...
- The user can only reach the Internet via a proxy server (in this example, Homer).
The Japan server can only be reached via a jump host on a server UK, which is installed in a so-called demilitarized zone (DMZ).
The jump host already has a JADE command line client Command Line Client installed to enable file transfer across the DMZ. - Direct connections between the user's computer (localhost) and the Internet and from the Homer proxy server to the Japan target server are blocked.
...
The jump fragment
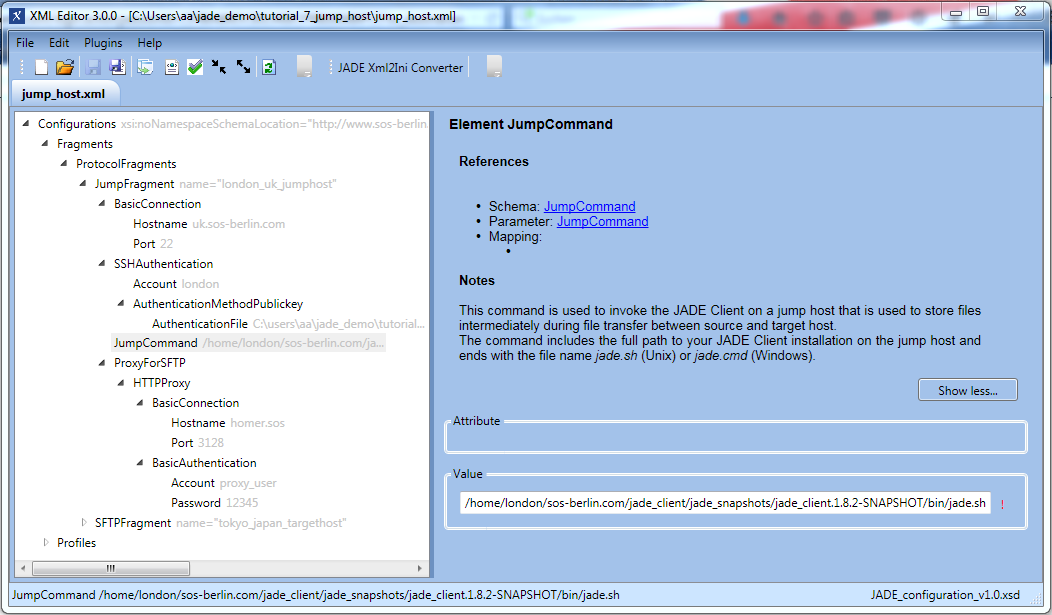
The first step is to configure the jump protocol fragment JumpFragment for the London server, as shown in the next screenshot.
This configuration fragment is identified by the name attribute of the JumpFragment parameter and as can be seen in the screenshot has three main components:a BasicConnection element,
an SSHAuthentication element and
the ProxyForSFTP element. Detailed descriptions of all these elements can be found in the relevant Parameter Reference sections, which are linked behind the parameter names.
Note that:
The JumpCommand parameter specifies the operation that is to be carried out by the JADE Client on the jump server.
The AuthenticationFile element specifies the path to the RSA key file on the user's local file system that is used to authenticate the user on the jump host.
The target fragment
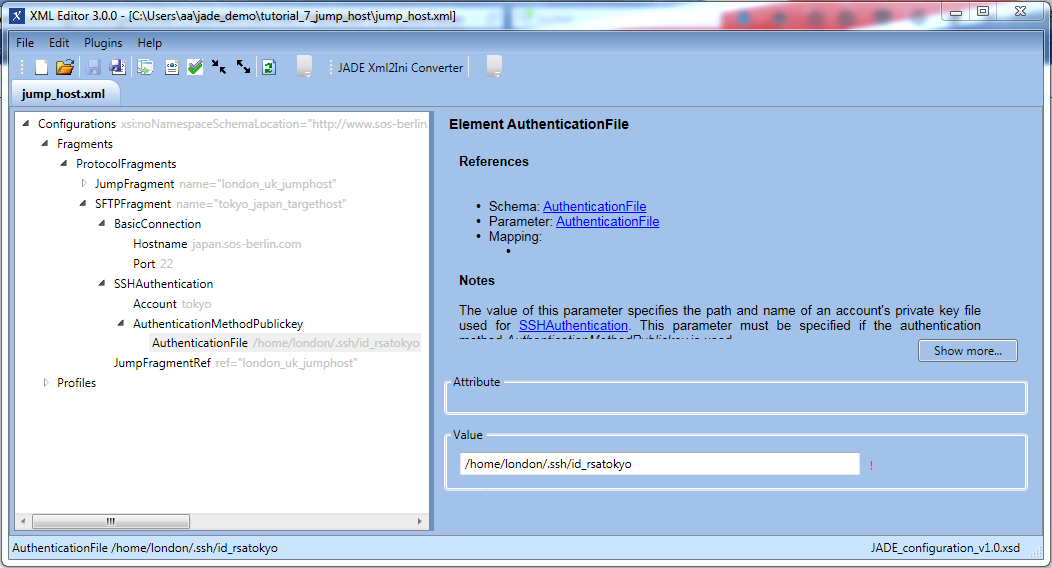
- The second step is to configure the target protocol fragment for the London server, as shown in the next screenshot.
- This element specifies the parameters required so that the JADE Client on the jump host can access the target server.
- As can be seen from the screenshot the fragment is protocol-specific and contains a JumpFragmentRef parameter which specifies the name of the JumpFragment element to be used to access the target server.
This means that it is only necessary to specify the target server and the jump host will be automatically added once the JumpFragment has been configured and referenced for the target.
- The second step is to configure the target protocol fragment for the London server, as shown in the next screenshot.
The transfer profiles
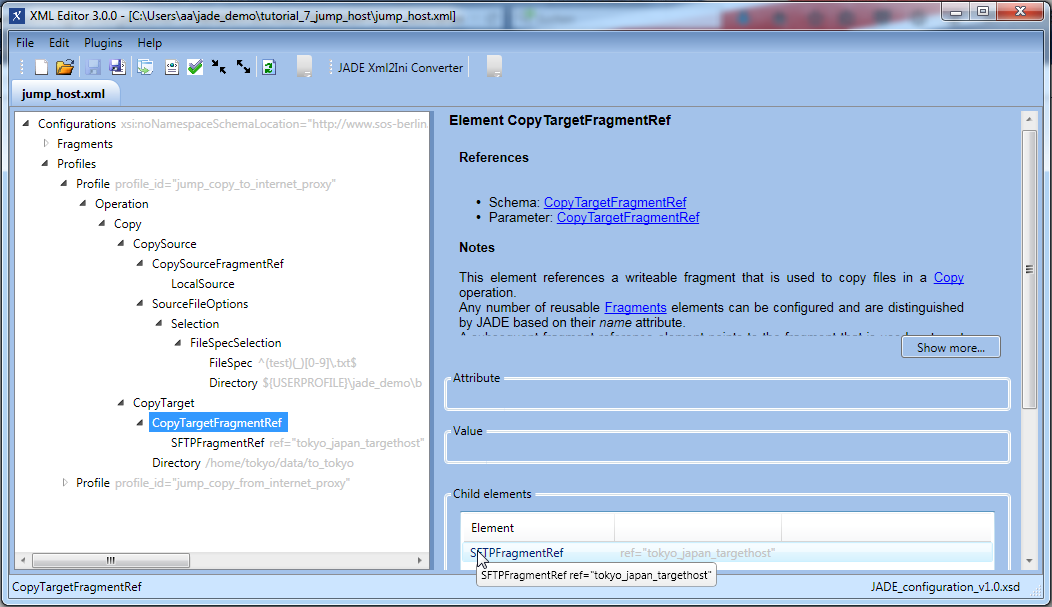
Transfer to the Internet
The next screenshot shows the transfer profile specifying the operation to be carried out (copy), the operation source (local) and target (the Japan server accessed using the Tokyo account via the UK jump server, specified using the SFTPFragmentRef parameter)Transfer from the Internet
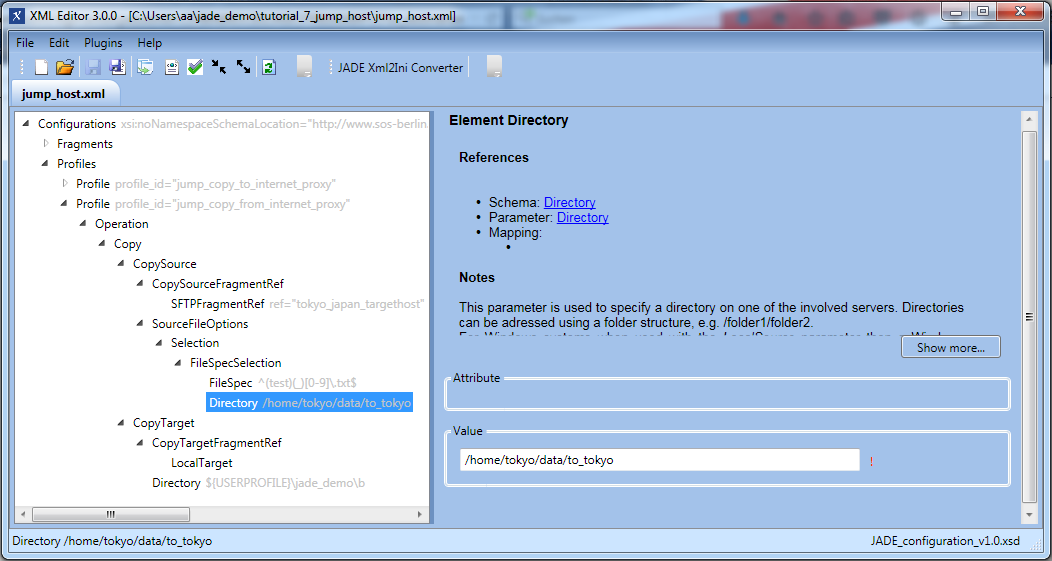
The next screenshot shows the profile configuration that would be required to carry out a similar transfer operation from the Japan server to the user's local file system via the jump host and proxy server.
This profile can be seen to be very similar to the jump_copy_to_internet profile shown above and illustrates how relatively simple configuration elements can be generated.
...
- The XML and ini configuration files used for the example shown in this tutorial can be downloaded using the following link:
- Note that in contrast to the other JADE tutorials we have not opened the servers used to make this tutorial for public use.
Users wishing to test out this configuration will have to first of all have to set up their own test serversenvironment.
Integration with the JADE Background Service
- The JADE Background Service is not able to directly access the JADE Client on the jump server. This means while the Background Service can access the transfer history and log files of the local JADE client Client, it is not able to access log or file transfer information from the JADE Client on the jump host.
However the originating JADE Client (i.e. the current example, the client on the source server) receives feedback from the client on the jump host containing information about whether transfer from the jump host to the target server was successful.
...