Page History
...
Each user with the permission to deploy has to add his X.509 signing certificate to JOC Cockpit.
Optional: Root CA Certificate
In addition, the X.509 certificate of the Root CA that signed the user's signing certificate can be added to JOC Cockpit. There is a single Root CA certificate for all user profiles.
- Any user signing certificates have to be published to the Controller and Agents. Certificates are stored to the
config/private/trusted-x509-keysfolder of Controller and Agent installations. - If a Root CA certificate is present in JOC Cockpit, then it is sufficient to add the Root CA certificate to the
config/private/trusted-x509-keysfolder of Controller and Agent installations.- No further user
signingcertificates have to be added to the Controller or Agents as long as the user signing certificates were created by the given Root CA. - This mechanism implies that any user signing certificate signed by the same Root CA certificate will be accepted.
- Users who do not wish to use this implicit mechanism should not add the Root CA certificate to Controller and Agents but should add individual user signing certificates only.
- No further user
...
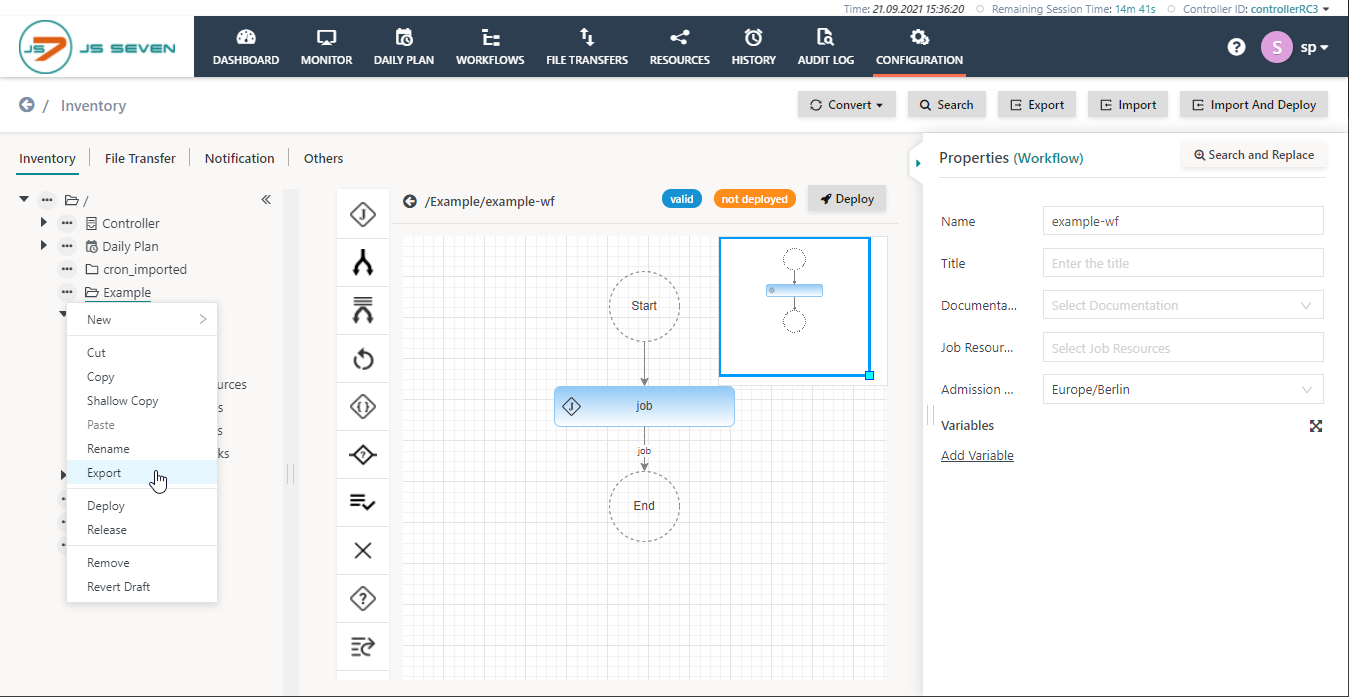
- Click Export either in the context menu of the folder to export or from the button in the top right corner:
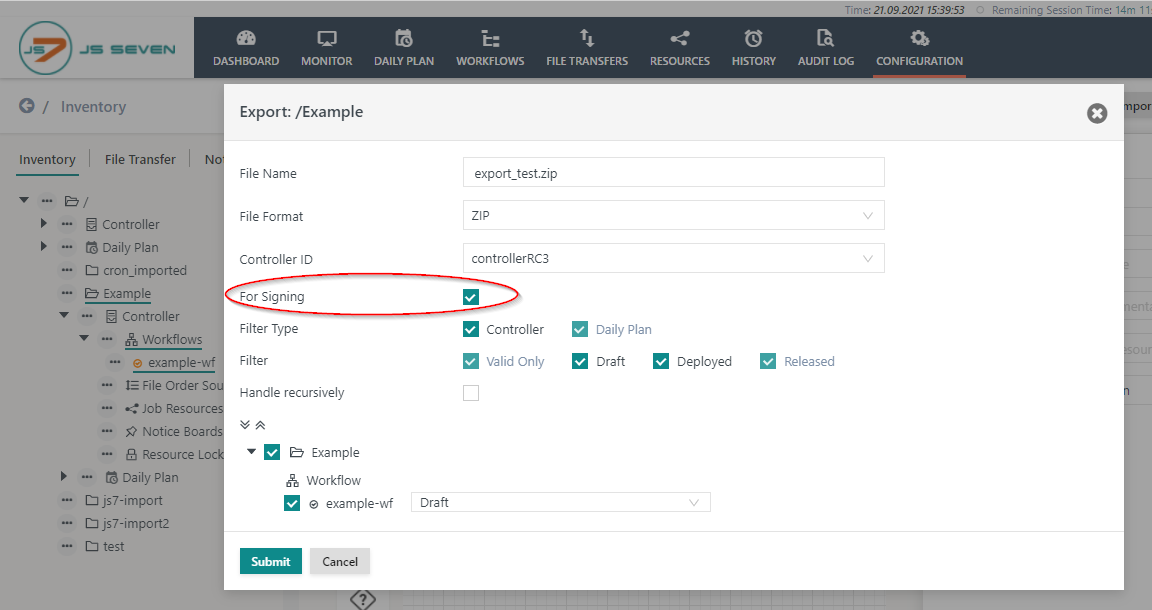
- In the Export popup pop-up window check the checkbox "for Signing":
- Select the scheduling objects to deploy.
...
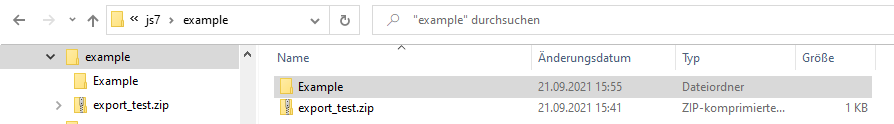
Extract the configuration from the archive and preserve the folder structure of included scheduling objects:
Sign Signing the configuration.
For this example, we use OpenSSL to sign the configuration file.:
| Code Block | ||
|---|---|---|
| ||
openssl dgst -sha256 -sign c:\tmp\sos.private-ec-key.pem -out c:\tmp\example-wf.workflow.json.sha256 c:\tmp\example-wf.workflow.json |
-sha256- the signer algorithm
-sign c:\tmp\sos.private-ec-key.pem- the private key file to sign the content of the original configuration file
-out c:\tmp\example-wf.workflow.json.sha256- the path to the output file
- the file contains the binary representation of the signature
c:\tmp\example-wf.workflow.json- the path to original scheduling object file (workflow)
- the path to original scheduling object file (workflow)
...
| OpenSSL | Java with RSA | Java with ECDSA |
|---|---|---|
| sha512 | SHA512withRSA | - |
| sha256 | SHA256withRSA | SHA256withECDSA |
During import, the scheduling object configuration and the signature from the archive will be forwarded to the Controller and will be validated. After successful validation by the Controller and by the Agent the scheduling object is deployed.
...