JADE Credential Store
See more information about Credential Store here Using Credential Store to securely store authentication, connection and other parameters
Set-up KeePassX DB as Credential Store
Download KeePassX and create kdb file
- JADE Credential Store (CS) supports KeePassX DB version 1.0
- One can download the KeePassX desktop utility from https://www.keepassx.org/downloads/
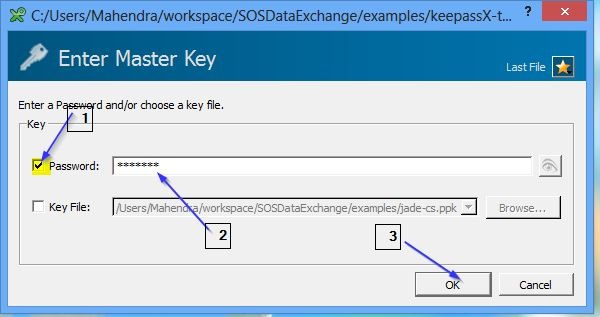
Set-up Credential Store with Password
Step 1: Setup KeePassX DB
- Open the KeePassX utility
- Choose password as Master Key
- Assign password to KeePass DB and click OK
JADE will use the Master Key, i.e. "password" specified during creation process as access password of KeePassX DB.
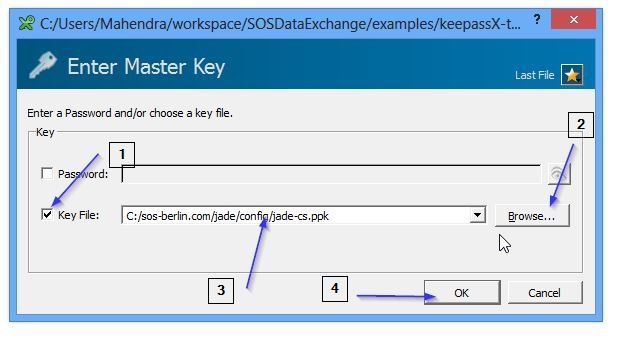
Set-up Credential Store with PPK key
- Start KeePassX utility
- Click on Key File as Master Key
- Browse for pre generated ssh key as Master Key
- Click Ok and KeePassX will open and will be ready to add new entries.
Create Credential Store entries
Create Credential Store entry for FTP server
KeePassX DB can organize entries in logical groups, under groups and sub-groups.
One can organize Credential Store in groups, e.g. Internal-Server, External-Server etc. User is free to choose his own organization scheme.
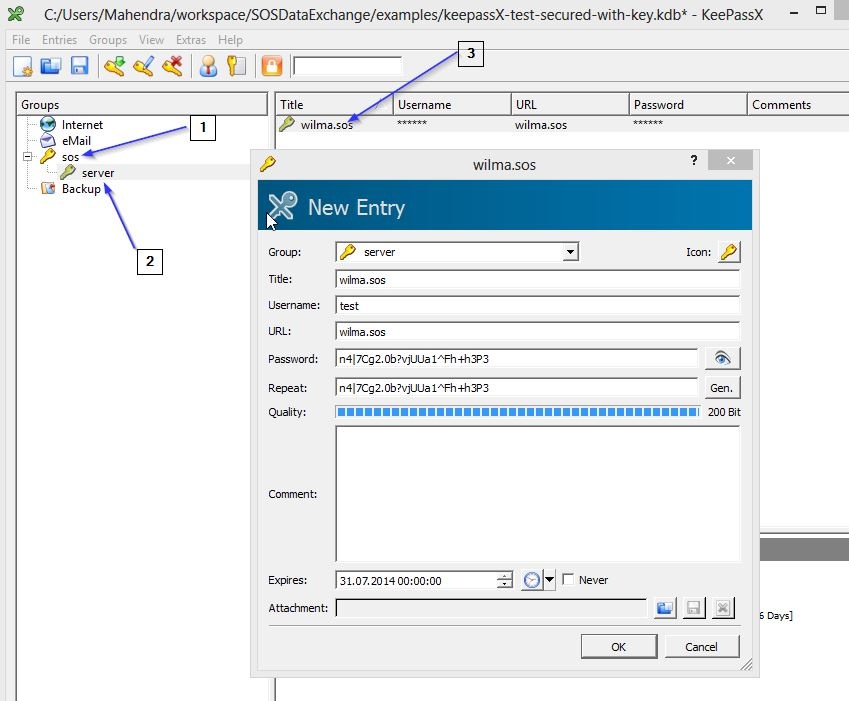
- Create new top group i.e. sos
- Create new sub group i.e. server
- Create new entry wilma.sos for settings
- Title : Will be used as key in the hierarchy to access the credentials.
- Username : Field is used to specify username i.e. FTP/SFTP user name
- Password : Password field is used to specify password, user can use the KeePassX's password generation feature to specify strong passwords or can provide already existing password.
- Comment : Can contain extra parameters for JADE along with credentials, all/any JADE parameter can be specified in Comment section.
- Expires : Expiry date is used to enforce Password/SSHkey expiration policy, user can define its own expiry period i.e. 90 days, or check option Never. JADE will raise an error if a KeePassX DB entry is not expired.
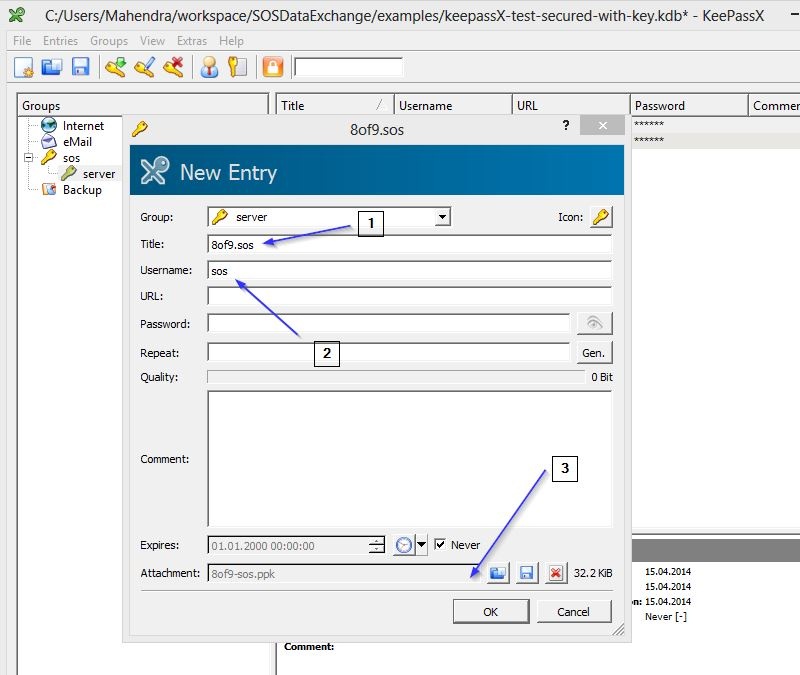
- Attachment : Can have private key file used for file transfer
Create Credential Store entry for SFTP server
JADE profiles with Credential Store
Set-up global Credential Store profile
Define an global profile having all the parameters concerning Credential Store. JADE can reuse any profile defined in same jade_settings.ini file.
It's recommended to create global fragments and reuse them in profiles.
Alternatively a user can define multiple KeePassX DB files, e.g. Test, Integration, Production and create corresponding profiles for the different environments.
Set-up global Credential Store profile with password
; Global Profile for KeePassX Database WithPassword [Keepass_DataBase_WithPassword] use_credential_Store = true CredentialStore_FileName = C:\sos-berlin.com\jade\credential-store\keepassX-test.kdb CredentialStoreAuthenticationMethod = password CredentialStore_password = *********
Set-up global Credential Store profile with public key
; Global Profile for KeePassX Database With Public Key [Keepass_DataBase_WithPublicKey] use_credential_Store = true CredentialStore_FileName = C:\sos-berlin.com\jade\credential-store\keepassX-test.kdb CredentialStoreAuthenticationMethod = privatekey CredentialStore_KeyFileName = C:\sos-berlin.com\jade\config\jade_cs_rsa.ppk
Set-up JADE profile for FTP
In this example we are referring/including Credential store settings from global KeePassX database profile Keepass_DataBase_WithPassword .
JADE then will open the KeePassX DB and refer the entry sos/server/wilma.sos, we have already defined this settings in the KeePassX DB:
source_CredentialStore_KeyPath: JADE will refer the entry from KeePassX DB.
source_include: include Credential Store settings.
[ReceiveUsingKeePass]
source_include = Keepass_DataBase_WithPassword
source_CredentialStore_KeyPath = sos/server/wilma.sos
source_dir = /tmp/test/jade/out
source_make_dirs = true
source_transfer_mode = ascii
target_protocol = local
target_dir = ${TEMP}/jade/in
operation = copy
file_spec = \.txt$
transfer_mode = ascii
Set-up JADE profile for SFTP
[ReceiveUsingKeePass]
source_CredentialStore_KeyPath = sos/server/8of9.sos
source_include = Keepass_DataBase_WithPassword
source_dir = /tmp/test/jade/out
source_make_Dirs = true
source_transfer_mode = ascii
target_protocol = local
target_dir = ${TEMP}/jade/in
operation = copy
file_spec = \.txt$
transfer_mode = ascii
An Example Server to Server Transfer Profile using Credential Transfer
A profile definition for Server to Server transfer, from a FTP to a SFTP server:
[transfer_server_2_server]
include = Keepass_DataBase_WithPassword
file_spec = ^.*\.txt$
operation = copy
source_CredentialStore_KeyPath = sos/server/wilma.sos
source_dir = /tmp/test/jade/out
target_CredentialStore_KeyPath = sos/server/8of9.sos
target_dir = ${TEMP}/jade/in
In this example all files with the file name extension .txt should be transferred from the server wilma via FTP to the server 8of9 by SFTP.
To start this with the command line client one must type:
jade.sh -settings=name_of_settings_file -profile=transfer_server_2_server
Profile fragments SFTP with Public Key :TBD
To make the profile more reusable and readable it is possible to reuse profiles snippets in the way like this:
Profile fragments SFTP with Public Key :TBD
To make the profile more reusable and readable it is possible to reuse profiles snippets in the way like this:
See also
- Using_CredentialStore_to_securely_store_authentication,_connection_and_other_parameters]
- For infos about the parameters see the parameter documentation on
jadeParameterReference.