Introduction
- The Credential Store (CS) allows sensitive data to be encrypted and stored securely and independently of the application(s) such as YADE and the JobScheduler YADE JITL Jobs that use this data. Access to the CS is only possible with access methods such as a key file and/or password.
- The CS requires the use of a
.kdbxdatabase and the installation of a kdbx-compatible user interface such as "KeePass 2" or "KeePass-X". - The advantage of using a CS is that the CS stores sensitive information such as credentials in a standardized, secure and fully encrypted database and sensitive authentication information is not exposed in use. Applications access the CS database by using password, encryption-key file or a combination of both.
- The CS can be used to securely store information of parameters, database connection URLs, private key files and other sensitive data.
Scope
This article describes the use of the Credential Store with the YADE Client.
A description of the use of the Credential Store with the YADE JITL job can be found in the Jobs JADEJob & JADE4DMZJob article.
Configuration Procedure
The examples presented in this article are based on the simple file transfer example described in the The YADE Client Command Line Interface - Tutorial 1 - Getting Started article. The tutorial describes the configuration required to download a number of files from a online server provided by the SOS GmbH and save these files on the user's local file system. Using this server means that users can get a working example up and running with a minimum of effort. A simplified version of the configuration used in the tutorial (only specifying FTP) is available as a download: sos-berlin_demo_2_local.xml. Instructions for installing and configuring the YADE Client can be found in the YADE - Tutorials article.
The configuration provided in the download file will cause six files in the root server folder to be copied to a local /jade_demo/transfer_receive folder, generating the target folder in the user's home or profile directory if required and permissions are available. The files will be transferred by FTP and authentication for the server (user name and password) is specified in the download file.
The example described in this article uses << UPDATE
Installing the Credential Store and configuring the database
KeePass 2 has been used in the current article to implement the Credential Store database. The installation of and use of KeePass is described on the KeePass Web Site.
Feature Availability
FEATURE AVAILABILITY STARTING FROM RELEASE 1.12.2
The Credential Store has to use a .kdbx database to be able to access all Credential Store features.
Secure, compliant and password-free use of the Credential Store requires the YADE Client in version 1.12.2 or newer.
Database Configuration
Credential Store databases are stored as a file on the file system.
For the examples described in the current article the following database was configured (on a Windows system):
- Path:
%USERPROFILE%\jade_demo\keepass\demo_cred_store.kdbx - Master Password:
sos
In addition a Master Key file (not used in the example below) can be generated using the Files/Change Master Key KeePass menu option and then selecting the Show expert options checkbox.
Adding an Entry to the Credential Store
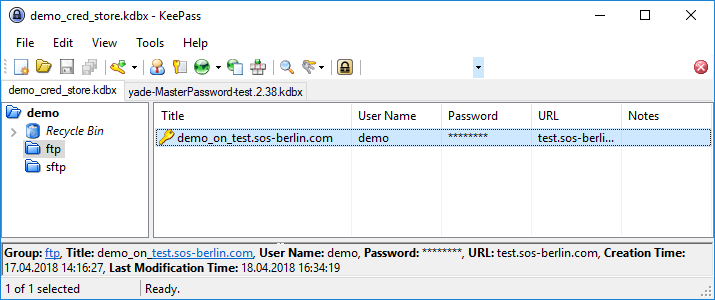
The following screenshot shows that two Groups have been configured for the current example, named "demo" and "ftp", along with the Entry "demo_on_test.sos-berlin.com". Entries are added using the Edit / Add Entry menu item.
The following information can be retrieved from standard KeePass CS fields:
- Title: The identifier CS database, this could be string e.g. host name/server name.
- User name: The user identification of a user who is authenticated for the operation.
- Password: Assigned password for a user account or passphrase for a private key.
- URL: The host name/server name or IP address of the server.
- Notes: This block can be used to specify additional parameters for the file transfer. The syntax ... < TO REWORK
- File Attachment & Custom Fields: Files such as PGP or SSH private keys can be stored as attachments. A first attachment is added as an attachment and further attachments are added using my_custom_field parameters
YADE will retrieve the contents of an attached file at run-time - intermediate or temporary files are not created when reading attachments. Note that attachments are specified in the KeePass GUI via the Advanced Edit Entry tab.
The next screenshot shows the configuration of the example Entry in the CS:
The following information was specified for the example in the database:
- Groups:
demo,ftp - Title:
demo_on_test.sos-berlin.com - User name:
demo - Password:
demo - URL:
test.sos-berlin.com(Alternatively, the IP address could have been specified here.)
Integrating the Credential Store in a File Transfer Configuration
The use of the Credential Store is specified in YADE Client file transfer configuration files, which are written in XML. We recommend using the SOS XML Editor to edit these files. Instructions for downloading, installing and using the XML Editor are linked from this page.
In the remainder of the current article, it is assumed that readers have made themselves familiar with the organization of the YADE Client file transfer configurations into Profiles and Fragments. This is described in The YADE Client Command Line Interface - Tutorial 1 - Getting Started article mentioned above.
The following example uses the XML configuration from the Getting Started article and adds the necessary configuration elements required to replace the "standard" authentication elements with elements stored in the Credential Store.
MP The following example uses the XML configuration from the Getting started article and move the sensetive information ( e.g. user name and password ) to the Credential Store.
The following XML configuration elements are required to specify the use of the Credential Store:
MP Please simplify this
The CredeitialStoreFragments element will have nececesery information (e.g. location of Credential store, access password etc.) required by YADE to retrrive the encrypted inforation.
Tehe CredetialStoreFragments can be referencesdy by ProtocolFragements to retrive and apply user and server information in the file transfer.
- A CredentialStoreFragments element at the same level in the XML hierarchy as the Protocol Fragments elements.
- This element can have one or more child Credential Store Fragment elements (described below).
- A CredentialStoreFragment element that is referenced from the ProtocolFragment. This Fragment specifies the location of and authentication required for the Credential Store.
- Password, key file and combined password/key file authentication methods are possible.
- A CredentialStoreFragmentRef element as a child element of the Protocol Fragment element - in the current example this is the FTPFragment.
- The values of the connection and authentication elements are modified to refer to elements stored within the Credential Store.
Addressing the Credential Store
Parameters stored in a Credential Store database Entry can be addressed in the CredentialStoreFragment XML element as follows:
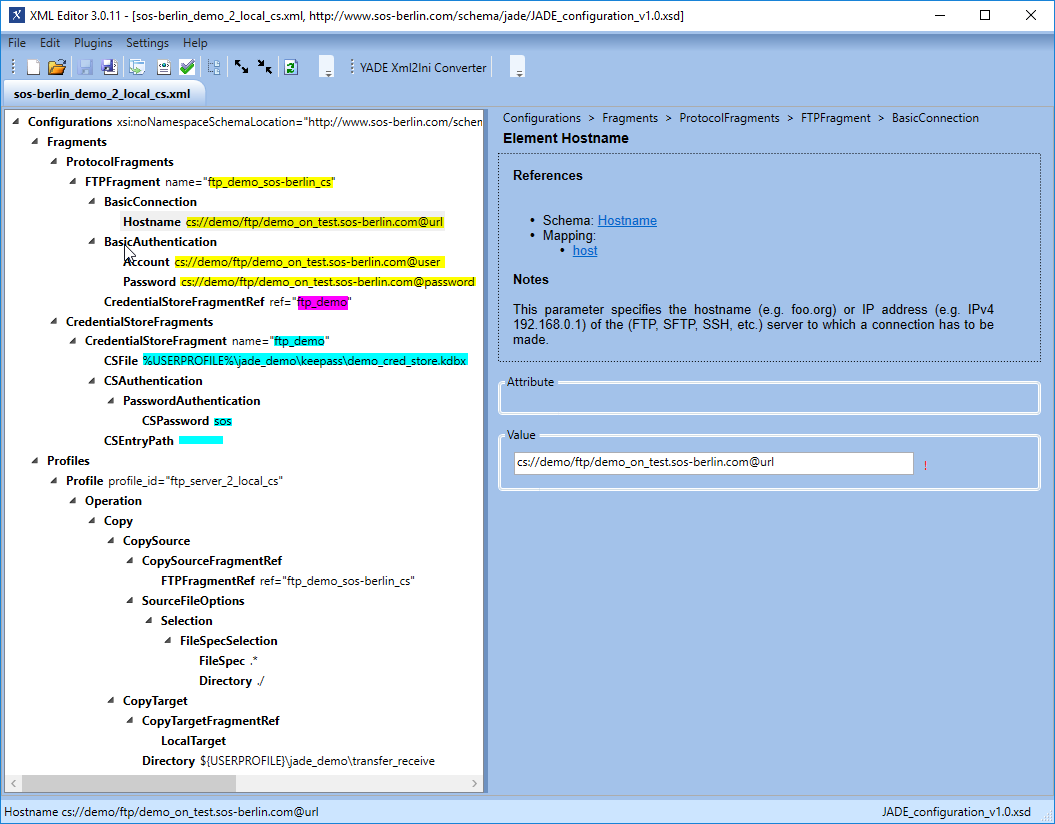
- The CSEntryPath element is used to specify the base path in the Credential Store database to the Entry. In the example this is set to:
demo/ftp/MP please change it to base pathdemo_on_test.sos-berlin.com
Wheredemoandftpare (optional) Group names, as specified above, anddemo_on_test.sos-berlin.comis the Title of the Entry.
The Credential Store Entry parameters are addressed using the following syntax:
- cs://@parameter_name, where the parameter_name is the name of the relevant parameter specified for the Entry.
The following parameters are set in the Credential Store in the current example:
- Hostname:
cs://@url(where@urlspecifies the URL element stored in the database ) - Account:
cs://@user@userspecifies the User name element stored in the database) - Password:
cs://@password@passwordspecifies the Password element stored in the database)
Note that a full list of parameters is described in the Adding an Entry to the Credential Store section above.
Alternative Syntax
Note also that although the CSEntryPath element is a required element, it can be left empty and that fully specified paths can be used for each parameter. For example, the Password could be specified using:
cs://demo/ftp/@passworddemo_on_test.sos-berlin.com
Configuration in the XML Editor
The parts of the XML configuration relevant to the use of the Credential Store are shown in the following screenshot of the configuration for the current example, with parameter values highlighted in yellow:
Running the YADE Client with the Credential Store
The use of the Credential Store is contained within the settings file and is not exposed when calling the YADE Client. For example, on Windows systems, the YADE Client is called for the current example using:
C:\Program Files\sos-berlin.com\jade\client\bin>jade.cmd -settings="%USERPROFILE%\jade_demo\sos-berlin_demo_2_local_cs.xml" -profile="ftp_server_2_local_cs"
The following listing shows the output produced by the example configuration. Note that the problem that occurred with the transfer of one of the files has nothing to do with the use of the Credential Store.
As with all YADE jobs, the number of successful file transfers can be seen in the log file.
See Also: