...
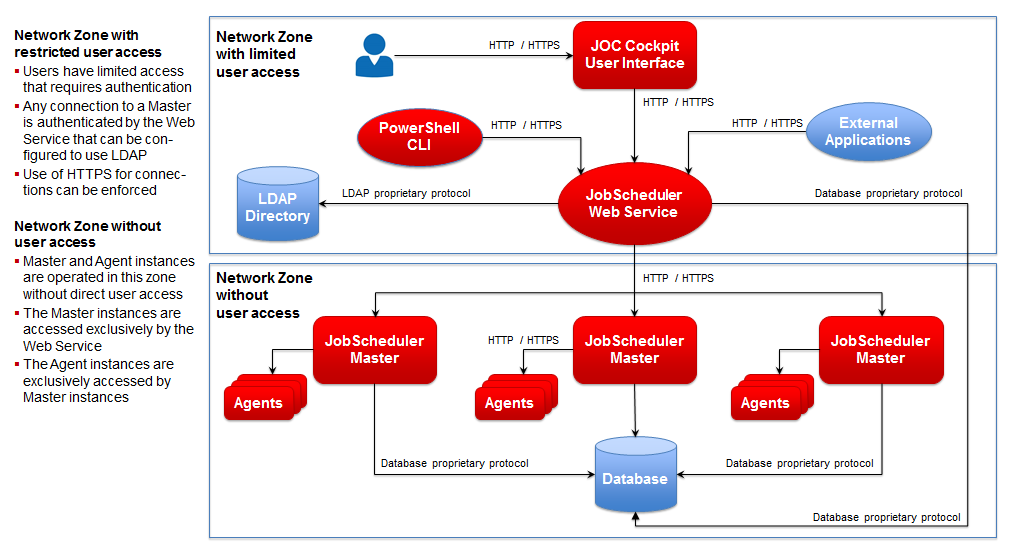
- Authentication and Authorization: The Web Services use an LDAP Directory for authentication, authorization is carried out against role-based group permissions data held on the WebServices server. This means that user access to particular resources can be restricted.
- Multiple GUI instances: The JobScheduler Web Services can be accessed by more than one JOC Cockpit, so that, for example, an operator situated in a remote site can carry routine tasks at the same time as an administrator in the server room is configuring maintenance procedures.
- 3rd Party Applications: External applications such as ERP systems can also access the Web Services and, for example, start jobs when they provide the correct authentication and authorization.
- Multi-Client Capability: Any number of JobScheduler Masters can be controlled via the Web Services as long as they are located in the same network.
- Job Status and History: JobScheduler Masters record operational information in a database - this information can be called up from the JOC Cockpit via the Web Services.
- Security: The architecture restricts direct user access to the JobScheduler Web ServiceJOC Cockpit. Only the Web Service has access to the JobSchedulers JobScheduler Masters themselves.
Technical Details
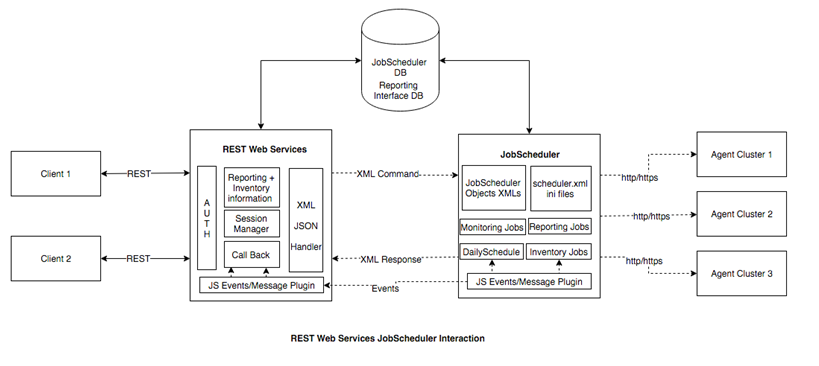
The diagram below shows the JobScheduler JOC Cockpit Architecture at a more technical level.
HTTP/HTTPS is used for communication between the RESTful Web Services and the JOC Cockpit - or other applications.
The Web Services use web service uses XML commands and responses to communicate with the JobScheduler Master(s). In addition events are communicated between the Web Services Service and the JobScheduler Masters.
...
Communication between the REST Web Services Service and the JobScheduler database takes place using Hibernate.
...
- authentication is carried out against a local configuration or an LDAP directory
- authorization is carried out against a role-based group permissions file.