Page History
...
- The JS7 - Identity Services offer integration with HashiCorpKeycloak® Vault authentication server.
- The Vault Keycloak Identity Service integration is available from JOC Cockpit:
- This requires HashiCorpKeycloak® Vault to be downloaded, installed and operated by the user. Vault Keycloak is not a built-in Identity Service and does not ship with JS7.
- JS7 implements a REST client for use with HashiCorp® Vault 1.7Keycloak® 16.0 and newer.
Identity Service Types
...
| Identity Service | Identity Service Configuration Items | JOC Cockpit Configuration | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Service Type | Built-in | User Accounts/Passwords stored with | User Accounts/Passwords managed by | Roles/Permissions stored with | Roles->User Accounts Mapping managed with | Roles Mapping | |||||||
VAULTKEYCLOAK | no | Vault Keycloak ServerVault | Keycloak Server | JS7 Database | Vault Keycloak Server | Mapping of Vault Policies Keycloak Roles to JOC Cockpit Roles | |||||||
VAULTKEYCLOAK-JOC | no | Vault Keycloak ServerVault | Keycloak Server | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit | VAULT-JOC-ACTIVE | no | Vault Server | Vault Server /JOC Cockpit | JS7 Database | JOC Cockpit | Mapping of user accounts and roles with JOC Cockpit |
Explanation:
- Service Type:
VAULTKEYCLOAK- Management of user accounts and passwords is performed by the Vault Keycloak Server.
- In addition, an automated mapping of policies roles - assigned a user account in Vault Keycloak - to JOC Cockpit roles takes place.
- The JOC Cockpit does not know any user accounts, passwords and role assignments as this information is managed with Vault Keycloak only.
- Service Type:
VAULTKEYCLOAK-JOC- Management of user accounts and passwords is performed by the Vault Keycloak Server.
- The assignment of roles to user accounts is performed with The the JOC Cockpit and is stored with the JS7 database.
- The JOC Cockpit knows user accounts and role assignments. The JOC Cockpit does not know passwords as this information is managed with Vault only
- Service Type:
VAULT-JOC-ACTIVE- Management of user accounts and passwords is performed by the JOC Cockpit. The JOC Cockpit forwards user accounts and passwords to the Vault Server. The JOC Cockpit stores users accounts (not: passwords) in the JS7 database.
- The assignment of roles to user accounts is performed with The JOC Cockpit and is stored with the JS7 database.
- The JOC Cockpit knows user accounts and role assignments. The JOC Cockpit temporarily knows passwords until this information is forwarded to Vault.
...
- Keycloak only
Keycloak Authentication Methods
JS7 supports the following authentication methods with Vault:
- Username & Password
- LDAP
- It is not required to use Vault Keycloak to connect to an LDAP Directory Service as there is a built-in in JS7 - LDAP Identity Service for this purpose.
- This authentication method can be used with the
VAULTKEYCLOAKIdentity Service Type only.
JS7 does not support cloud based authentication methods with Vault as such methods are typically used for engineering and administrative roles with cloud services that are not related to an application such as JS7.
...
Keycloak.
Keycloak Server Configuration
| Anchor | ||||
|---|---|---|---|---|
|
If the VAULT-JOC-ACTIVE Identity Service Type is used then an Application Role has to be created and an access token has to be generated with Vault that is added to the JOC Cockpit configuration of the Vault Identity Service.
| Status | ||||
|---|---|---|---|---|
|
| Anchor | ||||
|---|---|---|---|---|
|
...
Account & Password
- The authentication method has to be added to Vault.
- The path of the authentication method has to be added to the Identity Service configuration in the JOC Cockpit.
- If the
KEYCLOAKIf theVAULTIdentity Service Type is used then:- user accounts are managed exclusively by VaultKeycloak,
- policies roles have to be set up in Vault Keycloak with names that exactly match the names of roles in the JOC Cockpit.
- a user account will be assigned the roles matching policy names when performing a login to the JOC Cockpit.
- it is not required to add specific permissions to policies roles with VaultKeycloak.
- If the
VAULTKEYCLOAK-JOCIdentity Service Type is used then:- user accounts are managed by VaultKeycloak.
- user accounts are added to the JOC Cockpit to allow assignment of roles:
- user accounts in Vault Keycloak and in the JOC Cockpit have to match as otherwise the user account is not assigned a role.
- no passwords are managed by the JOC Cockpit.
VAULT-JOC-ACTIVEIdentity Service Type is used then:- user accounts
- are managed by
- the JOC Cockpit.
LDAP
- It is not necessary to use Vault to connect to an LDAP Directory Service as there is the built-in JS7 - LDAP Identity Service for this purpose.
- The authentication method has to be added to Vault.
- The path of the Authentication Method has to be added to the Identity Service configuration in JOC Cockpit.
- The
VAULTKEYCLOAKIdentity Service Type has to be used, meaning that:- user accounts are managed with VaultKeycloak.
- user accounts are added to the JOC Cockpit to allow assignment of roles:
- user accounts in Vault Keycloak and in the JOC Cockpit have to match as otherwise the user account is not assigned a role.
- no passwords are managed by the JOC Cockpit.
...
When a user logs in to the JOC Cockpit then user credentials are forwarded to the Vault Keycloak Server that authenticates the user and returns an access token.
- Vault access tokens are created with the following restrictions:
- time to live (TTL):
- the access token will expire after the given period,
- the Identity Service renews the access token 60s before expiration, this step is performed for an arbitrary number of renewals. This requires that the access token's TTL exceeds 60s and the Vault permission
selffor renewing a token by the token owner to be in place.
- maximum time to live:
- the access token's overall lifetime is limited, renewals cannot take place after the specified period.
- time to live (TTL):
- If an access token cannot be renewed by the Identity Service then the user session is terminated and the user is forced to login and to specify credentials.
- This happens in the event of the maximum TTL being exceeded or that the token has been revoked.
- Vault Keycloak administrators should check for reasonable values of the TTL, maybe not less than 300s, and the maximum TTL, maybe at least 15 minutes, as otherwise users would have to repeatedly login quite frequently.
- The JOC Cockpit handles the idle timeout of user sessions independently of VaultKeycloak, see JS7 - Identity Services.
- If the idle timeout is exceeded then the user session is terminated.
- The Identity Service tries to can revoke the access token . This requires the Vault permission
selfto revoke a token by the token owner.
- with the Keycloak server.
Identity Service Configuration
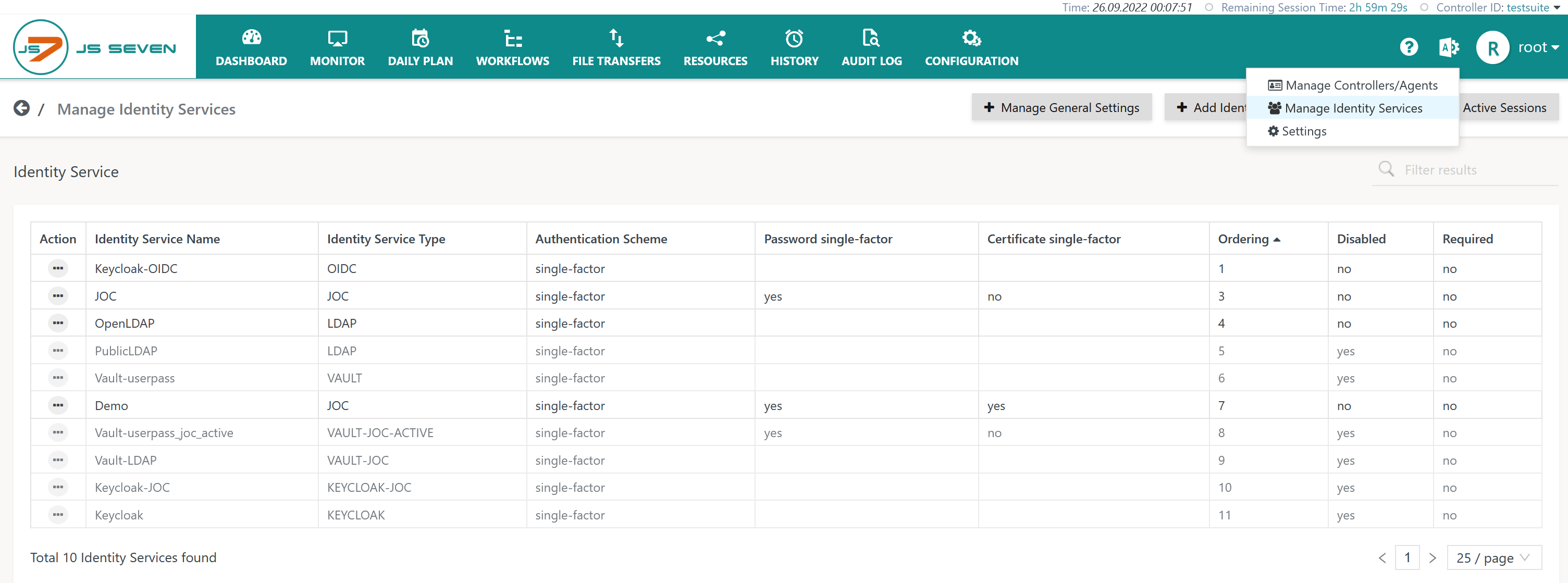
The JOC Cockpit Manage Identity Services page from the user menu of an administrative account is provided for the configuration of Identity Services:
Add Identity Service
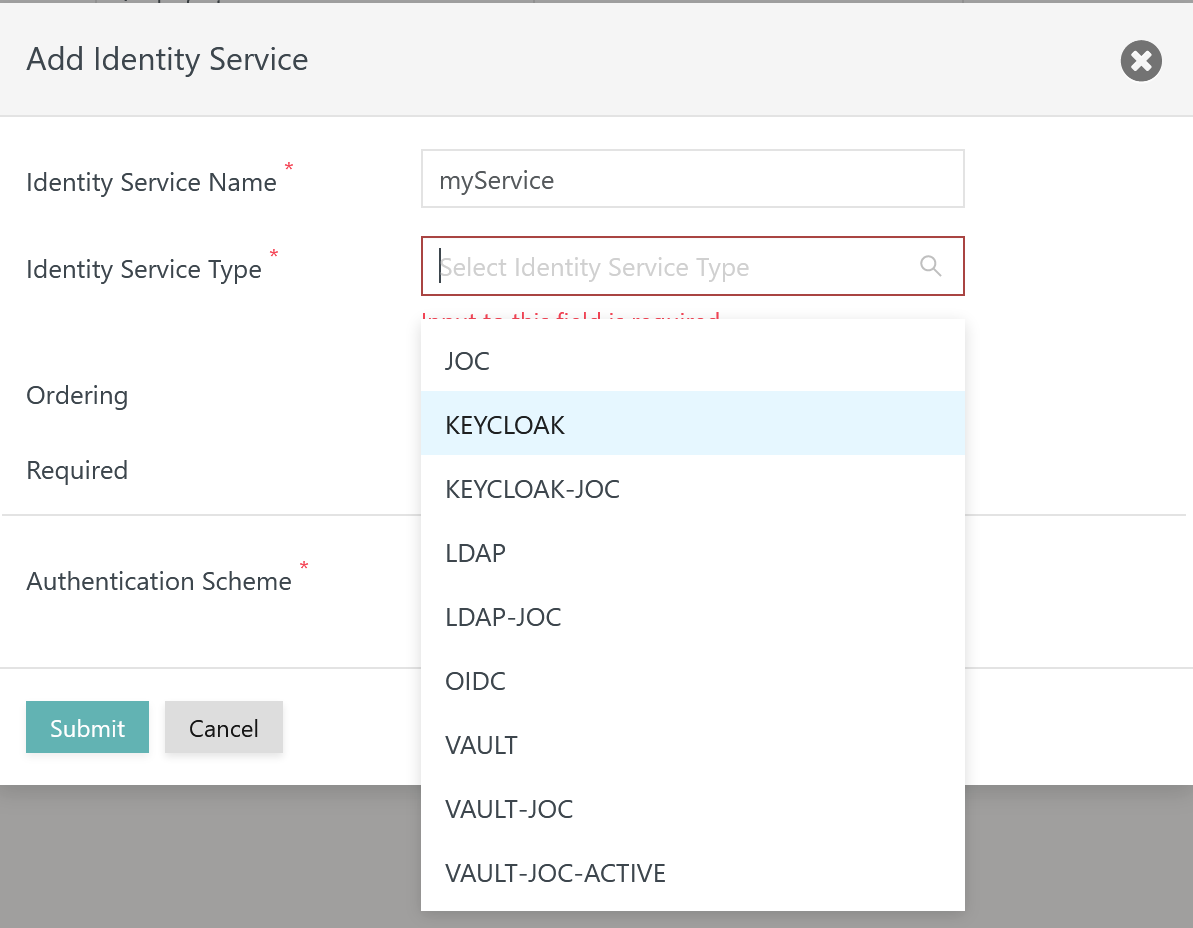
To add an Identity Service use the button Add Identity Service from the page shown above, listing the available Identity Services:
The remaining input fields for the popup window look like this:
Explanation:
...
Identity Service Settings
Having added a Vault Keycloak Identity Service it is necessary to add settings for the Vault Keycloak integration from the Identity Service's Manage Settings action menu item:
For use of the HashiCorp® Vault Identity Service:
- the Vault product has to be installed and has to be accessible for JOC Cockpit and
- the following settings have to be specified:
Explanation:
...