS7 Database / shiro.ini | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit | |||
| Shiro (deprecated) | yes | shiro.ini | JOC Cockpit | shiro.ini | shiro.ini | n/a | |||
The SHIRO Identity Service Type is:
| |||||||||
Management of Identity Services
The operation to manage Management of Identity Services is available from the user menu of an administrative user account accessed from the administration menu icon that is available for administrative user accounts in the right hand upper corner of any JOC Cockpit page:
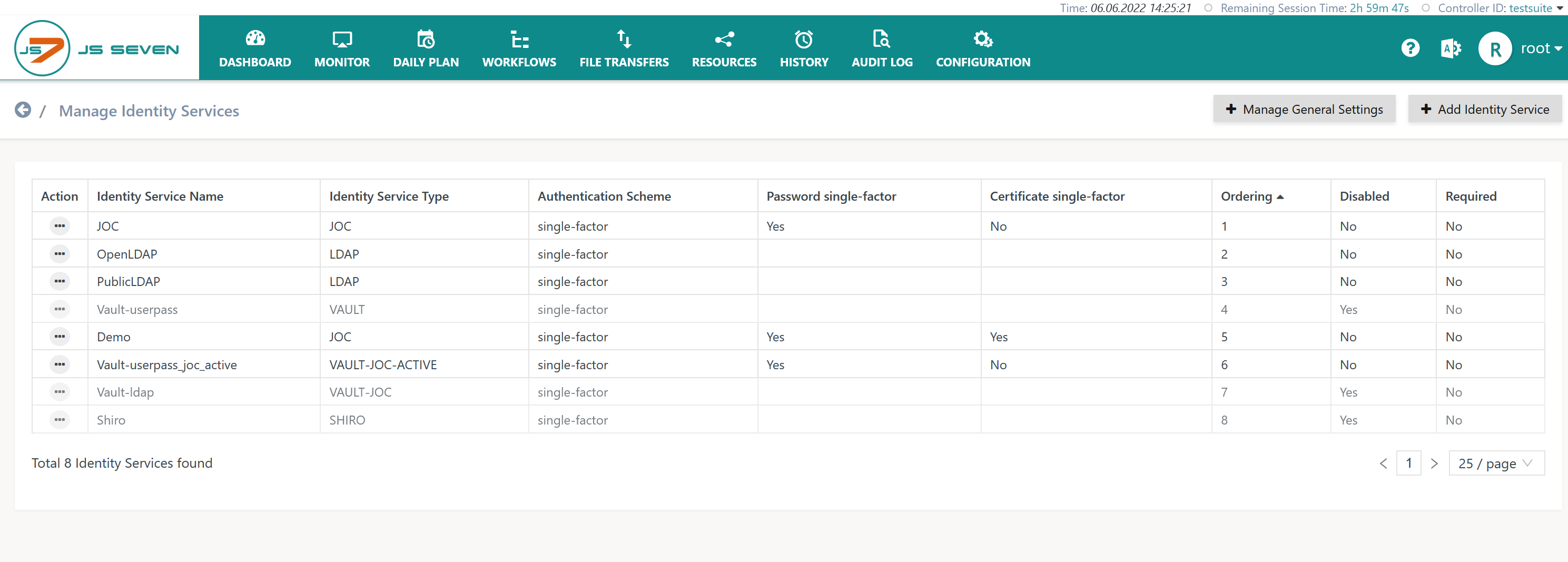
This operation brings forward the list of available Identity Services.
- By default a number of built-in Identity Services are available:
- In addition, connectors are available for external Identity Service products:
- The following Identity Services are considered to be deprecated and removed from current JS7 releases:
- The JS7 - Shiro Identity Service (deprecated)
Display feature availability EndingWithRelease 2.4.0
- The JS7 - Shiro Identity Service (deprecated)
...
By default users will find the JOC-INITIAL Identity Service which is added during initial installation.
- This Identity Service holds the single user account
rootwith passwordroot. - Users should modify the root user account's password.
- Users can modify the existing Identity Service or add new Identity Services.
Addition of an Identity Service
To add an Identity Service use the button Add Identity Service button from the above list of Identity Services shown above:
The remaining input fields for the popup window look like this:
...
- The
Identity Service Namecan be freely chosen. - The
Identity Service Typecan be selected as available from the matrix shown above matrix. - The
Orderingspecifies the sequence in which a login is performed with the available Identity Services. - The
Requiredattribute specifies if login with the respective an Identity Service is required to be successful, for example, if a number of Identity Services are triggered on login of with a user account. - The
Identity Service Authentication Schemeallows to selectselection of:single-factorauthentication : - a single factor is sufficient for login with the Identity Service that . This can be configured to make use of:- an optional user account and password
- an optional Client Authentication Certificate, see JS7 - Certificate based Authentication
two-factorauthentication: authentication - two factors are required for login with the Identity Service using:- a user account and password and
- a Client Authentication Certificate or FIDO Authentication Credentials.
Manage User Accounts and Roles
...
Settings are available at a global level and per individual Identity Service levels.
Anchor global_settings global_settings
Global Settings
| global_settings | |
| global_settings |
Global settings are applied to all Identity Services.
Explanation:
Session Idle Timeout(Default: 900 seconds 15 minutes)- If users are inactive for the given number of seconds then the user session expires and is terminated. Users can specify credentials and login to create a new user session.
- Should the lifetime of an access token provided by an external Identity Service be different from the maximum idle-timeout, then the JOC Cockpit will try to renew the access token with the Identity Service. Renewal of an access token does not require the user to repeatedly re-specify their login credentials for login.
- Identity Services can restrict the lifetime of access tokens (time to live) and they can limit renewal of access tokens (maximum time to live). If an access token cannot be renewed then the user session is terminated and the user is required to perform a login.
Initial Password(Default: initial)- If an administrator adds user accounts with the JOC Cockpit and does not specify a password then the
Initial Passwordwill be used. As a general rule the JOC Cockpit does not allow to the use of empty passwords but populates them from with theInitial Passwordif no a password is not specified by the user that adds or modifies an adding or modifying the account. - In addition, the operation to reset a user account's password is available that . This replaces an existing password with the
Initial Password. - If the
Initial Passwordis assigned, then a flag is set with for the user account to change indicate that the password has to be changed with the next login. This behavior ensures that users cannot use theInitial Passwordexcept for an initial login.
- If an administrator adds user accounts with the JOC Cockpit and does not specify a password then the
Minimum Password Length(Default 0)- For any passwords specified - including the
Initial Password- a minimum length is specifiedindicated. - Consider Note that the number of characters and arbitrariness of character selection are key factors for secure passwords. Password complexity requiring e.g. digits and special characters to be used do not substantially add to password security except in case of short passwords.
- For any passwords specified - including the
Settings specific
...
to Individual Identity Services
Such settings Settings are explained with the individual for each Identity Service individually:
- JS7 - JOC Identity Service (does not require any no settings required)
- JS7 - LDAP Identity Service
- JS7 - OIDC Identity Service
- JS7 - Certificate Identity Service
- JS7 - FIDO Identity Service
- JS7 - HashiCorp® Vault Identity Service.
- JS7 - Keycloak Identity Service
- JS7 - Shiro Identity Service (deprecated) (does not require any settingsno settings required)
Processing of Identity Services
A number of Identity Services can be processed for with the login of a user:
- Required Identity Services: user login is performed with all required Identity Services.
- No Optional optional Identity Services are considered.
- If more than one Required required Identity Service is configured then a user cannot log in if the login fails with any of the Required required Identity Services.
- Permissions are applied from roles assigned by the all Identity Services that is the last one in the sequence of enabled Identity Services which are required to authenticate a user account.
- Optional Identity Services: with the first successful login to an Identity Service the user is considered being to have logged in.
- No further optional Identity Services are consulted if a user login is successful with one of the Optional optional Identity Services.
- For example, if two Optional optional Identity Services
JOCandLDAPare configured in this sequence then the login to theJOCIdentity Service can fail and still the user might successfully login with theLDAPIdentity Service. - Permissions from the successful login to an Optional optional Identity Service are used.
- Disabled Identity Services are not considered for user login.
Identity Services are ordered to specify the sequence of preferred use for authentication.
Consider Note that a number of Identity Providers, for example LDAP being used for Active Directory access, might not accept repeatedly failed login attempts and might block the respective user account.relevant user account.
Multi-factor Authentication
Identity Services can be used with Multi-factor Authentication (MFA). This includes to use two separate factors for authentication that are located in different media:
- User/password credentials are what a user remembers and manually types in the JOC Cockpit GUI.
- Certificates are located on the machine from which the user operates the browser to access the JOC Cockpit GUI.
- FIDO can be used for a variety of authentication methods, including use of roaming authenticators, for example a USB stick, and platform authenticators, for example from the OS or from a smart phone.
Find the following matrix of Identity Services for use as a first factor and a second factor:
| First Factory | Second Factor | |
|---|---|---|
| JOC | CERTIFICATE | FIDO |
| CERTIFICATE | FIDO | |
| FIDO | CERTIFICATE | |
| LDAP | CERTIFICATE | FIDO |
| LDAP-JOC | CERTIFICATE | FIDO |
| OIDC | CERTIFICATE | FIDO |
| OIDC-JOC | CERTIFICATE | FIDO |
| KEYCLOAK | CERTIFICATE | FIDO |
| KEYCLOAK-JOC | CERTIFICATE | FIDO |
Single Sign-On
The JS7 - OIDC Identity Service allows single sign-on for the underlying Identity Provider:
- Users who have been previously authenticated with the same Identity Provider as used by the OIDC Identity Service can access JOC Cockpit from their browser without specifying credentials.
- Users who initially authenticate with an Identity Provider by use of JOC Cockpit can open additional tabs in their browser without specifying credentials.
Further Resources
| Display children header |
|---|
| Display content by label | ||||
|---|---|---|---|---|
|